Introduction to Attribute-Based Access Control
Securing your data isn’t just important—it’s sometime life or death (specially when it comes to your text messages). Traditional access control methods often fall short in addressing the dynamic needs of modern organizations. That’s where Attribute-Based Access Control (ABAC) comes into play.
ABAC is a policy-based access control method that considers various attributes of users, actions, resources, and the environment when making access decisions. This allows you to implement more fine-grained access policies that adapt to changing contexts.
Imagin being able to grant access not just based on a user’s role, but also on their location, the time of day, or even the device they’re using. ABAC makes this possible by evaluating a multitude of attributes in real-time.
Why Traditional Access Control Methods Fall Short
Traditional access control models like Role-Based Access Control (RBAC) assign permissions based on roles assigned to users. While RBAC is straightforward and easy to implement, it can become cumbersome as the number of roles grows. It’s particularly challenging to accommodate dynamic access requirements that depend on context or specific attributes.
For instance, consider an organization where employees need access to sensitive data only during business hours and only from the office network. Implementing this policy using RBAC would require creating multiple roles or complex role hierarchies. As a result, you might face ‘role explosion,’ making the system harder to manage and increasing the risk of misconfigurations that could lead to security breaches.
Additionally, RBAC doesn’t easily support policies based on environmental factors or user attributes that can change frequently. In a world where remote work, flexible hours, and bring-your-own-device policies are becoming the norm, RBAC’s limitations become more pronounced.
How ABAC Works
ABAC uses attributes as the building blocks for access control decisions. These attributes can pertain to the user, the resource, the action, or the environment. The access control engine evaluates policies that define which attribute combinations grant or deny access.
For example, you can create a policy that allows access to a financial report only if the user is a manager in the finance department and is accessing the report from the corporate network during business hours.
Key Concepts of ABAC
- User Attributes: Information about the user, such as department, job title, security clearance, or group memberships.
- Resource Attributes: Characteristics of the resource being accessed, like its classification level, owner, or type.
- Action Attributes: The type of action being performed on the resource, such as read, write, delete, or approve.
- Environmental Attributes: Contextual information like time of day, location, IP address, or device type.
Policies in ABAC are constructed using these attributes in logical statements. They can be as simple or as complex as needed, providing a high level of flexibility and control.
Benefits of Implementing ABAC
Implementing ABAC offers several advantages:
- Dynamic Access Control: Access decisions adapt in real-time based on current attributes, reducing the need for manual updates.
- Reduced Adminstrative Overhead: Eliminates the need for managing an excessive number of roles, simplifying policy management.
- Enhanced Security: Provides fine-grained control, reducing the risk of unauthorized access and helping comply with regulatory requirements.
- Scalability: Easily accommodates new users, resources, and policies without significant reconfiguration, making it suitable for growing organizations.
With ABAC, you can create a more secure and efficient access control system that aligns with your organization’s specific needs.
Implementing ABAC with Keycloak
Keycloak is an open-source Identity and Access Management solution that supports ABAC through its Authorization Services. By leveraging Keycloak, you can implement ABAC in your applications without building the infrastructure from scratch.
Keycloak provides a comprehensive set of features for authentication, authorization, and management of user identities. Its Authorization Services support fine-grained authorization using both RBAC and ABAC models.
Enabling Authorization Services
To implement ABAC with Keycloak, you first need to enable authorization services for your client application:
1. Log into the Keycloak Admin Console.
2. Navigate to 'Clients' and select your client application.
3. Go to the 'Authorization' tab and enable the authorization settings (ensure that client authentication is also enabled).
