Explore Insights on Identity and Access Management (IAM)
Discover expert tips, best practices, and in-depth guides to simplify and secure your IAM strategy. Search through our blogs to find something you need.
Popular categories
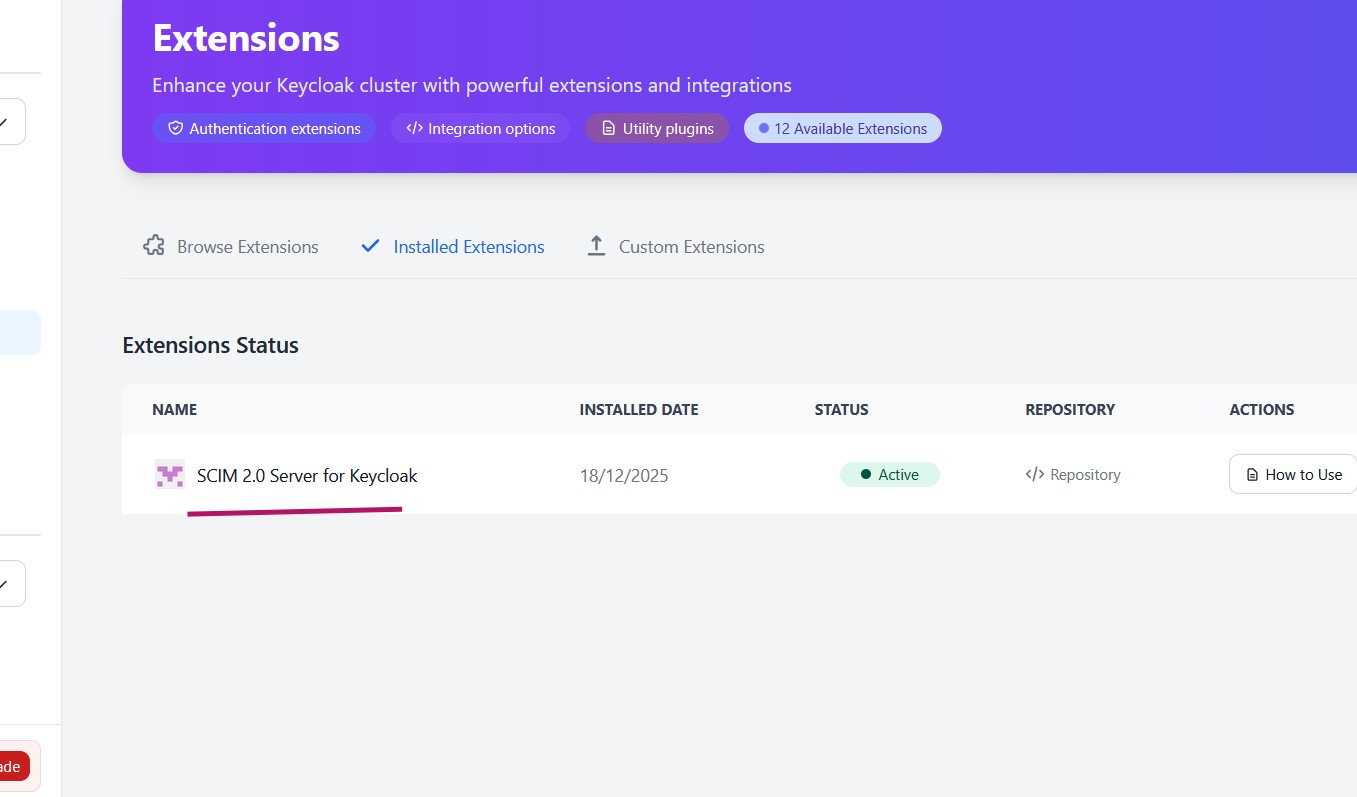
Using SCIM 2.0 with Skycloak (Managed Keycloak)
Learn how to configure SCIM 2.0 in Keycloak using Skycloak with external JWT authentication and test user provisioning via Postman...
Read More...Secure React API Access Using Keycloak (OIDC + PKCE)
Learn how a React app securely accesses Spring Boot APIs using Keycloak, OpenID Connect Authorization Code Flow, and PKCE...
