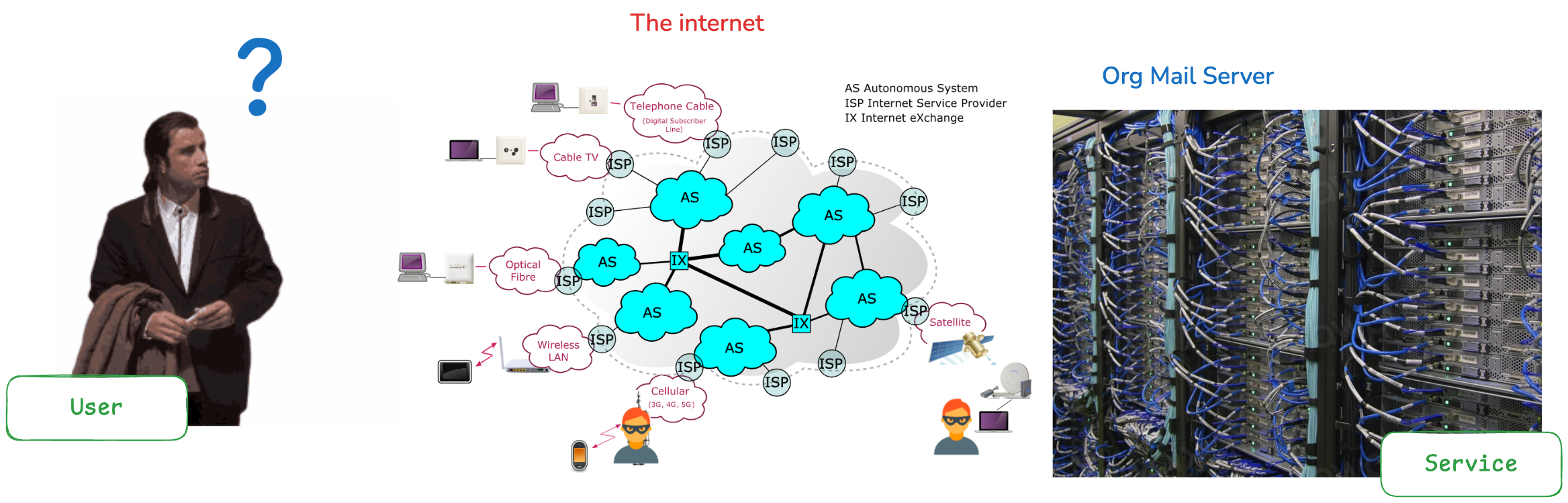
Introduction
With cyber threats lurking around every corner, having a robust authentication system is essential. Specially when login in your bank account from that new coffee shop in town. Today, we will take a look at Kerberos authentication—a network’s sheild that provides identity verification and protects your assets/resources from unauthorized access.
What is Kerberos Authentication?
Kerberos is a network authentication protocol designed to provide strong authentication for client/server applications by using secret-key cryptography. Developed at MIT in the 1980s, Kerberos has become a standard in network authentication nowadays. Named after the mythical three-headed dog guarding the gates of Hades, Kerberos guards your network by allowing secure authentication over non-secure networks. That’s pretty much the key detail to remember: over unsecured networks.
