Explore Insights on Identity and Access Management (IAM)
Discover expert tips, best practices, and in-depth guides to simplify and secure your IAM strategy. Search through our blogs to find something you need.
Popular categories
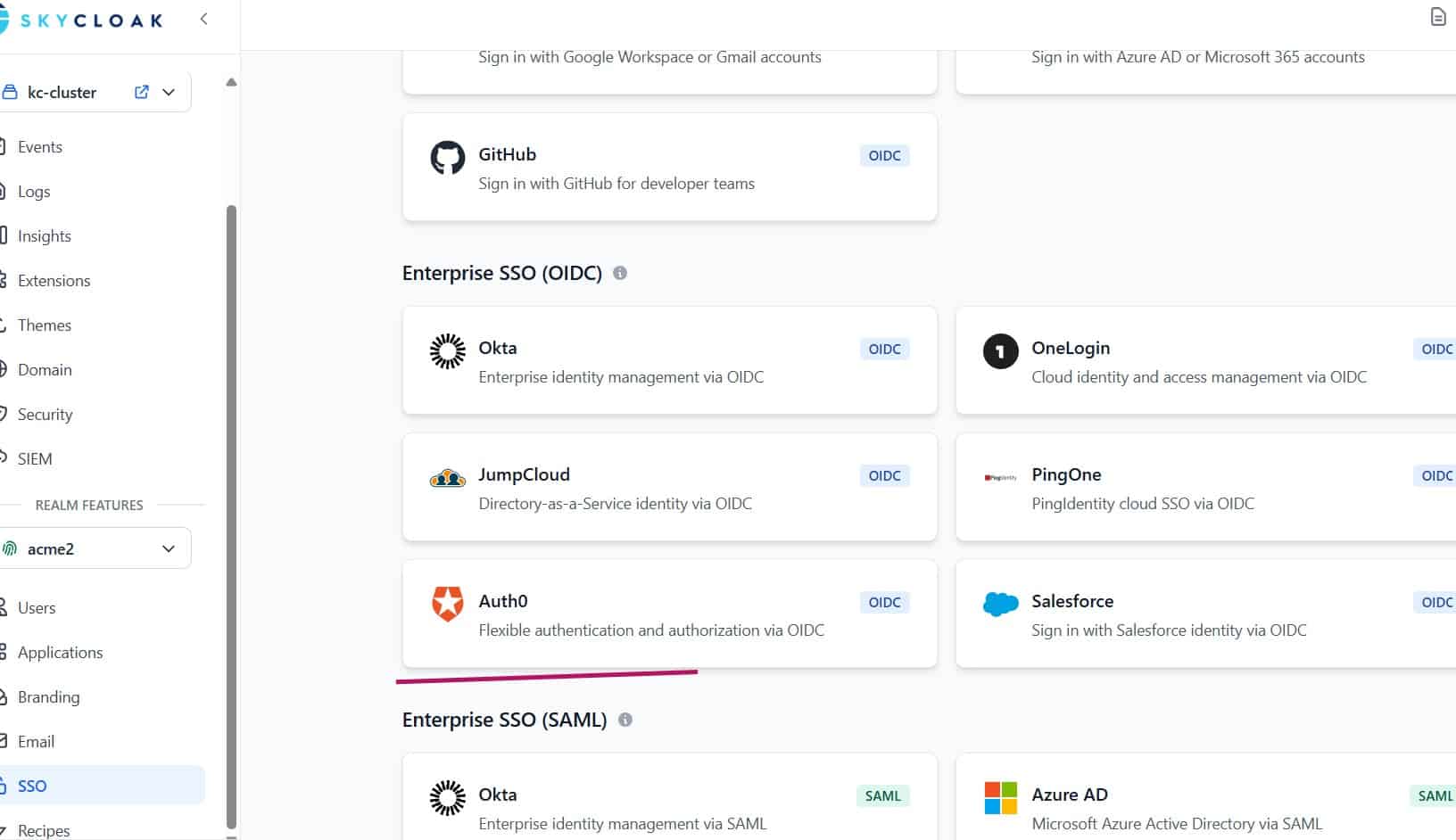
Integrating Keycloak with Auth0 Using Skycloak SSO Templates
Learn how to configure Keycloak Identity Brokering with Auth0 using Skycloak Console’s SSO templates in a simple, production-ready way...
