Introduction
Keycloak is a popular, free, open-source Identity and Access Management (IAM) product. However, enterprises often face challenges in installing, maintaining, and scaling Keycloak to meet production-grade requirements.
Skycloak provides managed Keycloak hosting in the cloud, helping organizations overcome these challenges in a cost-effective way. It offers multiple plans supporting features such as high availability, custom domains, and more.
Keycloak, being open source, can be customized using extensions.
In this article, we will see how to use Email OTP custom extension with Skycloak.
Using extensions with Skycloak
The Skycloak Console comes with a set of freely available custom extensions that can be easily installed and configured.
By default, Keycloak does not include an option to use email-based OTP (One-Time Password) for multi-factor authentication (MFA).
Let’s look at how to use a free extension in Skycloak to enable this functionality.
First, ensure that you have created a cluster and a realm for your organization in the Skycloak Console and selected them from the left pane.
Next, configure the Email server so that your Skycloak cluster can send emails. The Skycloak Console provides clear instructions for this under Console → Email, so we won’t go into detail here.
Installing the Extension
In the Skycloak Console’s left pane, there is an Extensions menu. You’ll find a number of free extensions there.
We’ll focus on the Email OTP Authenticator, which can be installed with a single click. Once installed, the console will display it as shown below:

More details on this plugin are available here.
Configuring the Authentication Flow
Now, we want to enable Email OTP as the second factor for browser authentication.
- Go to the Keycloak Console and select the realm you created earlier.
- Navigate to Authentication → Flows in the left pane.
- Duplicate the existing Browser flow — for example, name it browser-email.
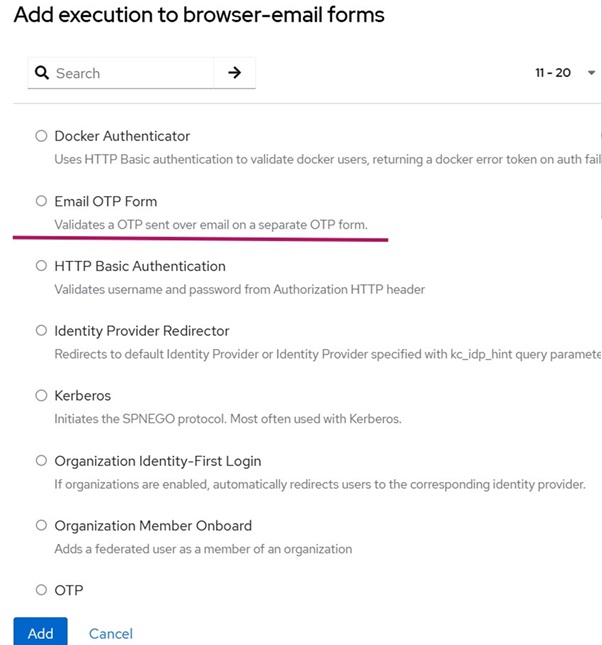
- In the duplicated flow, click the plus (+) button and choose Add Extension → Email OTP Form.
- Position it at the bottom
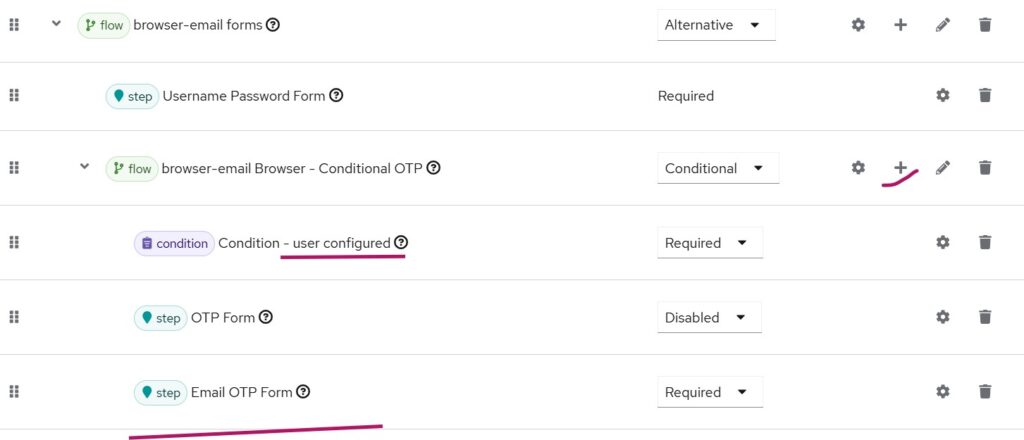
Note: Selecting gear button to the right of the Email OTP form, gives additional customization options. We have not covered them in this blog.
Ensure the Conditional OTP is set to CONDITIONAL (default).
Disable the default OTP form and instead enable the Email OTP Form, marking it as REQUIRED.
This ensures that if the user has an email configured, the second-factor authentication via email OTP will be triggered.
Once configured, mark the new browser-email flow as the current flow using the Actions menu in the top-right corner.
Verification
To verify your setup:
- Log in to your realm with a user account that has a valid email configured.
- After entering the username and password, you should see the following window:
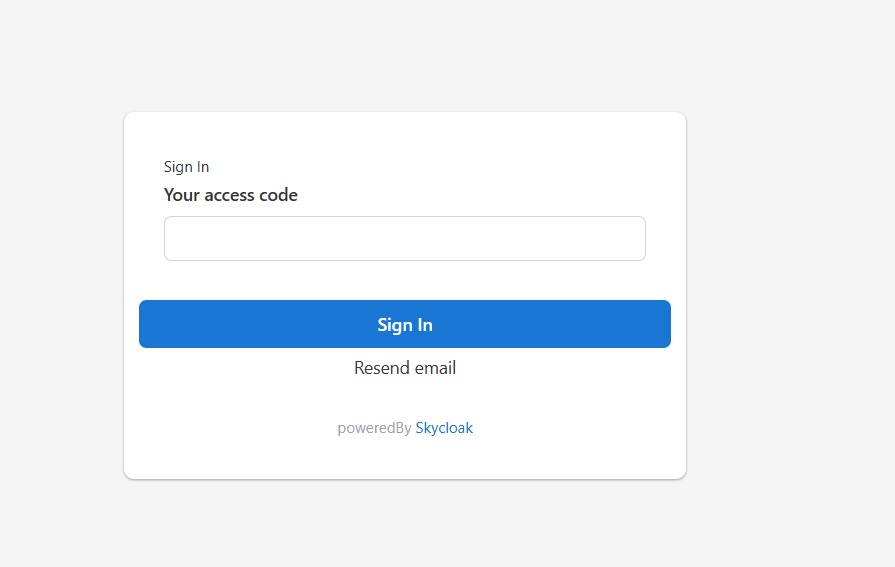
An email containing the OTP will be sent to the user’s registered email address. The user can then enter the OTP to complete authentication.
(Note: The footer displayed in the above window can be optionally disabled in the launch plan using the Branding option)
Summary
In this article, we explored how to enable Multi-Factor Authentication (MFA) in Keycloak using the Email OTP extension available with Skycloak. This integration helps enhance account security with an additional verification step beyond passwords.
Skycloak offers many more advanced features for managing and securing your Keycloak
If you’re new to Skycloak, visit the Skycloak Getting Started Guide to learn how to set up and make the most of its Keycloak extensions.