Explore Insights on Identity and Access Management (IAM)
Discover expert tips, best practices, and in-depth guides to simplify and secure your IAM strategy. Search through our blogs to find something you need.
Popular categories
Authentication Error Handling: User Experience and Security Balance
Explore how to balance user experience and security in authentication error handling to enhance both safety and usability...
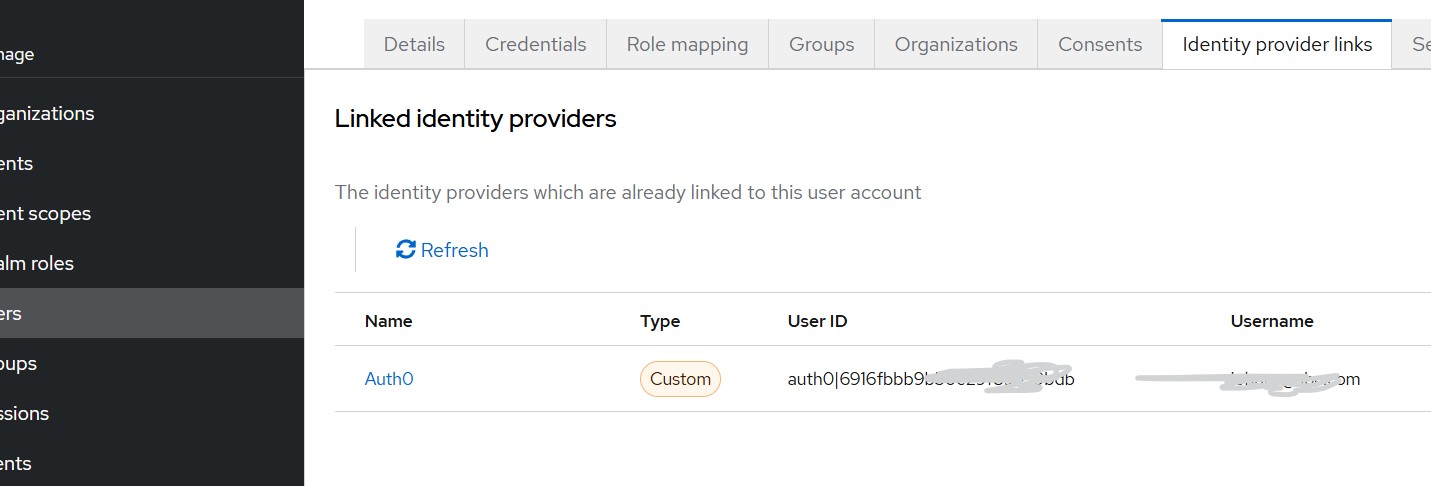
Read More...Attribute Mapping in Keycloak During OIDC Identity Brokering
Learn how to map user attributes such as email and phone number in Keycloak when using Auth0 or other providers through OIDC Identity Brokering...
Read More...Identity Governance Workflows: Automated Access Request and Approval Processes
Explore how automated identity governance workflows streamline access requests and approvals, enhancing security, compliance, and efficiency...
Read More...Authentication Metrics and KPIs: Measuring Identity System Performance
Explore essential metrics and KPIs for evaluating the performance of identity systems, focusing on security, user experience, and operational efficiency...
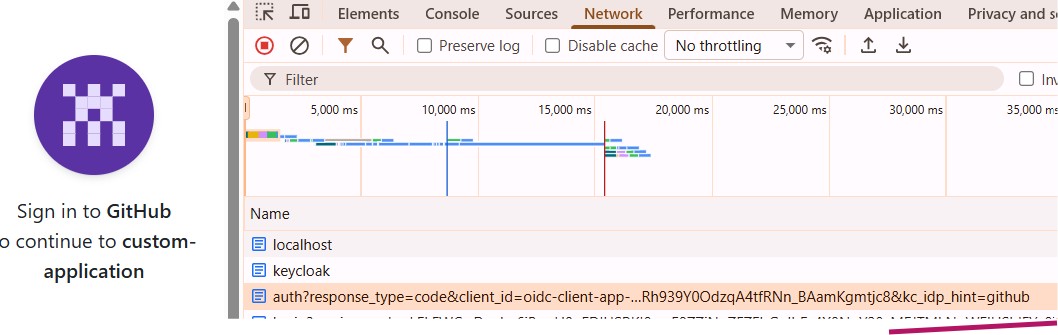
Read More...Use kc_idp_hint to Choose Identity Provider in Keycloak
Learn how to use the kc_idp_hint query parameter in Keycloak to automatically select and redirect users to the desired Identity Provider during OIDC login...