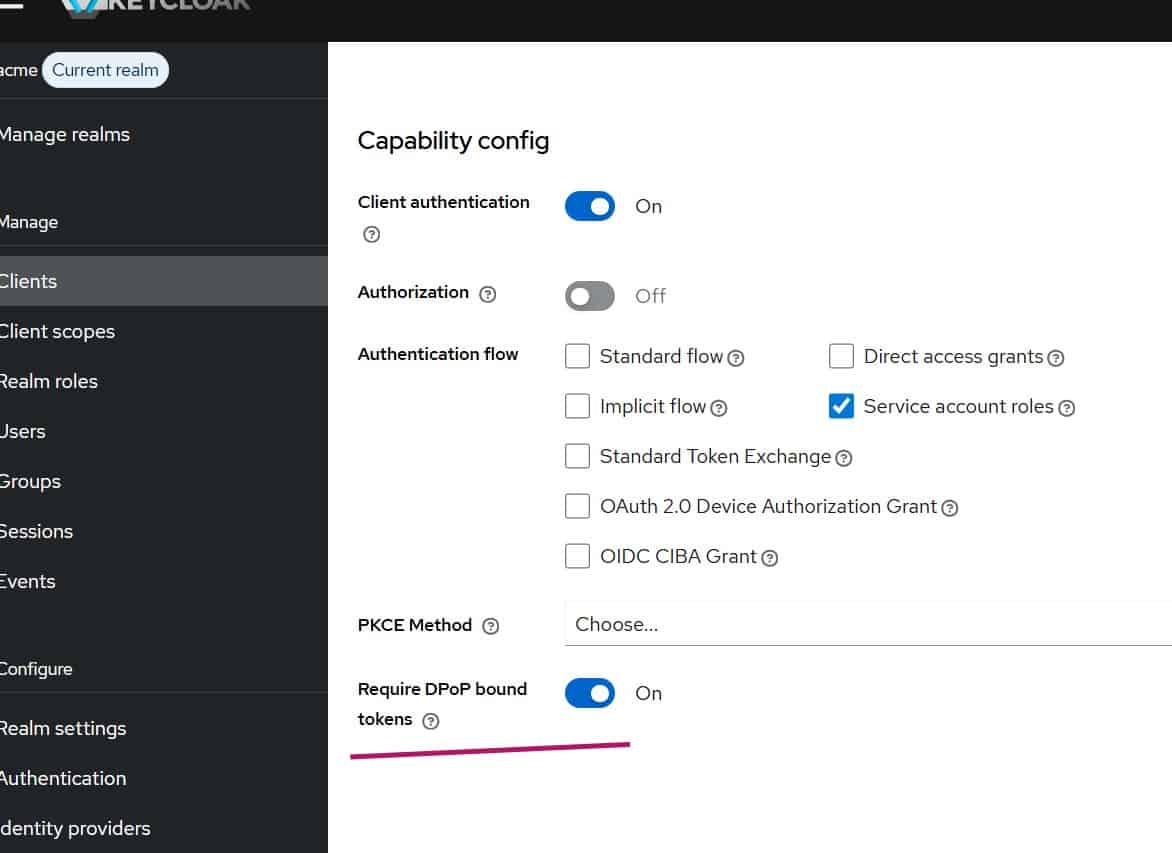
Read More...DPoP with Keycloak Admin API Using Node.js
Learn how to implement DPoP with Keycloak Admin API using Node.js, including token binding, CNF validation, and real-world tips...
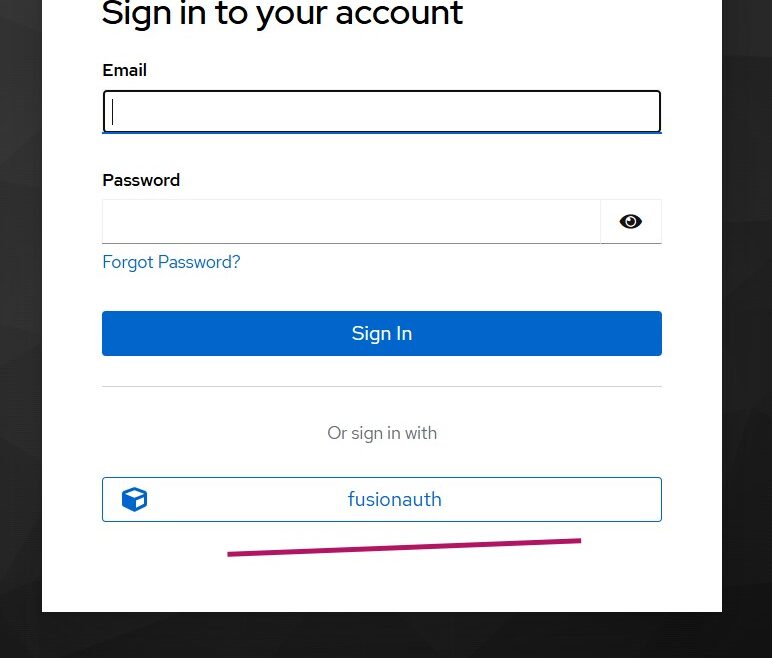
Read More...Keycloak Identity Brokering with FusionAuth
Learn how to configure FusionAuth as an OIDC identity provider for Keycloak using identity brokering with step-by-step setup and testing guide...