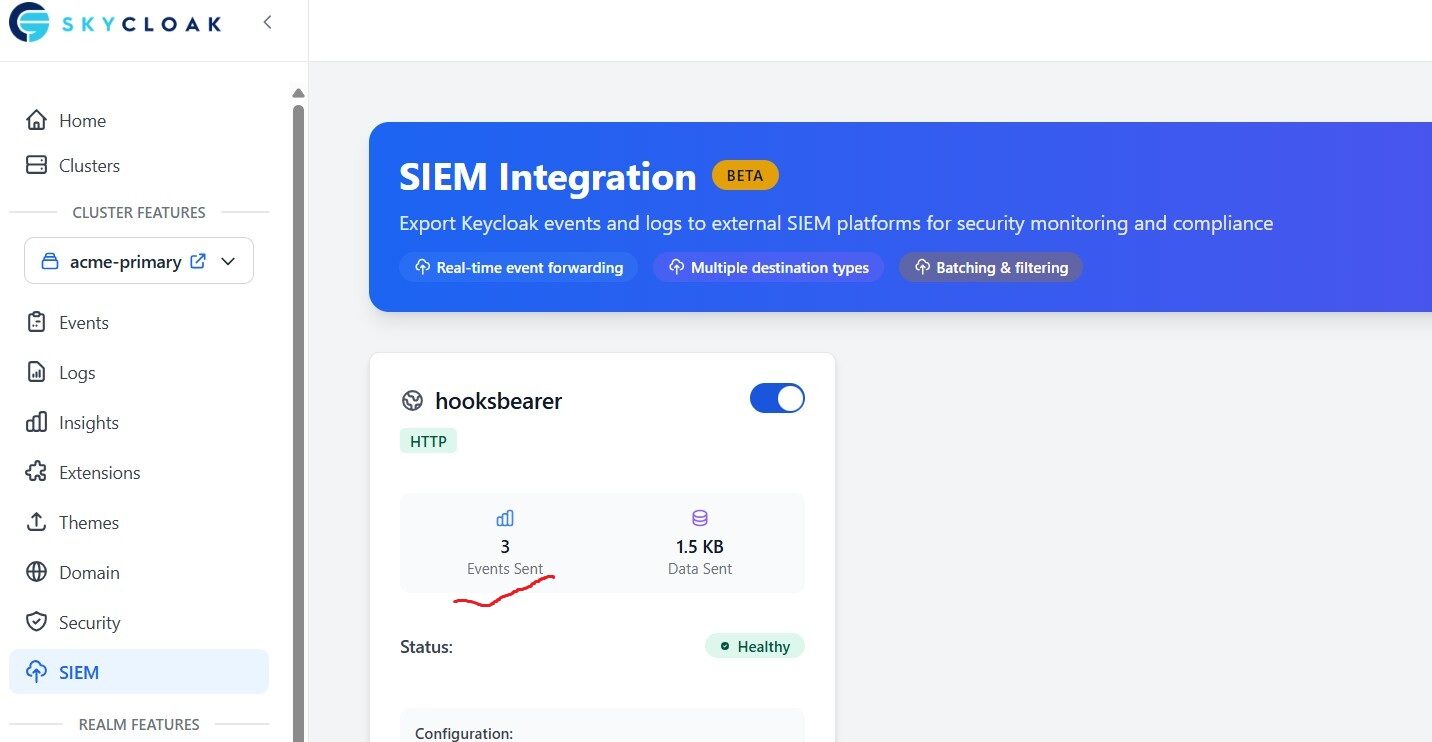
Read More...Forward Keycloak Events to SIEM via Skycloak HTTP Webhook
Learn how to send Keycloak authentication events, server logs, and security telemetry to your SIEM using Skycloak HTTP-hooks for centralized monitoring...
