Introduction
Ever wondered why some passwords stay secure even after relentless hacking attempts? In the ever-changing field of cybersecurity, protecting user credentials is paramount. See for yourself on the amount of breach occurs every day! Bcrypt has been a stalwart in password hashing, ensuring that even if attackers breach your database, your users’ passwords remain indecipherable.
While new contenders like Argon2 have entered the fray, bcrypt continues to be a trusted choice for developers and security professionals alike. This guide delves into the basics of bcrypt, exploring why it remains a preferred algorithm for password hashing. We’ll provide actionable insights, real-world examples, and best practices to enhance your authentication systems. Let’s dive in!
Understanding Bcrypt: The Basics
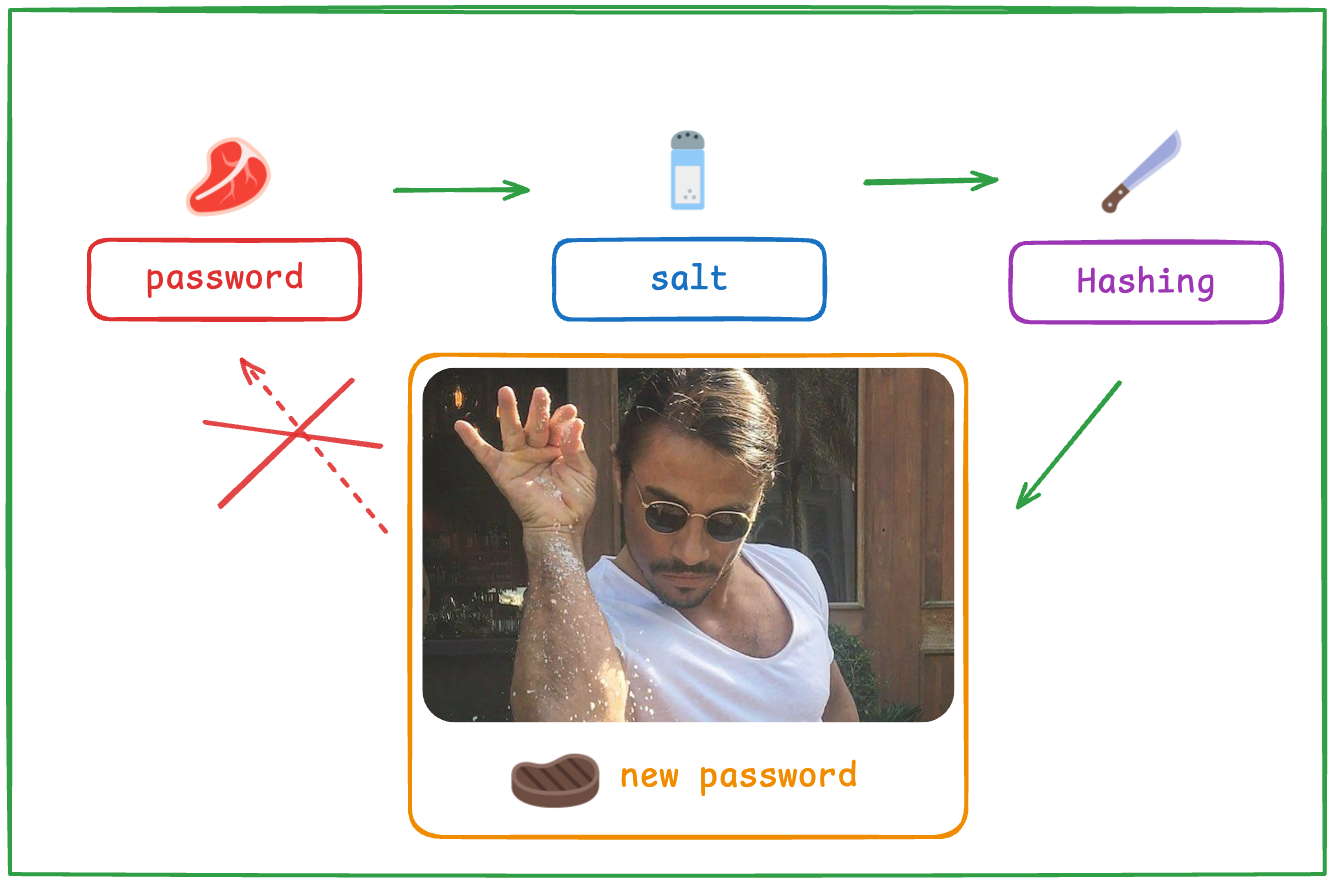
Bcrypt is a password hashing function designed to be computationally intensive, making it resistant to brute-force attacks. It’s based on the Blowfish cipher and incorporates a salt to protect against rainbow table attacks.
The algorithm is adaptive, meaning you can increase the iteration count (work factor) over time to compensate for increased hardware speed, ensuring sustained security.
How Bcrypt Works

Bcrypt takes your plain-text password and a salt as input. It then applies the EksBlowfish algorithm, a variant of the Blowfish cipher, repeatedly based on the defined work factor. The result is a hash that is unique to the input password and salt.
The use of the salt ensures that identical passwords will have different hashes, and the computational intensity of the algorithm slows down attackers attempting to guess passwords through brute-force methods.
The Importance of Salting
Salting adds random data to the input of a hashing function. In bcrypt, the salt is a crucial component that guards against rainbow table attacks, where attackers use precomputed tables to reverse hashes.
By using a unique salt for each password, bcrypt ensures that even identical passwords will produce different hashes. This means an attacker cannot use precomputed hashes to attack your system.