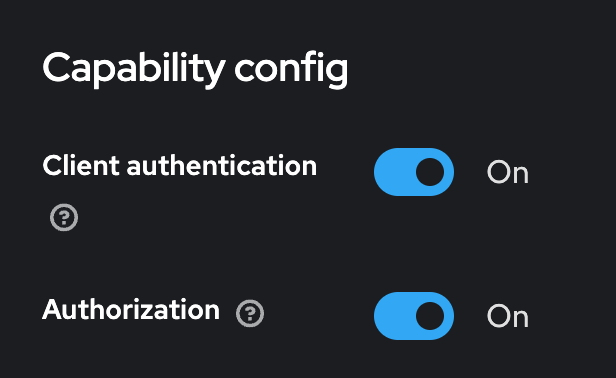
Enabling authorization services transforms your client into a resource server capable of handling authorization requests and decisions.
Defining Resources and Scopes
Next, define the resources and scopes that represent the protected assets and actions in your application:
1. In the 'Authorization' tab, click on 'Resources'.
2. Click 'Create' to add a new resource, such as 'Financial Report'.
3. Define scopes like 'view', 'edit', 'delete' to represent permissible actions on the resource.
Resources and scopes enable you to specify exactly what is being protected and what actions can be performed.
Creating Policies and Permissions
Now, create policies that use attributes to make access decisions:
1. Navigate to 'Policies' in the 'Authorization' tab.
2. Click 'Create' and select the policy type (e.g., 'User Attribute', 'JS', 'Time-based').
3. Define conditions based on attributes. For example, a 'User Attribute' policy that checks if 'department == finance' and 'role == manager'.
You can create complex policies using a combination of different policy types to match your specific requirements.
Then, link these policies to permissions:
1. Go to 'Permissions' in the 'Authorization' tab.
2. Click 'Create' to add a new permission.
3. Associate it with the desired resource (e.g., 'Financial Report') and scopes (e.g., 'view').
4. Assign the policy you created earlier to the permission.
This setup ensures that access to the resource is granted only when the policy conditions are met.
Example: Time-Based Access Control
Let’s consider an example where you want to allow access to a resource only during business hours:
1. Create a 'Time-based' policy.
2. Set the policy to allow access between 9 AM and 5 PM.
3. Assign this policy to the relevant permissions.
With this policy in place, users attempting to access the resource outside of business hours will be denied, enhancing security based on environmental attributes.
Best Practices for ABAC Implementation
To get the most out of ABAC, consider the following best practices:
- Define Clear Policies: Ensure that your access control policies are well-defined, documented, and understood by all stakeholders. Ambiguous policies can lead to unintended access being granted or denied.
- Regularly Update Attributes: Keep user and resource attributes up-to-date. Outdated attributes can result in incorrect access decisions, potentially exposing sensitive data.
- Monitor and Audit: Use Keycloak’s built-in monitoring tools to track access patterns and identify anomalies. Regular audits help ensure that the access control system is functioning as intended.
- Least Privilege Principle: Grant users the minimal level of access required to perform their duties. This reduces the attack surface and limits potential damage from compromised accounts.
- Test Policies Thoroughly: Before deploying policies in a production environment, test them extensively to ensure they work as expected under various scenarios.
- Educate Users: Make sure users understand how attributes affect their access. This awareness can help them comply with organizational policies and reduce friction.
Following these best practices will help you maximize the benefits of ABAC while minimizing potential risks.
Conclusion
Attribute-Based Access Control offers a smarter way to secure your data by considering a wide range of attributes in access decisions. By implementing ABAC with Keycloak, you can enhance your security posture while reducing administrative overhead.
With the ability to create dynamic, context-aware policies, ABAC helps you address the complexities of modern access control requirements. Whether you’re dealing with remote workers, regulatory compliance, or simply trying to streamline your access management, ABAC provides the flexibility you need.
Ready to take your access control to the next level? Learn more about Keycloak’s authorization services in their Authorization Services Guide.
Thinking about self-hosting Keycloak? Discover the costs and considerations before you make a decision.
If you’re looking for a managed Keycloak solution with additional enterprise features, check out our pricing plans at Skycloak. Don’t miss out on securing your data smater! 🚀