Introduction
In the world of digital security, terms like OAuth and Single Sign-On (SSO) are thrown around frequently. But what do they really mean? Are they the same thing? If you’ve found yourself puzzled by these concepts, you’re in the right place! 😊 This beginner’s guide will reveal the mysteries of OAuth and SSO, highlight their key differences, and show you how to implement them using Keycloak. Let’s go!
Understanding OAuth
What is OAuth?
OAuth stands for Open Authorization. It’s an open standard protocol that allows secure authorization in a simple and standardized way from web, mobile, and desktop applications. Essentially, OAuth enables applications to obtain limited access to user accounts on an HTTP service, such as Facebook, GitHub, or Google.
For more detailed information on OAuth, you can visit the official website at oauth.net.
How OAuth Works
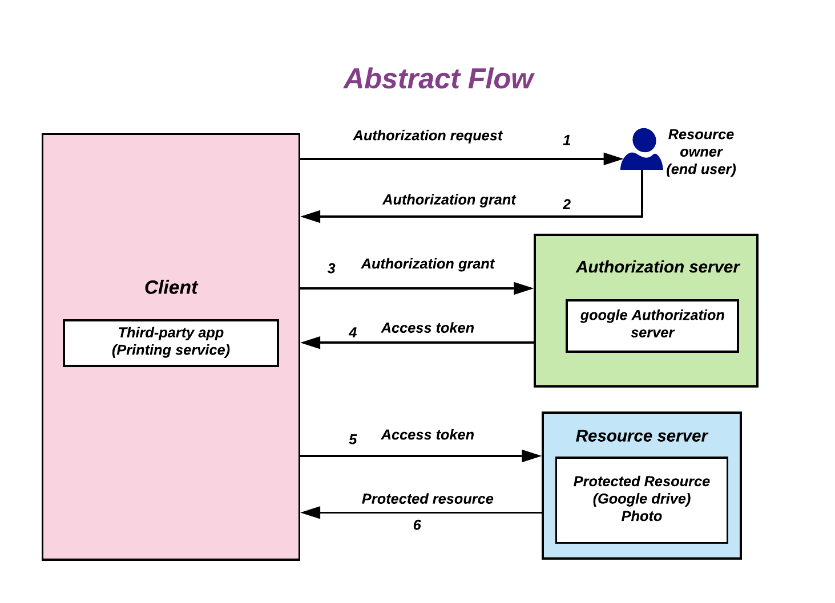
OAuth operates through a series of interactions between the user, the application, and the authorization server. Here’s a simplified flow:
- The application requests authorization from the user.
- If the user approves, the application receives an authorization grant.
- The application uses the grant to request an access token from the authorization server.
- With the access token, the application can access the user’s data from the resource server.
Common Use Cases for OAuth
OAuth is widely used in scenarios where applications need to access user data from another service without obtaining the user’s login credentials. For example:
- A third-party app posting on social media on behalf of a user.
- Analytics tools accessing data from a user’s account.
- Allowing applications to access a user’s contacts or calendar events.
Understanding Single Sign-On (SSO)
What is SSO?
Single Sign-On (SSO) is an authentication process that allows a user to access multiple applications with one set of login credentials. It centralizes user authentication to a single identity provider, improving security and user experience by reducing password fatigue.
SSO implementations often leverage protocols like SAML (Security Assertion Markup Language) or OpenID Connect. Learn more about OpenID Connect at openid.net.
