Introduction
When looking at a SamlRequest XML file for the first time and you are not an authentication specialist, you will get dizzy. And it’s quite normal, understanding the nuts and bolts of SamlRequest is important when ensuring secure communication between your service providers and identity providers. Today. let’s check out SamlRequest and figure out what it truly means for SAML.
In this guide, we’ll explore the role of SamlRequest in the SAML protocol, discuss common challenges, and provide actionable insights on how to implement and manage SamlRequest effectively using tools like Keycloak.
Understanding SamlRequest in SAML
Before we dive into SamlRequest, it’s essential to grasp the basics of SAML (Security Assertion Markup Language). SAML is an XML-based framework for exchanging authentication and authorization data between parties, specifically between an identity provider (IdP) and a service provider (SP).
What is SAML?
SAML enables single sign-on (SSO) by allowing users to authenticate with an identity provider and access multiple service providers without re-entering credentials. It’s a cornerstone in federated identity management, promoting secure and seamless user experiences across various applications.
The Role of SamlRequest
The SamlRequest is an authentication request message sent by the service provider to the identity provider. It initiates the SAML authentication process, asking the IdP to authenticate the user and provide the necessary assertions for access.
This request contains essential information like the assertion consumer service URL, protocol binding, and request ID. Understanding and properly handling SamlRequest is vital for the integrity and security of the authentication flow.
The Anatomy of a SamlRequest
A SamlRequest is more than just a simple message—it’s a structured XML document that plays a pivotal role in the authentication process. Let’s break down its components and see how it fits into the authentication flow.
Components of SamlRequest
The SamlRequest typically includes:
- Request ID: A unique identifier for the request.
- IssueInstant: The timestamp of when the request was generated.
- AssertionConsumerServiceURL: The URL where the IdP should send the authentication response.
- Protocol Binding: Specifies the binding mechanism (e.g., HTTP POST, HTTP Redirect).
- Issuer: Identifies the service provider making the request.
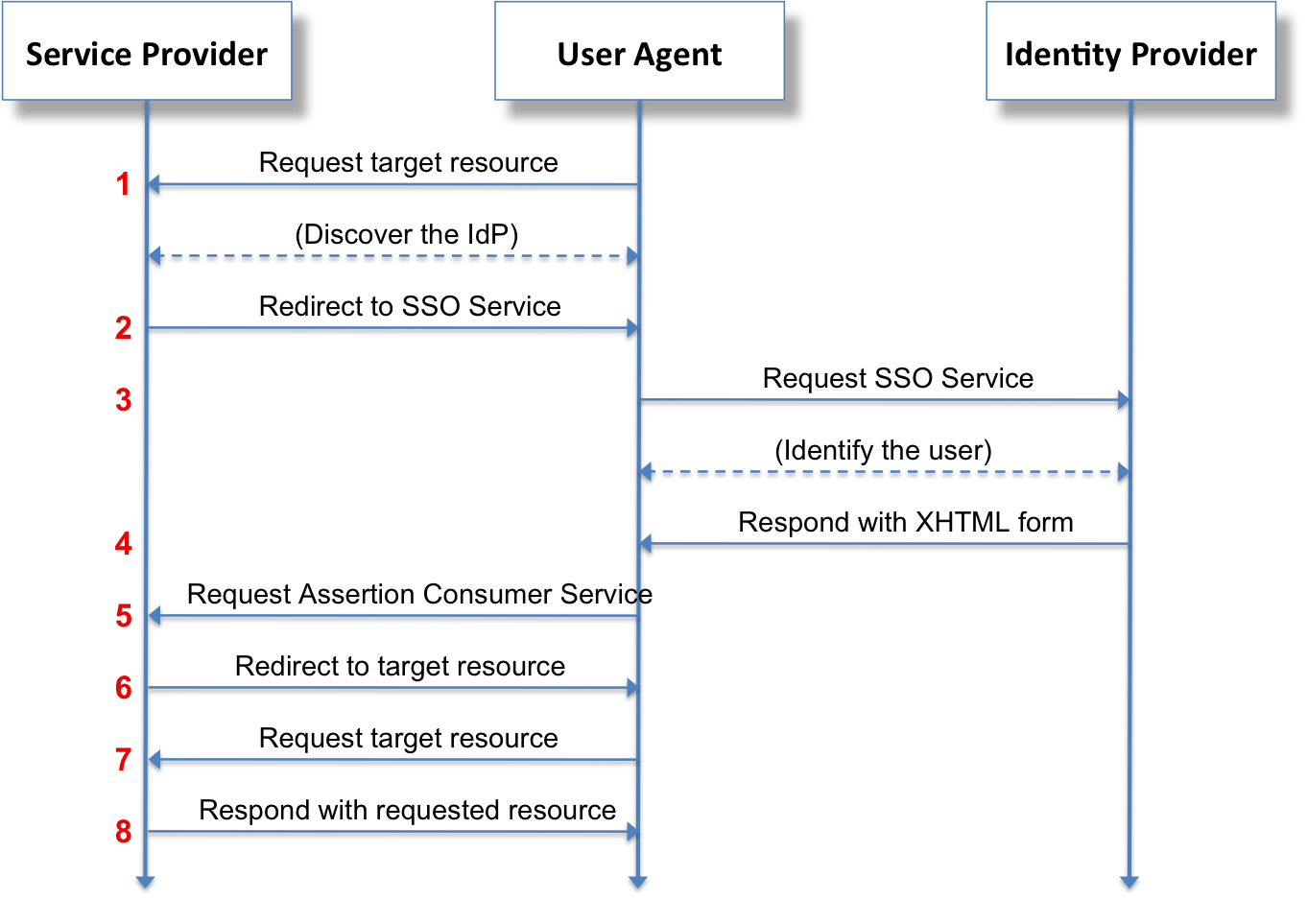
SamlRequest in the Authentication Flow
Here’s how SamlRequest fits into the SAML authentication flow:
- The user attempts to access a resource on the service provider.
