I was recently asked about the costs involved in self-hosting Keycloak compared to opting for managed hosting services. In this blog post, we’ll explore several factors to help you decide the best approach for hosting Keycloak—or any other tool—on your own.
In this analysis, we’ll work under the assumption that our cluster is designed to serve thousands of users while maintaining high availability. We plan to discuss smaller-scale options in future discussions.
Before we delve into the details, let’s clarify some key terms:
- “Self-hosting” refers to the process of setting up and maintaining the infrastructure that supports Keycloak, whether it’s on-premise or hosted in a private or public cloud.
- In our discussion, we’ll distinguish between Keycloak itself and its infrastructure requirements. Our focus will primarily be on the latter—specifically, on the orchestration and infrastructure management aspects, irrespective of whether these are managed as a platform or service.
- It’s important to note that we’ll consider the cost of configuring Keycloak to be consistent, regardless of who is managing the hosting.
No matter the deployment method—be it Kubernetes, VMs, Docker Swarm, or even your basement setup—the fundamental cost principles remain constant when operating Keycloak. These include:
- Infrastructure: The backbone of your setup, encompassing the physical or virtual resources needed.
- Security & Compliance: Ensuring your deployment is secure and meets regulatory standards.
- Operation: The day-to-day management and maintenance of your system.
Ultimately, the costs boil down to two main types: financial expenditure for services and the human effort required to achieve the desired outcomes.
Infrastructure
For this discussion, let’s simplify the infrastructure cost calculation by considering the following setup throughout the blog:
- A Keycloak cluster consisting of 3 nodes, each equipped with 16GB of RAM and 4 CPUs.
- A PostgreSQL instance for database needs, featuring 500GB of storage, 2 CPUs, and 8GB of RAM.
- A Reverse Proxy (such as Nginx or HAProxy) setup with 2 CPUs and 8GB of RAM, handling TLS termination.
We’ll also assume the use of local caching for efficiency. Given the importance of availability, each component is strategically placed in different physical locations (across zones or regions) to mitigate single points of failure, ensuring latency between instances does not significantly impact performance.

When discussing the orchestration of an application like Keycloak, it’s crucial to consider the infrastructure costs, which primarily revolve around CPU and RAM requirements. For the purposes of this blog, we’ll simplify by assuming the use of Virtual Machines (VMs). While more complex setups may involve container orchestration platforms like Kubernetes, the primary cost considerations remain the CPU and RAM.
Renting VMs for the system will comprise of:
- Keycloak Cluster: For a robust setup, renting 3 VMs, each with 4 CPUs and 16GB of RAM, is suggested. The cost per VM can vary between $80 to $260 monthly. For simplicity, we’ll estimate $170 per month for each VM, leading to a total of $510 per month for the cluster.
- Database and Reverse Proxy: Additionally, 2 VMs with 2 CPUs and 8GB of RAM will support the database and reverse proxy services. Costs here range from $40 to $160 per VM monthly. Averaging this to $100 per VM gives us a total of $200 per month for these services.
This setup, sourced from a reputable cloud provider, would thus approximate $610 monthly.