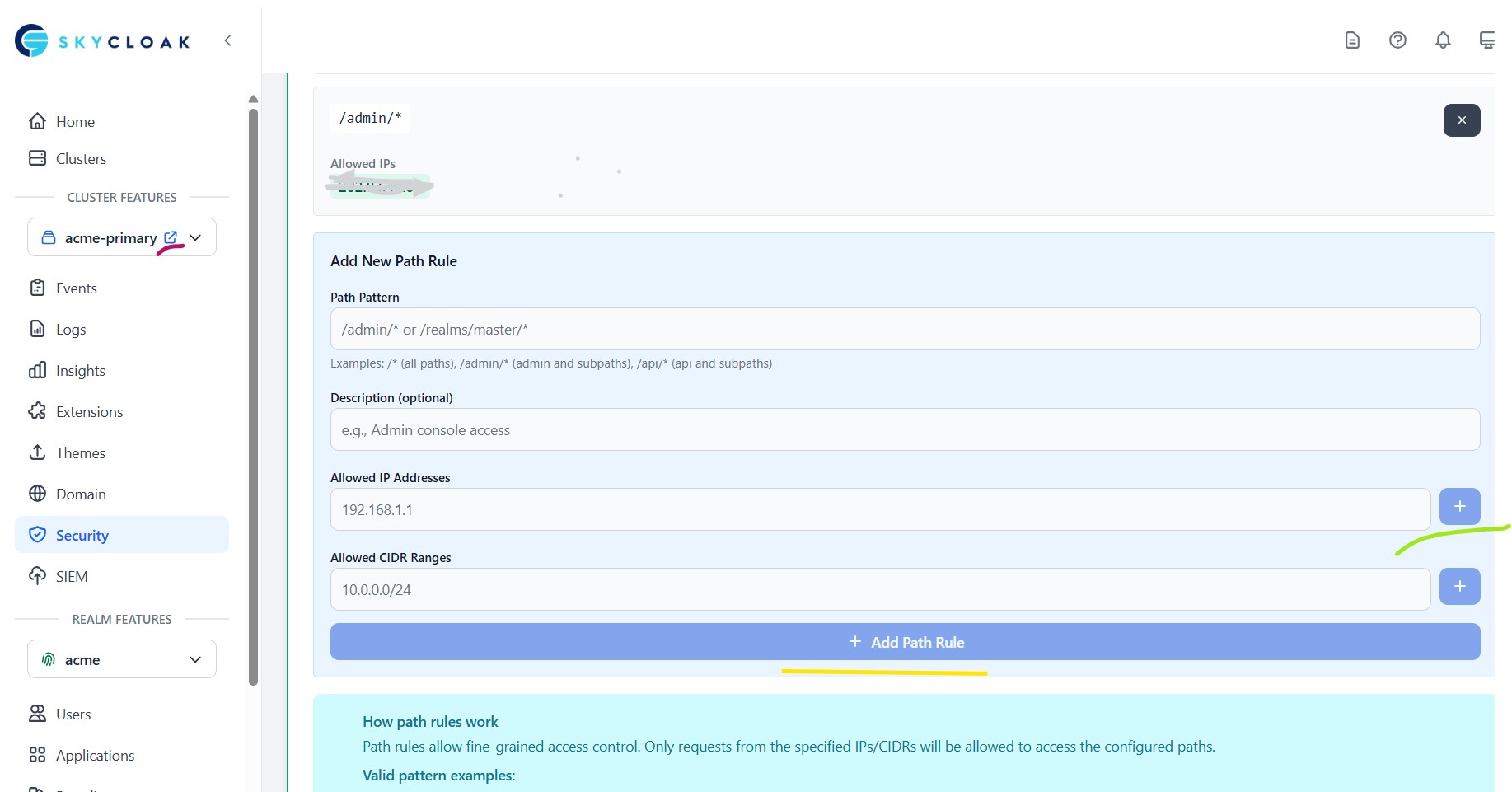
Read More...Path-Based IP Restriction for Keycloak Admin Console
Restrict Keycloak admin console access using IP/CIDR whitelisting on Skycloak. Secure your /admin/* path with path-based IP rules...
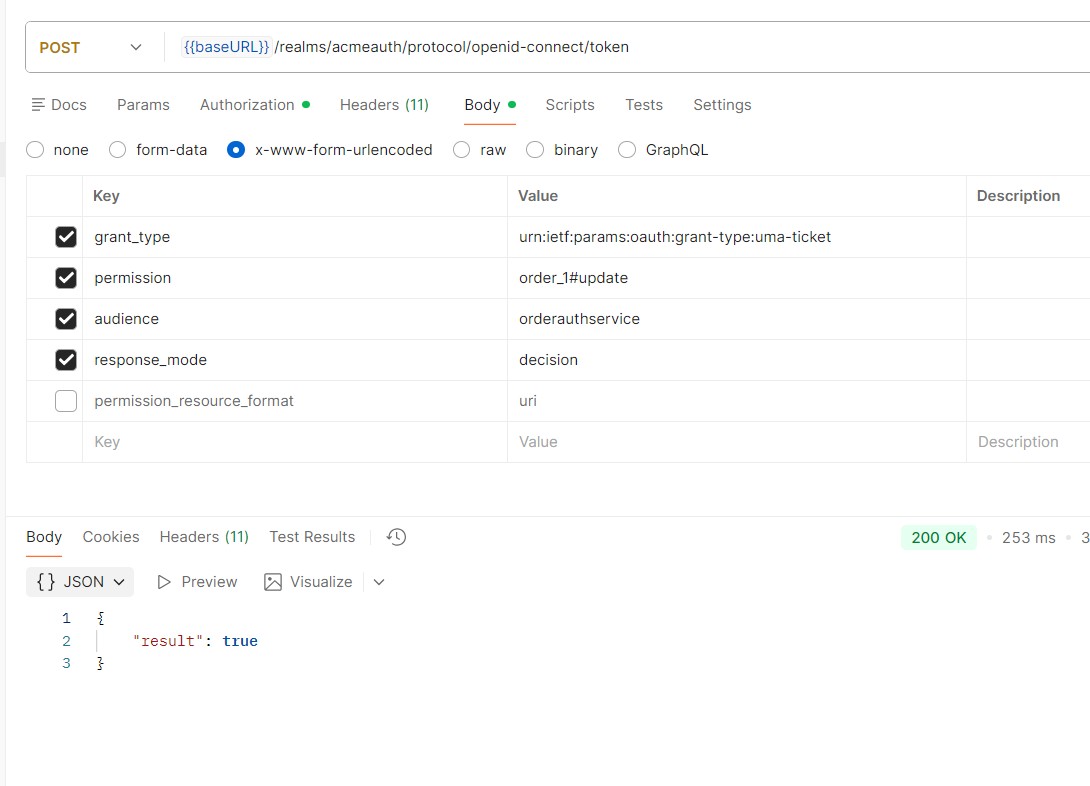
Read More...Fine-grained authorization in Keycloak Explained
