Introduction
After watching enough hacker movies and series, securing your resources gets more critical than ever (of course, when the budget and priorities allows it 😉). Access control strategies like Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) are great solutions to protect your data, and it can be implemented fast and easily. In this post, we’ll explore these strategies and show you how you can implement them now using tools like Keycloak.
Understanding Access Management
Access management is the process of controlling who has acess to resources in your system. By implementing an access control strategy, you ensure that only authorized users can access certain information, reducing the risk of data breaches and unauthorized activities.
In the modern enterprise environment, where employees, partners, and customers interact with your systems, it would be ridiculous not to have some sort of access management in place. Poor or no access control can lead to unauthorized data exposure, compliance violations, and financial losses.
The Importance of Access Control
Access control is crucial for protecting your digital assets. It helps prevent unauthorized access, ensures compliance with regulations, and protects your company’s reputation. Without proper access control, your business is vulnerable to various security threats.
Access control is not just about keeping unauthorized users out; it’s about ensuring that the right users have the right access at the right time. Well designed access control helps you comply with industry regulations like GDPR, HIPAA, and others. It also enhances user productivity by providing the right access to necessary resources.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a strategy where permissions are assigned to roles, and users are assigned to these roles. This simplifies access management by grouping permissions into roles that mirror your organization’s structure.
RBAC is widely adopted because it simplifies permission management. With RBAC, you can easily onboard new employees by assigning them to appropriate roles, and when someone changes positions, you simply update their role assignment. This reduces administrative overhead and minimizes errors compared to managing permissions on a per-user basis.
For instance, consider the following roles and their permissions:
| Role | Permissions |
|---|---|
| Admin | Full access to all resources |
| Manager | Access to team reports, manage team members |
| User | Access to own profile and tasks |
You can easily see that each role has a similar function to in a team or department. The closer it is to the actual meaning, the easier it will be to onboard new users.
Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) takes a more dynamic approach by assigning access based on attributes of users, resources, and the environment. This allows for more granular and flexible access control policies.
ABAC considers multiple attributes like user role, department, resource sensitivity, and even environmental contexts like time or location. This approach enables you to define complex access control policies that can adapt to changing contexts and requirements.
For example, you can set a policy that allows managers to approve expenses only during business hours and only when they are connected from the company’s network. This granularity provides top of shelf security and aligns access policies closely with business requirements.
An example ABAC policy might look like:
if user.role == 'Manager' and resource.type == 'ExpenseReport' and env.time >= '09:00' and env.time <= '17:00' and env.location == 'CorporateNetwork' then allowImplementing Access Control with Keycloak
Keycloak is an open-source Identity and Access Management (IAM) solution that makes it easy to implement RBAC and ABAC in your applications. With Keycloak, you can manage users, roles, and permissions through an intuitive admin console.
Let’s look at how you can get started with Keycloak to implement these access control strategies.
Getting Started with Keycloak
To start using Keycloak, you can deploy it using Docker. If you prefer deploying Keycloak yourself, here’s how you can run it using Docker:
docker run -e KC_BOOTSTRAP_ADMIN_USERNAME=admin -e KC_BOOTSTRAP_ADMIN_PASSWORD=admin -p 8080:8080 keycloak/keycloak:26.0.7 start-devFor more customizable deployments, you might want to use a docker-compose file. You can generate one using the Skycloak Docker-compose generator.
If you’re looking to save time on setup and maintenance, we offer Keycloak managed as a service.
Configuring RBAC in Keycloak
In Keycloak, you can define roles at the realm or client level. To create a role:
- Login to the Keycloak admin console.
- Navigate to Realm roles and click Create Role.
- Enter the role name and save.