Security & Compliance
Ensuring the security of your Keycloak instances and PostgreSQL cluster is paramount. Basic security measures necessitate network configurations that prevent unauthorized access, adding both time and cost to the setup. This may include the use of Internet and NAT gateways along with proper routing to manage traffic securely, potentially adding additional costs. Here is a revised diagram:
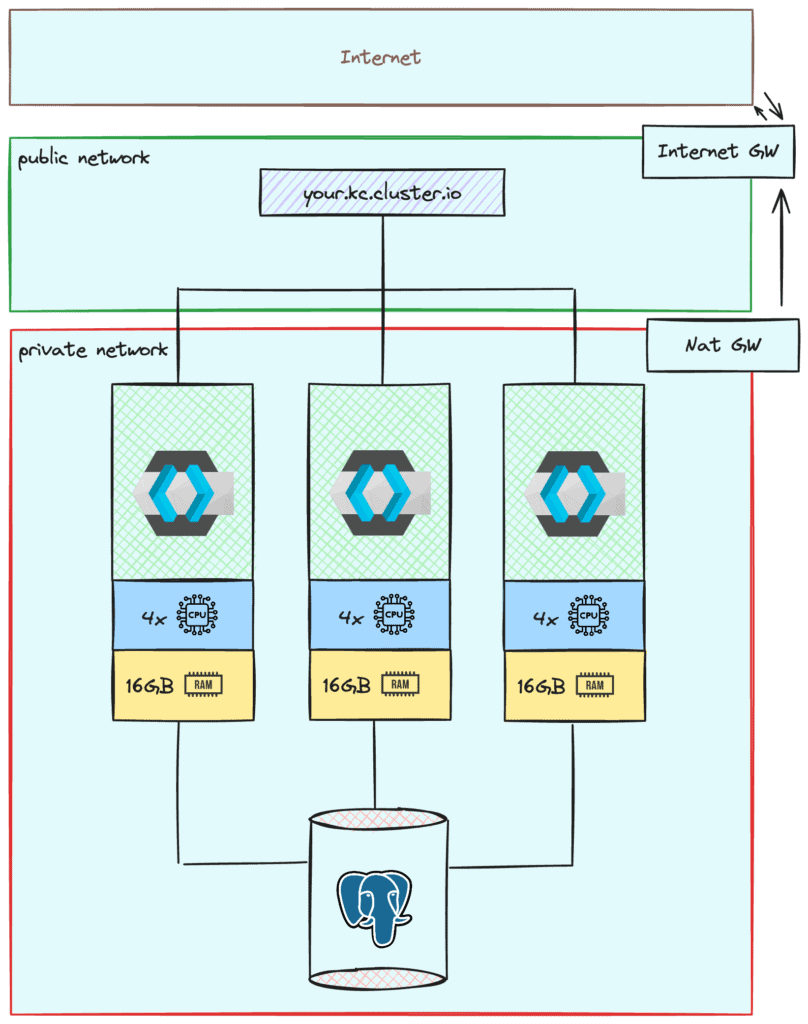
To ensure your cluster’s secure communication, you’ll need to establish internet and NAT gateways, alongside configuring routing tables for optimal traffic flow. Simplifying for this discussion, we’ll allocate one instance for each function at $80 each, totaling an additional $160 per month.
This scenario doesn’t yet factor in a firewall setup. It’s a straightforward case, but even this simple setup demands careful planning and testing to ensure security.
Adhering to minimum security best practices might lead to compliance audits like SOC, ISO, or GDPR requirements. The costs for these can be significant, potentially adding $100,000 in fees, though we’ll omit these from our basic calculations due to their variability.
Operation
With your cluster up and running, operational challenges can arise, such as:
- One instance runs out of memory
- One instance goes down due to hardware malfunction
- One instance was in a degraded state and the provider needed to restart it
- Your TLS certificate expired and you didn’t notice
- There is a new CVE that is now exposed and targets all PostgreSQL 15 which you are using
- etc.
These are just a few examples. Any infrastructure engineer will tell you that maintaining a system’s uptime is an ongoing task with a never-empty to-do list. Here is a comment from an IAM engineer complaining about maintaining the infra for an open source IAM solution.
I have zero experience with Keycloak, but if you don’t have the resources to manage it, don’t implement an open source IAM solution. You’re just asking for trouble.
I am a dedicated IAM engineer using a major cloud solution and it is absolutely a full time job.
I would just bite the bullet and use Azure/Okta/Ping/ForgeRock unless you are really strapped for cash or have unique data security concerns.
The_Security_Ninja
For operational maintenance, let’s assume an optimistic scenario where your cluster needs just three hours of upkeep per week. Assuming you have an entry-level engineer skilled in OS, database management, networking, and more, at a cost of $30/hour, this would equate to an additional $360 per month.
This budget should suffice for routine maintenance and support as needed, bringing us to a total monthly cost a minimum of $1250/month for hosting a Keycloak cluster capable of managing thousands of users.
Does this seem an affordable or costly venture for handling such a significant user base with a high-availability cluster? How much do you really think you would pay?
If you don’t even want to think about it, contact us and we will help you get where you want with Keycloak.