Understand how Keycloak evaluates permissions with UMA, policies, scopes, and RPT or JSON-based decisions for secure resource access...
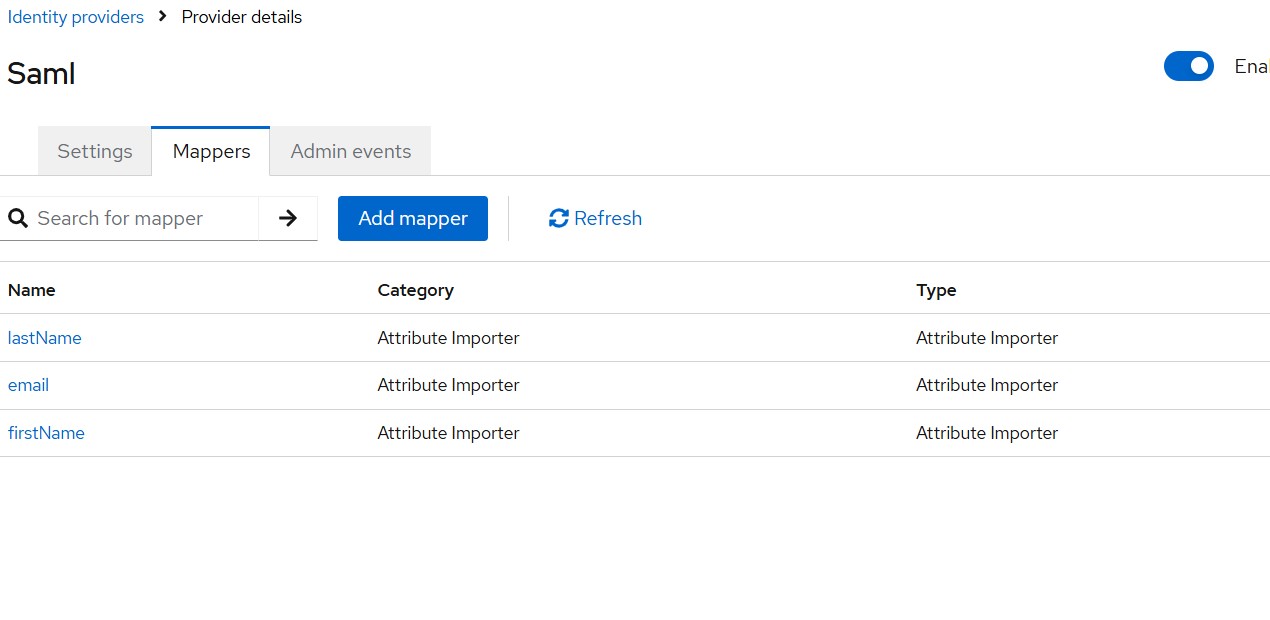
Read More...Attribute Mapping when using Keycloak as a SAML SP
Learn how to map user attributes sent via SAML into Keycloak, including email, firstName, and lastName, when using an external identity provider...
