I recently received the question: Can I use the Master Realm for my users? Let’s dive in to figure out whether it’s a good idea.
TL;DR: No with some proof.
Keycloak, a widely-used Identity and Access Management (IAM) solution, offers powerful capabilities for authenticating and managing users in your applications. One concept at the core of Keycloak’s design is the “realm.” Realms in Keycloak help to partition the system to support multi-tenancy. But there’s one realm that stands out from the others: the Master realm.
What is the Master Realm?
The Master realm is the default realm created when Keycloak is first set up. It’s essentially the administrative space containing configurations for the Keycloak instance itself, including realms, clients, and user management. Think of the Master realm as the control panel for the Keycloak server.
Should I Use the Master Realm for My Users?
It might be tempting to use the Master realm for your users due to its default presence and full range of capabilities. However, this is generally discouraged for several reasons:
- Security Risks: The Master realm has elevated privileges that are necessary for administering the entire Keycloak instance. By adding regular users to this realm, you could inadvertently grant them access to sensitive areas, posing a significant security risk.
- Best Practices: Keycloak advocates for the separation of concerns. The Master realm is intended solely for administration purposes, not for regular user management or authentication services.
- Scalability and Organization: Utilizing separate realms allows for better organization and scalability. As your application or organization grows, managing users, roles, clients, and permissions becomes more complex. Segregating users into different realms can help manage this complexity efficiently.
Best Practices for Using Realms in Keycloak
Instead of using the Master realm for regular users, follow these best practices:
- Create Dedicated Realms: For each application or user group, create a dedicated realm. This approach enhances security and allows for custom configurations tailored to each group’s needs.
- Use Fine-Grained Permissions: In the realms that you create for your users, employ fine-grained permissions to ensure users have only the access they require. This principle of least privilege helps to reduce the risk of security breaches.
- Centralize Administration: While separating user spaces, maintain a centralized administrative approach using the Master realm. This method keeps your Keycloak instance’s management organized and secure.
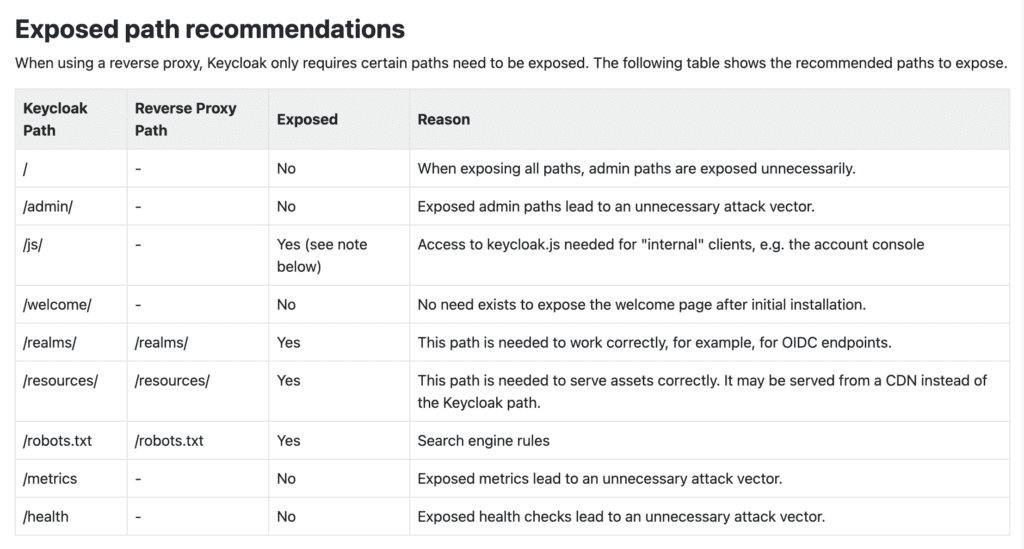
- Restrict Public Access to the Master Realm: For additional security, ensure that the path to the Master realm is not publicly accessible. Instead, it should only be accessible through private networks or secure VPNs. You can start by setting Keycloak behind a proxy. See the image below for some recommendations from Keycloak on what to allow and what to block.
- Regularly Review and Audit: Regularly review the configurations and permissions in all realms, including the Master realm, to ensure they are up-to-date and adhere to your security policies.
Conclusion
While Keycloak’s Master realm is powerful and essential for the overall management of your Keycloak instance, it is not designed for handling regular users. Creating separate realms for different user groups or applications is a more secure and organized approach that adheres to best practices in identity and access management.
Remember, the goal is to make your IAM solution work for you in the most effective and secure way possible. By following the recommendations outlined in this post, you can leverage Keycloak’s capabilities while maintaining a robust security posture.