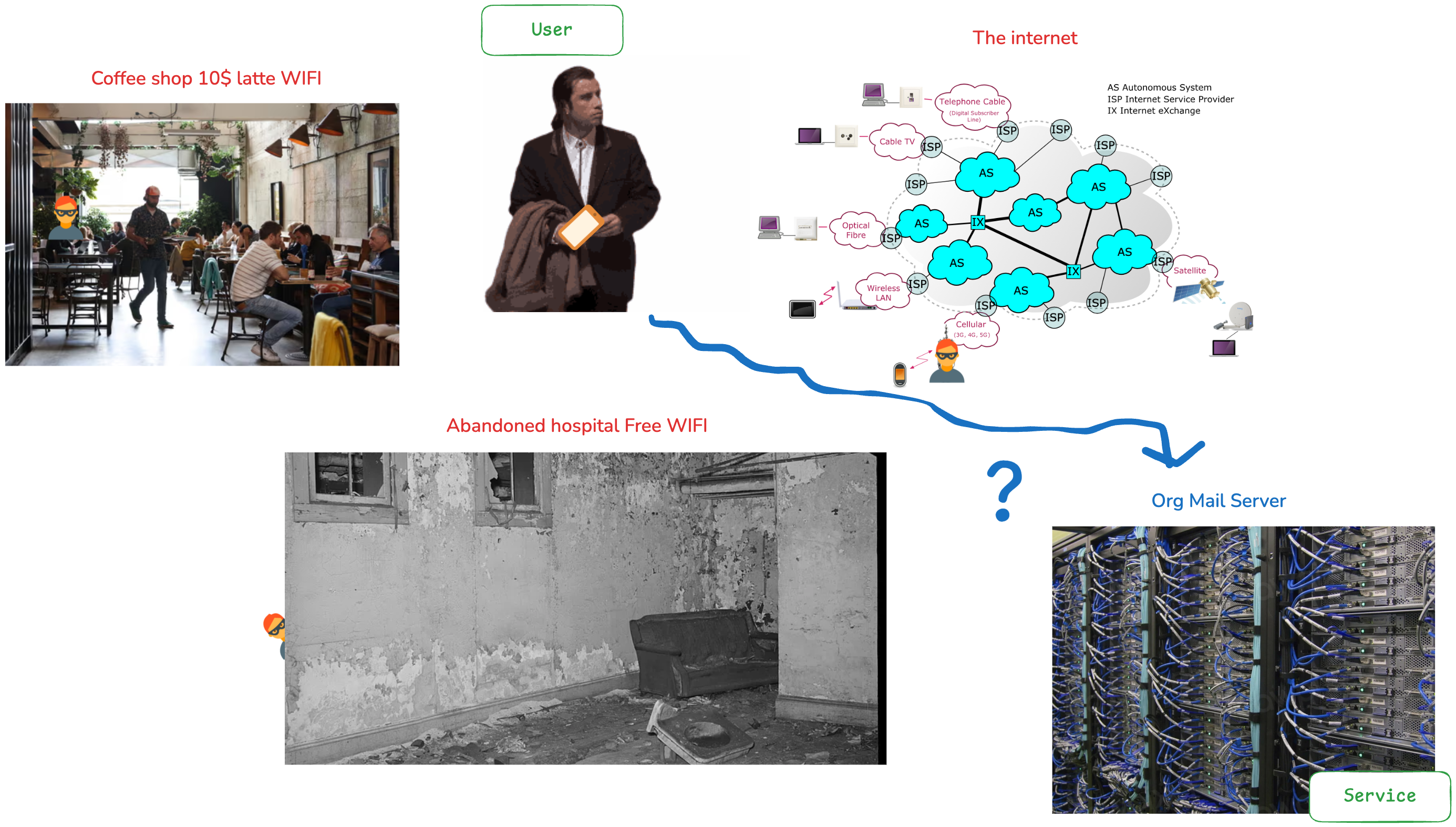
It enables secure identity verification across those networks, ensuring that sensitive data remains protected. By preventing passwords from being sent over the network, Kerberos minimizes the risk of interception and unauthorized access. Look at John for example below. Do you think it’s a good idea for him to access his organization’s mail server from those 3 options?
How Does Kerberos Work?
At its core, Kerberos uses a trusted third-party called the Key Distribution Center (KDC) to authenticate users and services. A Kerberos server is often called the KDC as well. When you log in, Kerberos grants you a ticket that allows you to access various services without re-entering your credentials. This ticket-based system minimizes the risk of password interception and enhances security. See it like when going to an event and you get that stamp on your wrist that is quite hard to wash.
The process:
- Initial Authentication Request: You enter your login credentials, which are sent to the KDC. The credentials are encrypted, ensuring they are not exposed during transmission.
- Ticket Granting Ticket (TGT) Issuance: Upon successful authentication, the KDC issues a TGT to you. This ticket is encrypted and can be used to request access to multiple services without re-authenticating.
- Service Ticket Request: When you try to access a specific service, you present the TGT to the KDC to obtain a service ticket for that service.