Read More...Authentication Technology Refresh: Modernization Planning and Timeline
Explore the essential steps for modernizing authentication systems, ensuring security, compliance, and a smooth transition to innovative protocols...
Read More...Identity Service Procurement: Contract Negotiation and SLA Requirements
Explore essential strategies for negotiating IAM contracts and SLAs to secure digital operations and ensure compliance with regulations...
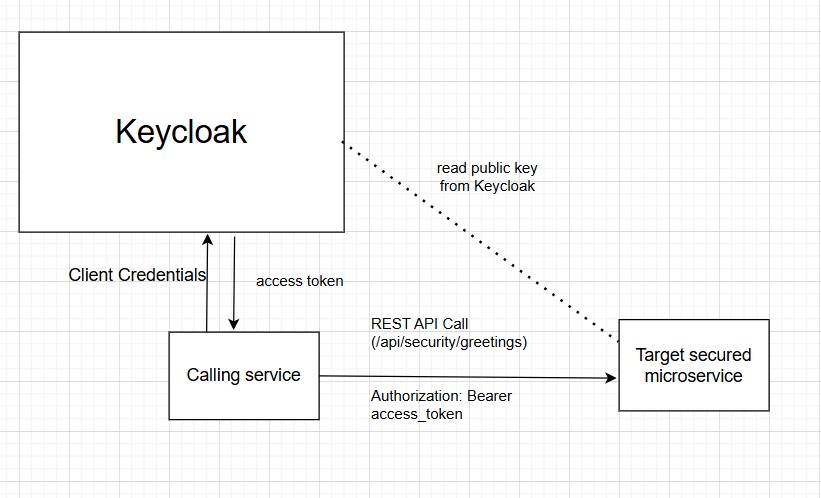
Read More...Secure Your Spring Boot REST API with Keycloak Token
Secure your Spring Boot REST API using Keycloak’s Client Credentials Grant with OAuth2 Resource Server. Client roles ensure authorized microservice access...
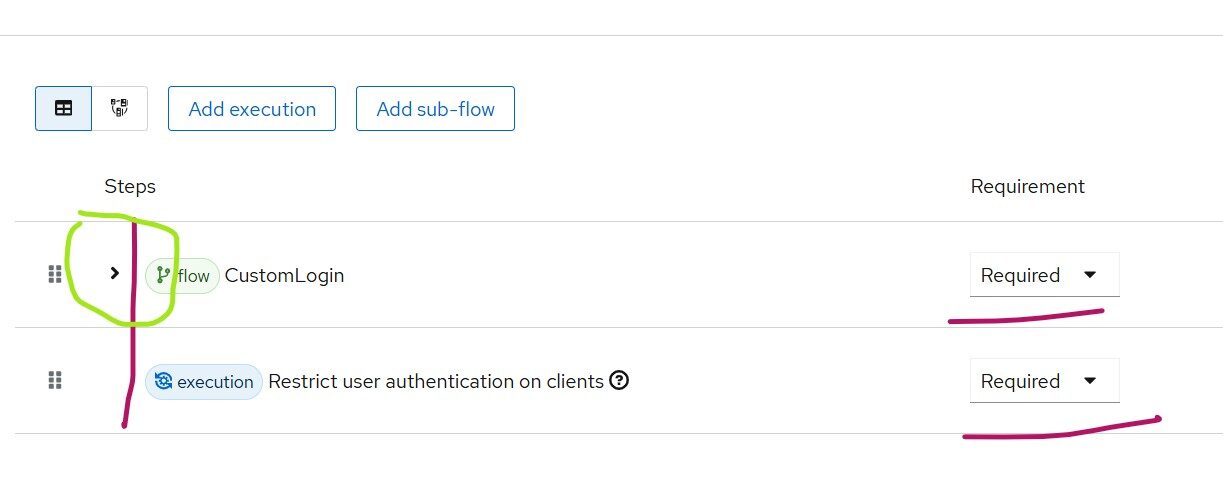
Read More...Restrict Keycloak Clients to Specific Users
Learn how to restrict Keycloak client applications to specific users using roles and do group-based access control by using custom extensions in Skycloak...
Read More...