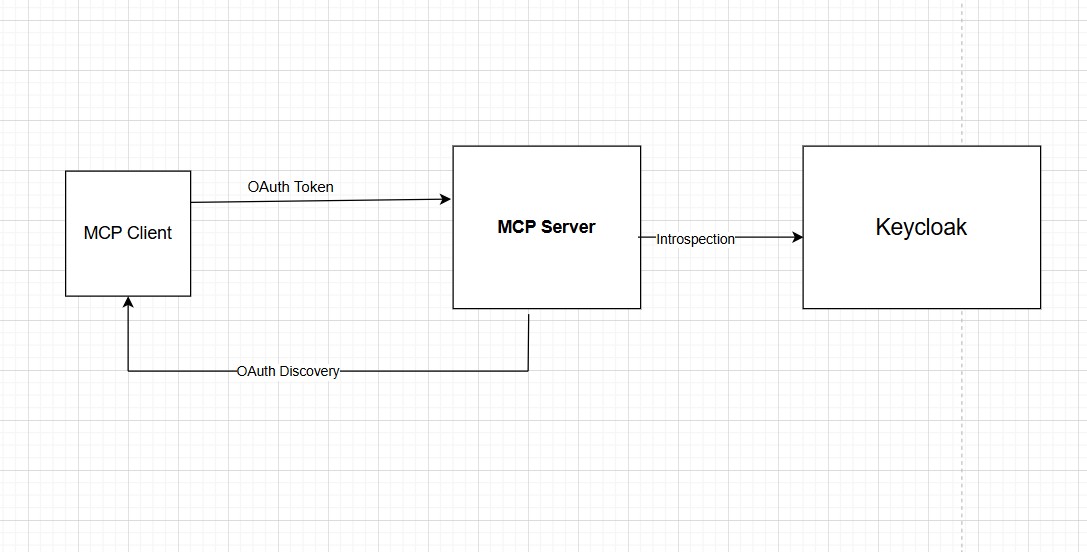
Read More...Securing MCP Servers with Keycloak OAuth 2.0
Learn how to secure a Model Context Protocol (MCP) server using Keycloak OAuth 2.0, token introspection, and audience validation...
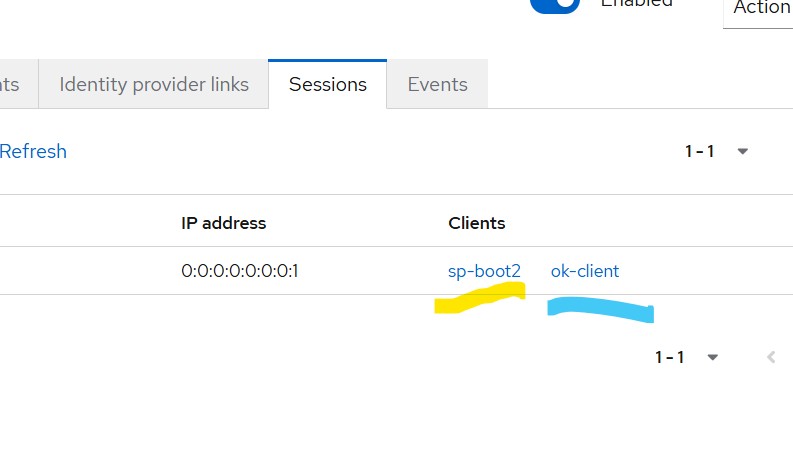
Read More...Migrating from Legacy Keycloak Spring Boot Adapters
Learn how to migrate from legacy Keycloak Spring Boot adapters to native Spring Security OAuth2/OIDC for Keycloak 25+ and Spring Boot 3...
Read More...Bridging IdP-Initiated SAML to OIDC with Keycloak
Learn how to enable OIDC application access using an IdP-initiated SAML flow with Auth0 as IdP and Keycloak as the service provider...