- Service Access Granted: You present the service ticket to the service server, which verifies it with the KDC. Once validated, you’re granted access.
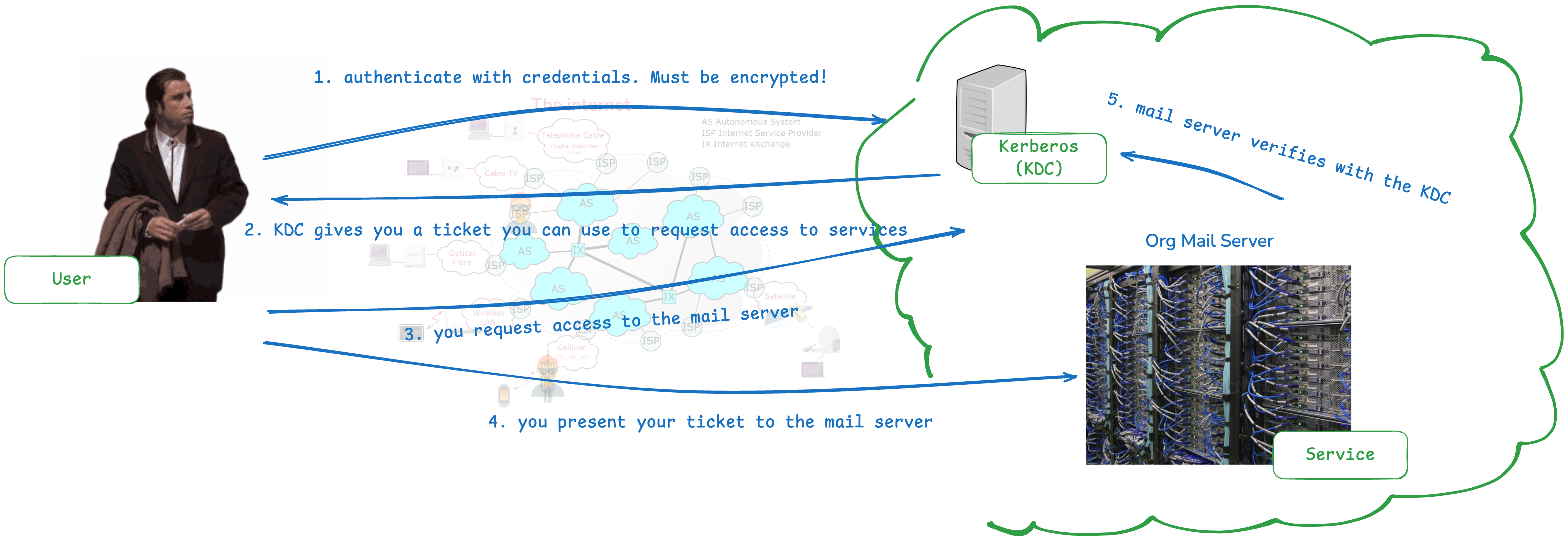
This process ensures that passwords are never sent over the network after the initial authentication, reducing the risk of interception or replay attacks.
Benefits of Using Kerberos
Kerberos offers numerous advantages:
- Enhanced Security: Passwords are never sent over the network, reducing the risk of interception.
- Single Sign-On (SSO): You authenticate once and gain access to multiple services without repeated logins.
- Mutual Authentication: Both you and the service verify each other’s identity, preventing man-in-the-middle attacks.
On top of it all, Kerberos helps reduce maintenance overhead by centralizing authentication, and its compatibility with various operating systems and applications makes it a versatile choice for organizations of all sizes.
Kerberos also supports mutual authentication, where both the client and the server verify each other’s identity. This is crucial in preventing attacks where a malicious bob impersonates a server to steal your credentials.
Moreover, Kerberos is scalable and can handle a large number of authentication requests, making it a good case for enterprise environments.
Conclusion
Kerberos authentication offers robust protection against unauthorized access. By integrating Kerberos with platforms like Keycloak, you can enhance your security posture while providing a smooth user experience. Stay tuned as we make available a step by step guide on how to integrate Keycloak with a Kerberos server.