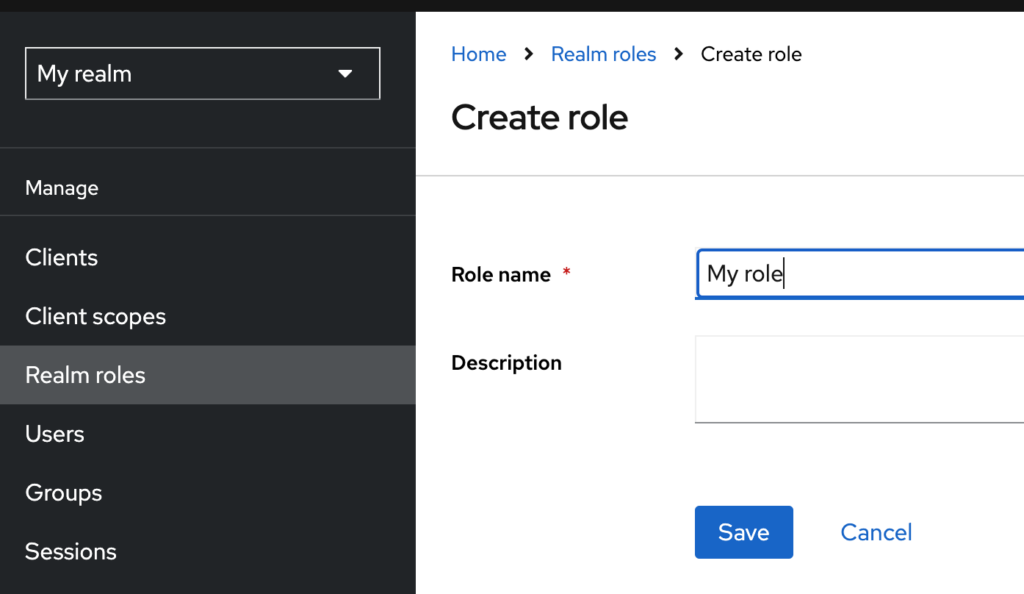
Be aware that if you add attributes to the role, it will not automatically be passed to users assigned to that role. See this for source.
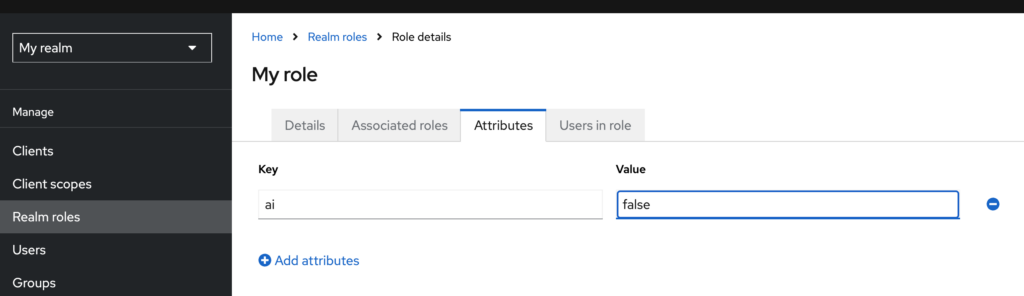
Next, assign this role to users:
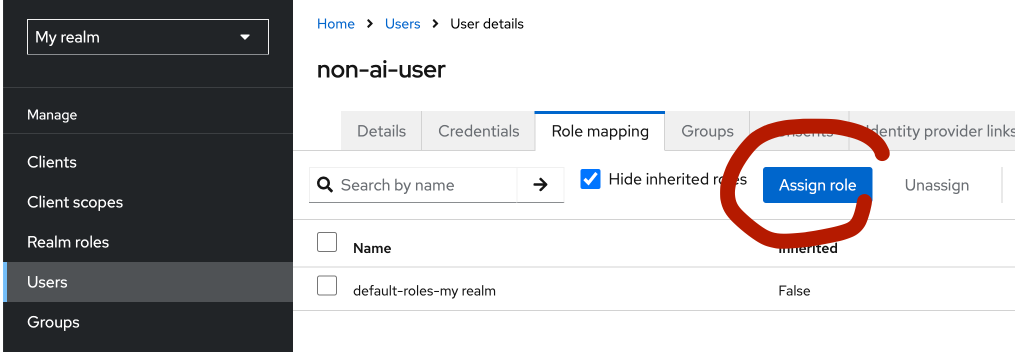
- Go to Users and select a user.
- Under the Role Mappings tab.
- Click Assign role.
