Introduction
In this article, we look at how to use Passkeys with Keycloak.
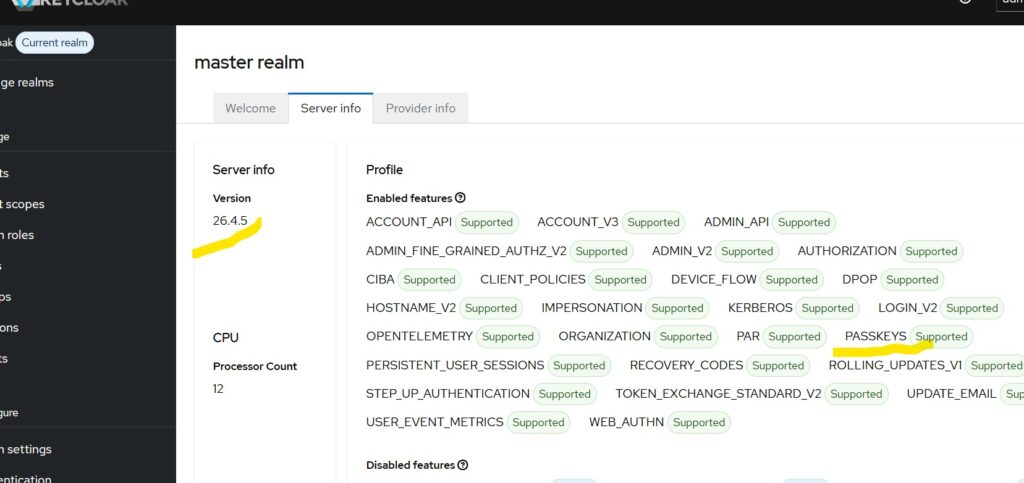
For demonstration, I am using Keycloak 26.4.5
What is a Passkey? (as per the FIDO Alliance)
A passkey is a FIDO authentication credential based on FIDO standards that allows users to sign in to apps and websites using the same mechanism they use to unlock their device—biometrics, PIN, or pattern.
Passkeys are cryptographic credentials tied to a user’s account on a website or application. They eliminate the need for passwords.
Additional Overview
Before using WebAuthn, a user must register a WebAuthn credential with Keycloak.
Keycloak acts as the Relying Party (RP), and the other components are:
- Browser
- Authenticator (built-in device authenticator or external hardware)
- User
WebAuthn works using public–private key cryptography. During registration:
- A public–private key pair is generated.
- The private key stays securely on the user’s authenticator (device or security key) and never leaves it.
- The public key is sent to Keycloak and stored in its database for future authentication.
Login Flow After Registration
Once registration is complete, a login attempt works like this:
- User tries to authenticate at Keycloak.
- Keycloak sends a challenge to the browser.
- The browser invokes
navigator.credentials.get(), which interacts with the authenticator. - The authenticator signs the challenge with the private key.
- The signed challenge is returned via the browser to Keycloak.
- Keycloak verifies the signature using the stored public key.
- If the signature is valid, the user session is created.
In Keycloak, WebAuthn can be used as:
- First-factor authentication (passwordless login)
- Second-factor authentication (after username/password)
Configuring passkey
Starting with Keycloak version 26.4 passkey can be configured more easily as per the Keycloak documentation over here.
In this article, we look at how to use passkeys for first-factor authentication
First, ensure that you are using a supported version of Keycloak.
Enabling passkeys
Preliminary Settings
Go to:
Realm Settings -> Authentication -> Policies -> WebAuthn Passwordless Policy
- Turn Enabled Passkeys= ON
It is also recommended to keep the following settings at their default values:
- Require discoverable credentials = Yes
- User Verification requirement = Required
Registering the user
A user can register a passkey using the built-in Account Console after logging in through the normal username/password flow:
Account Settings -> Signing In
If you have reviewed the documentation linked earlier, you will notice that the default browser authentication flow already supports first-factor passkey login. (we have to set Passkeys to ON as described in the beginning of this article)
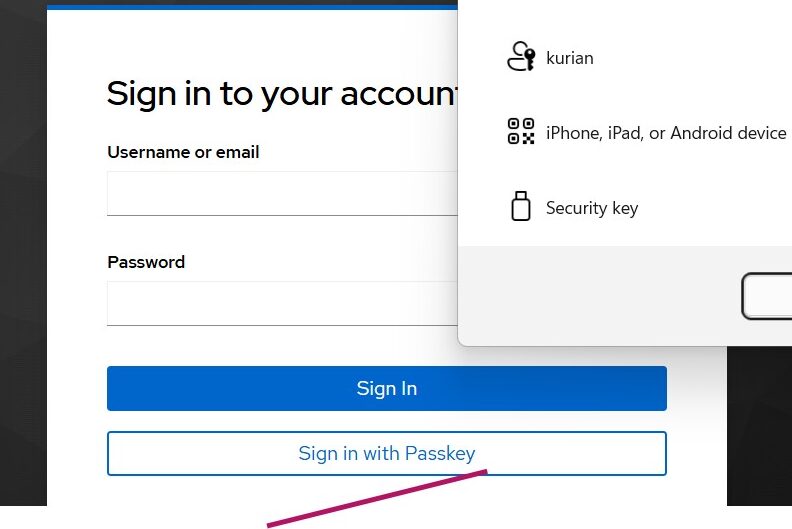
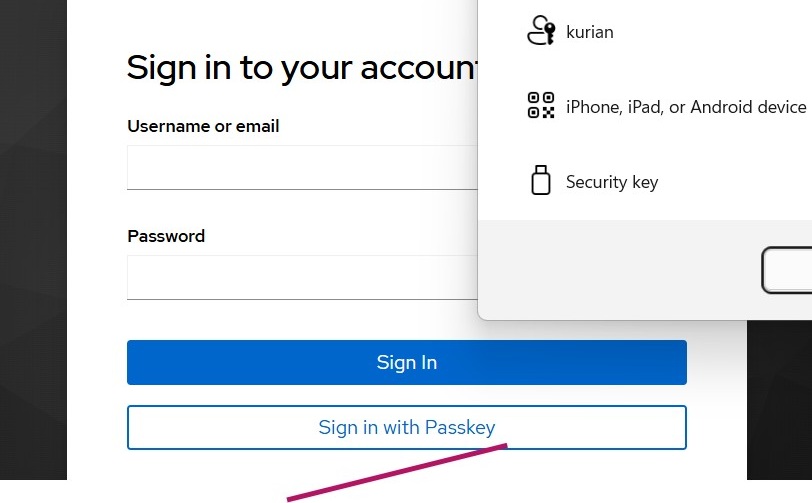
Testing the implementation
Access your client application or the built-in Account Console.
Click Sign in with Passkey and select the passkey you created during registration in the Account Console.
Summary
In this article, we explored how to use the Passkeys in Keycloak as a first-factor authentication method. With passkeys, users get a secure, phishing-resistant, password-free login experience powered by the FIDO2 standards.
Skycloak provides production-ready managed Keycloak hosting, helping teams avoid the complexity of maintaining and scaling Keycloak themselves.
If you’re new to Skycloak, visit the Skycloak Getting Started Guide to learn more.