- The service provider detects no active session and generates a
SamlRequest. - The SamlRequest is sent to the identity provider, often via a browser redirect.
- The identity provider processes the request, authenticates the user, and generates a SAML response.
- The response is sent back to the service provider, where the user is granted access.
Common Challenges with SamlRequest
While SamlRequest is a standard mechanism, it comes with its own set of challenges that can trip up even seasoned developers. Let’s explore some common hurdles and how to overcome them.
Digital Signature Verification Issues
One common challenge is verifying digital signatures on SamlRequests. If the signatures are not correctly generated or validated, it can lead to authentication failures. Ensure that both the service provider and identity provider are configured to use compatible signature algorithms and that the necessary certificates are in place.
For instance, mismatches in signature algorithms, such as using SHA-1 instead of SHA-256, can cause verification errors. Regularly update and align your cryptographic settings to industry standards to avoid these issues.
Time Synchronization Problems
SAML relies on accurate timestamps for security. If there’s a significant time skew between the service provider and identity provider servers, authentication requests may be rejected. Implement Network Time Protocol (NTP) synchronization on all servers to keep clocks in sync.
This is crucial because the IssueInstant and NotBefore/NotOnOrAfter conditions are time-sensitive. A discrepancy can make assertions appear invalid or expired.
Incorrect Binding Configurations
Using the wrong protocol binding (e.g., HTTP Redirect vs. HTTP POST) can lead to misunderstandings between the SP and IdP. Ensure that both parties agree on the binding method specified in the SamlRequest.
Double-check your application’s configuration settings and verify them against the identity provider’s supported bindings. Misconfigurations here can lead to lost or misinterpreted authentication requests.
Best Practices for Handling SamlRequest
To make the most of SamlRequest and bolster your application’s security, it’s important to follow industry best practices. Here are some actionable tips to enhance your SAML implementation.
Implementing Secure Signatures
Always sign your SamlRequests using strong algorithms like RSA-SHA256. Avoid deprecated algorithms such as SHA-1, as they are vulnerable to attacks. Ensure that your private keys are securely stored and managed.
In Keycloak, you can configure the signature algorithm by navigating to the client’s SAML settings and selecting the appropriate option. This ensures compatibility and security across your authentication flows.
Using Keycloak for SamlRequest Management
Keycloak is an open-source identity and access management solution that simplifies SAML implementations. It handles SamlRequest generation and processing securely and efficiently.
By leveraging Keycloak, you can:
- Automatically manage cryptographic keys.
- Configure identity brokering and user federation.
- Utilize built-in support for various SAML bindings and protocols.
For an even smoother experience, consider using Skycloak, which offers Keycloak on autopilot, simplifying deployment and management.
Regularly Updating and Testing Your Configuration
Stay ahead of potential issues by keeping your SAML configurations up to date. Regularly test your authentication flows, especially after making changes to certificates or cryptographic settings.
Automated testing tools and staging environments can help identify and resolve issues before they impact users. Remember, proactive maintenance is key to a secure and reliable authentication system.
Comparing SamlRequest Handling in Keycloak and Other Solutions
Choosing the right identity provider is crucial for effective SamlRequest handling. Let’s compare how Keycloak stacks up against other popular solutions.
Keycloak vs. Other Identity Providers
Keycloak offers several advantages:
- Open-source: No licensing fees and a strong community support.
- Flexible: Supports various protocols like SAML, OAuth2, and OpenID Connect.
- Extensible: Customizable through plugins and themes.
Other providers like Okta or Auth0 are commercial solutions that may offer more out-of-the-box integrations but come at a cost.
Why Choose Keycloak
If you’re looking for a cost-effective, robust, and flexible solution, Keycloak is a strong candidate. It excels in handling SamlRequest with ease and provides a comprehensive platform for identity and access management.
For organizations that prefer managed solutions, Skycloak’s pricing offers competitive options to run Keycloak without the hassle of maintenance.
Conclusion
Figuring out that using SamlRequest isn’t just a piece of XML sent somewhere—it’s about getting more authentication features available to your organizations with the security and efficiency of inspector Gadget. By grasping the role and structure of SamlRequest, you’re better equipped to troubleshoot issues, implement best practices, and choose the right tools for your needs.
Remember to stay vigilant about your configurations, keep your cryptographic settings up to date, and consider leveraging solutions like Keycloak for streamlined management. With these insights, you’re well on your way to mastering SAML authentication. Now, go forth and secure your applications like a pro! 🔐