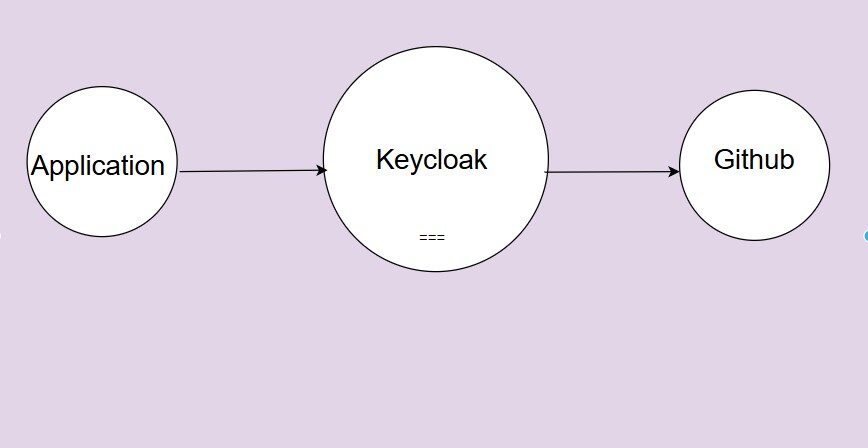
Read More...Using Keycloak Identity Brokering to Add GitHub Social Login
Learn how to integrate GitHub login using Keycloak’s Identity Brokering feature with Skycloak, enabling seamless social authentication for your applications...
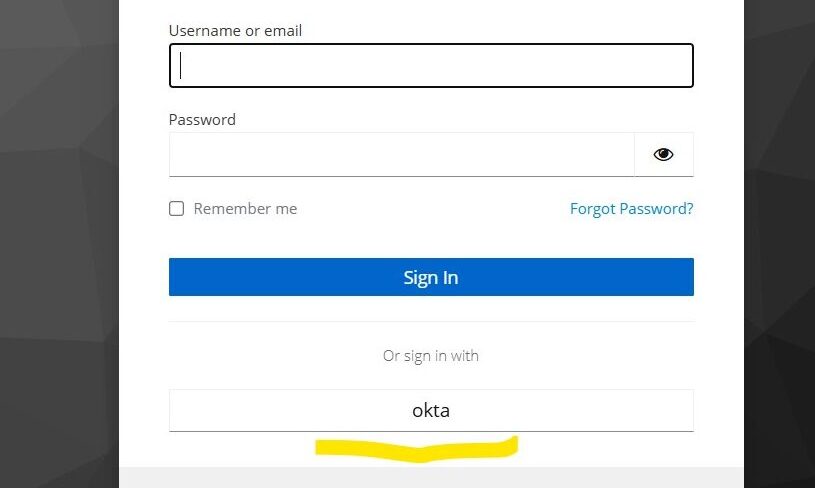
Read More...Configuring Keycloak as a SAML Service Provider
Set up Okta as a SAML Identity Provider and Keycloak as a SAML Service Provider using Identity Brokering. Step-by-step guide for seamless SSO integration...
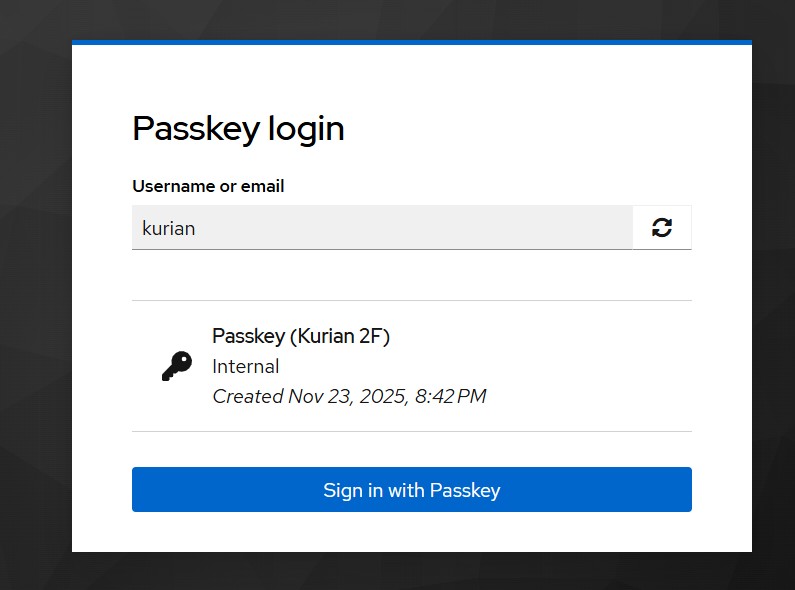
Read More...Keycloak WebAuthn: Enabling Passkeys for 2FA
Learn how to configure and use passkeys as a second-factor authentication method in Keycloak, building on the earlier setup for passwordless login...
Read More...