- Filter by realm role and select your role
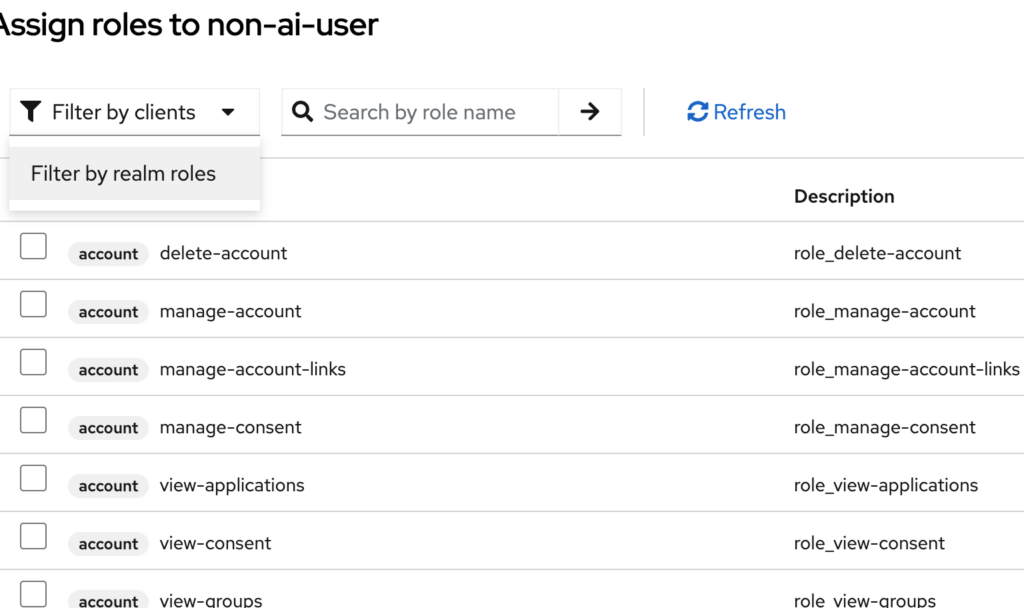
Now, your application can check for these roles to grant or deny access to resources. Here’s an example of checking a user’s role in code:
if (user.hasRole('Manager')) {
// Allow access
}Configuring ABAC in Keycloak
Keycloak supports ABAC through its authorization services. You can define policies based on user attributes, resource attributes, and more.
To configure ABAC:
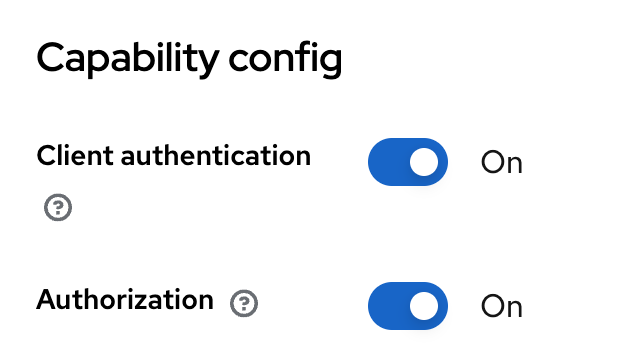
- Enable Authorization on your client settings.
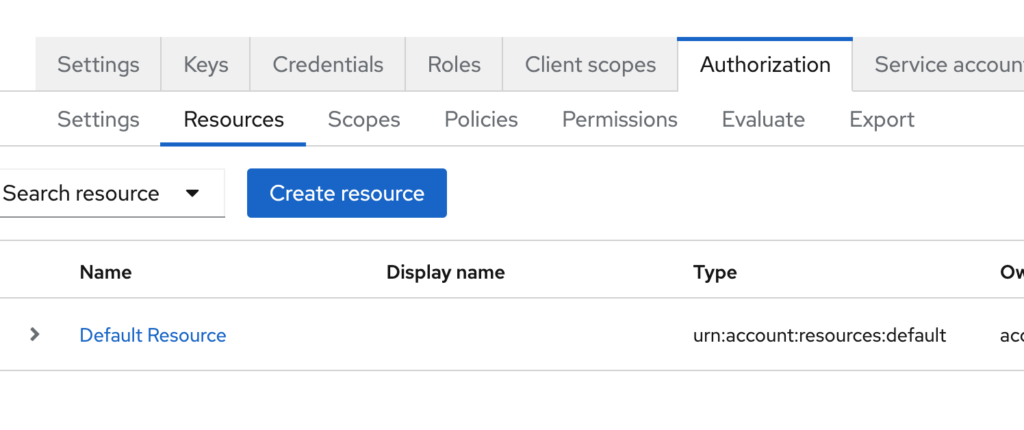
- Define resources and scopes under the Authorization tab.
- Create policies based on attributes.
- Create permissions that tie resources, scopes, and policies together.
Here’s an example of a policy definition in Keycloak:
{
"type": "js",
"code": "if ($evaluation.context.identity.getAttributes()['department'][0] == $evaluation.resource.attributes['department'][0]) {
$evaluation.grant();
}"
}By leveraging Keycloak’s features, you can implement complex access control mechanisms without reinventing the wheel. Additionally, Keycloak supports integrations with various databases and LDAP servers, allowing you to connect it with your existing user directories.
A more completed guide will eventually be available on the documentation page.