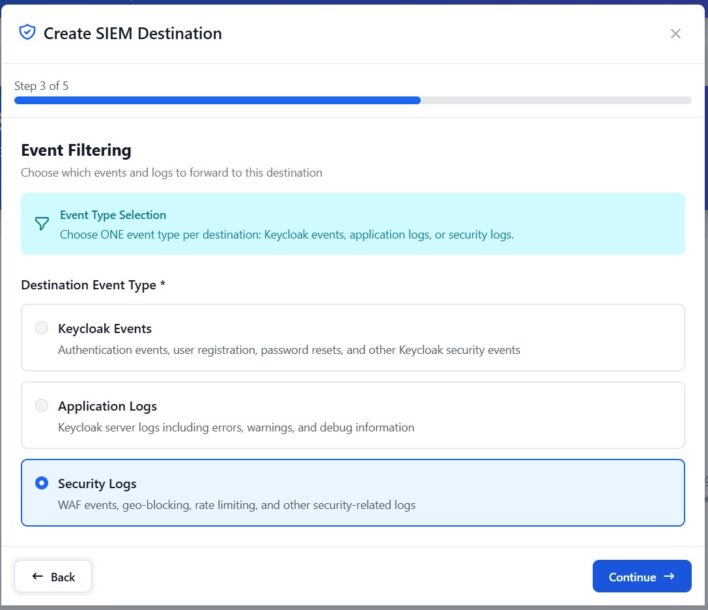
Read More...Integrating Skycloak Security Logs Using Syslog
Learn how to configure Skycloak to send security logs via Syslog to rsyslog and integrate with SIEM platforms like Elastic Stack...
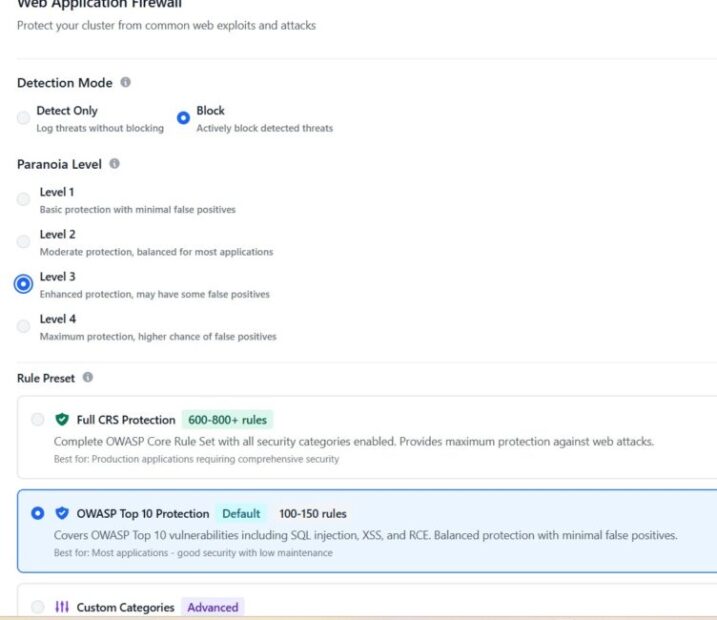
Read More...Securing Keycloak with Skycloak’s Configurable WAF
Learn how to secure your Keycloak cluster using Skycloak’s configurable WAF with OWASP Top 10 protection, paranoia levels, and real-world testing...
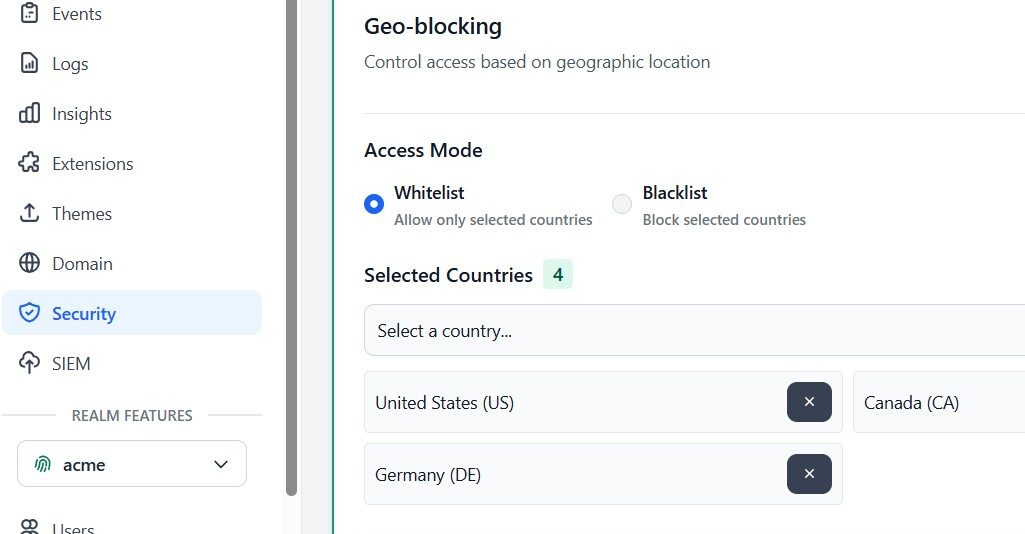
Read More...Geo-blocking Your Keycloak cluster using Skycloak
Enable Geo-blocking in Skycloak to restrict access to your Keycloak cluster by country and enhance security with simple configuration...
Read More...