Why Bcrypt is Preferred for Password Hashing
Bcrypt has stood the test of time due to its robust security features and adaptability. Its design makes it exceptionally resistant to various attack vectors commonly exploited in password cracking.
The algorithm’s ability to adjust its computational cost means that it can remain secure even as computing power increases, a feature not present in simpler hashing algorithms.
Security Features of Bcrypt
Bcrypt’s primary security feature is its adaptive hash function. By increasing the work factor, you can make the hashing process more computationally intensive, slowing down attackers without affecting user experience significantly.
Additionally, the inclusion of a salt protects against rainbow table attacks, and the algorithm’s resistance to GPU acceleration makes it harder for attackers to use specialized hardware to speed up cracking attempts.
The Significance of the Work Factor
The work factor determines how many iterations the hashing function performs. A higher work factor means more computations, increasing the time required to generate the hash.
This adjustability allows organizations to strike a balance between security and performance. As hardware evolves, the work factor can be increased to enhance security without major overhauls to the system.
Real-World Applications of Bcrypt
Bcrypt is widely adopted across various platforms and applications for securing passwords. Its proven security makes it a go-to choice for developers aiming to protect user data effectively.
Let’s explore some real-world scenarios where bcrypt plays a critical role.
Web Application Authentication
Many websites and web applications use bcrypt to hash user passwords before storing them in databases. This practice ensures that, even if the database is compromised, the passwords are not immediately exposed.
Integration with Keycloak
Keycloak, an open-source Identity and Access Management solution, supports bcrypt among other hashing algorithms. With the rise of Argon2, Keycloak has updated its hashing mechanisms, but bcrypt remains a reliable option for many deployments (for versions pre 25).
By using bcrypt within Keycloak older than 25, developers can ensure compatibility and maintain a high level of security in their authentication flows.
Enterprise Security Solutions
Enterprises often rely on bcrypt for securing internal user credentials. The algorithm’s adaptability allows organizations to meet compliance requirements and enhance security over time.
Companies can adjust the work factor to align with their security policies without disrupting user experience or requiring significant infrastructure changes.
Comparing Bcrypt with Other Hashing Algorithms
With several password hashing algorithms available, it’s essential to understand how bcrypt stacks up against alternatives like Argon2 and PBKDF2.
Let’s compare these algorithms based on security, performance, and suitability for different use cases.
Bcrypt vs. Argon2
Argon2, the winner of the 2015 Password Hashing Competition, is considered the successor to bcrypt. It addresses some of the limitations of bcrypt by providing resistance to GPU cracking and offering configurable memory usage.
While Argon2 offers enhanced security features, bcrypt remains widely used due to its maturity and extensive support across platforms. For systems where memory consumption is a concern, bcrypt might still be the preferred choice.
Bcrypt vs. PBKDF2
PBKDF2 is another commonly used hashing algorithm, recommended by standards like NIST and used in FIPS-compliant environments. It allows for adjustable iterations to increase computational difficulty.
However, PBKDF2 is more susceptible to GPU acceleration attacks compared to bcrypt. Bcrypt’s structure inherently provides better resistance, making it a more secure option in environments where GPU-based attacks are a threat.
Common Challenges and Solutions with Bcrypt
Implementing bcrypt is not without its challenges. Understanding these issues and their solutions is crucial for effective and secure deployment.
Here are some common hurdles you might face and how to overcome them.
Performance Considerations
As the work factor increases, so does the time required to hash passwords. This can impact user experience during authentication and registration processes.
Solution: Balance the work factor to ensure security without significantly degrading performance. Conduct performance testing to find the optimal setting for your specific environment.
Migration to Bcrypt
Transitioning from another hashing algorithm to bcrypt can be tricky, especially when dealing with existing user passwords.
Solution: Implement a gradual migration strategy. When users log in, re-hash their passwords with bcrypt and update the stored hash. Alternatively, prompt users to reset their passwords to trigger bcrypt hashing.
Ensuring Compatibility
Not all systems or libraries may support the latest versions of bcrypt, leading to compatibility issues.
Solution: Verify the compatibility of bcrypt implementations in your technology stack. Use well-maintained libraries and keep them updated to ensure smooth operation.
Implementing Bcrypt in Your Authentication Systems
Ready to integrate bcrypt into your system? Here’s how you can implement it effectively, ensuring maximum security and efficiency.
Following best practices is key to avoiding common pitfalls and enhancing your system’s resilience against attacks.
Best Practices
Always use a unique salt for each password. This practice enhances security by ensuring that hashed passwords are unique, even if users choose the same passwords.
Regularly update the work factor to keep up with advancements in hardware capabilities. This proactive approach maintains the algorithm’s effectiveness over time.
Step-by-Step Implementation Guide
- Choose a reputable bcrypt library compatible with your programming language.
- Define an appropriate work factor. Start with a value that balances security and performance, such as 12.
- When a user sets or updates their password, generate a unique salt and hash the password using bcrypt.
- Store the hashed password and the salt securely in your database.
- During authentication, retrieve the stored hash and salt, and use bcrypt to hash the input password for comparison.
Conclusion
Bcrypt remains a robust and reliable password hashing algorithm, preferred for its security features and adaptability. By understanding its basics and implementing it correctly, you can significantly enhance the security of your authentication systems.
Remember to stay updated with industry best practices, regularly review your password policies, and consider the specific needs of your environment when choosing hashing algorithms. Whether you stick with bcrypt or consider newer options like Argon2, the key is to ensure that your users’ credentials are well-protected.
Ready to take your password security to the next level? Don’t hesitate to contact us at Skycloak for expert guidance and managed solutions. Your users’ security is our top priority! 🔒