How SSO Works
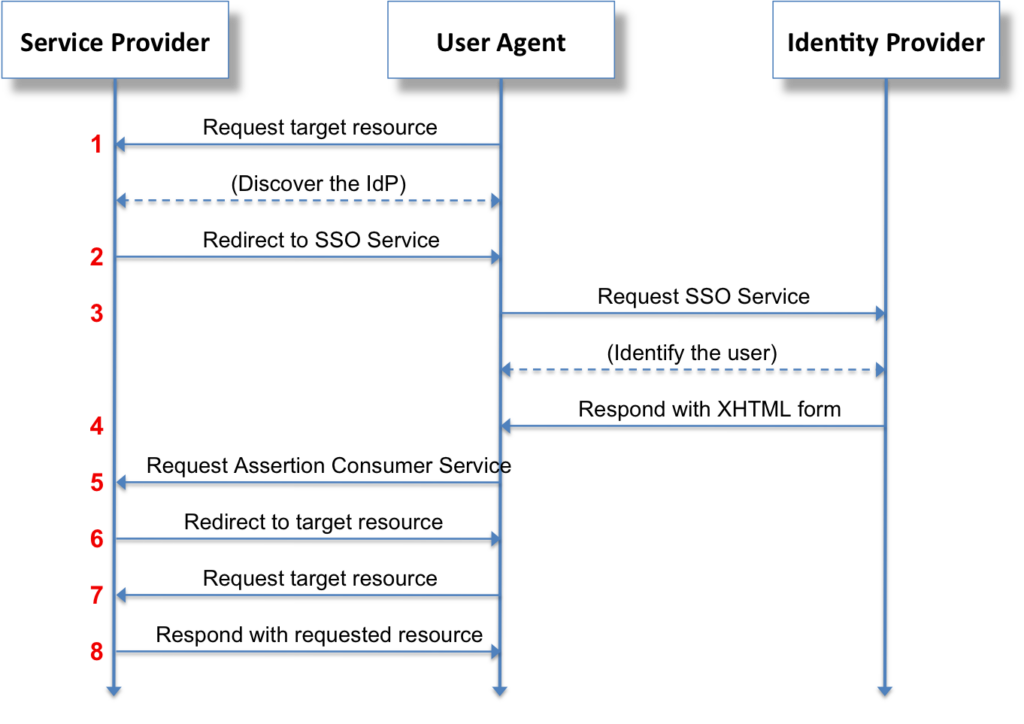
SSO functions by establishing trust between applications through a centralized authentication system. Here’s a simplified process:
- The user (user agent) tries to access an application.
- The application (service provider) redirects the user to the SSO authentication server (identity provider).
- The user logs in (if not already authenticated).
- The SSO server validates the credentials and returns an authentication token to the application.
- The user gains access without needing to log in again.
Common Use Cases for SSO
SSO is beneficial in environments where users need to access multiple applications seamlessly:
- Enterprise environments with numerous internal applications.
- Educational institutions providing access to various online resources.
- Unified access to cloud services and SaaS applications.
Is OAuth the Same as SSO?
Comparing OAuth and SSO
At first glance, OAuth and SSO might seem similar because they both deal with user authentication and authorization. However, they serve different purposes:
- OAuth is primarily an authorization framework that allows an application to act on behalf of a user.
- SSO is an authentication process enabling users to access multiple applications with one set of credentials.
Key Differences Between OAuth and SSO
Here are some crucial distinctions:
- Purpose: OAuth delegates authorization, while SSO focuses on user authentication.
- Function: OAuth allows third-party applications to access user data without sharing passwords, whereas SSO streamlines the login process for users across multiple applications.
- Protocols: OAuth uses tokens for authorization, whereas SSO often employs protocols like SAML (check out our blog about SSO vs SAML to reduce even more the confusion) or OpenID Connect for authentication.
When to Use OAuth vs SSO
Choosing between OAuth and SSO depends on your specific needs:
- If your application needs to access user data from another service on behalf of the user, OAuth is appropriate.
- If you want to provide a seamless login experience across multiple applications, SSO is the way to go.
Sometimes, both can be used together to enhance security and user experience.
Implementing OAuth and SSO with Keycloak
Keycloak as an Identity and Access Management Solution
Keycloak is an open-source Identity and Access Management (IAM) solution that provides both OAuth and SSO capabilities. It offers features like user federation, identity brokering, social login, and more.
With Keycloak, you can implement robust authentication and authorization mechanisms without building them from scratch.
Setting Up OAuth in Keycloak
To implement OAuth with Keycloak, follow these steps:
- Create a Realm: A realm manages a set of users, credentials, roles, and groups.
- Register a Client: Define your application as a client within Keycloak.
- Configure Client Settings: Set the access type to ‘confidential’ or ‘public’ based on your application’s needs.
- Obtain Access Tokens: Use Keycloak’s token endpoint ({{server}}/auth/realms/{{realm}}/protocol/openid-connect/token) to retrieve access tokens for authorized requests. To learn more about some OAuth authorization flow, check this out.
Setting Up SSO in Keycloak
Implementing SSO with Keycloak involves (this method leverages OpenID Connect for authentication. You could also create a SAML client for a different use case):
- Configuring Identity Providers: Set up external identity providers (e.g., Google, Facebook) for identity brokering.
- Enabling SSO Protocols: Configure protocols like SAML or OpenID Connect as needed.
- Adjusting Client Settings: Enable ‘SSO Session Idle’ and ‘SSO Session Max’ settings to manage session behavior.
Keycloak handles the heavy lifting, allowing users to authenticate once and gain access to multiple applications seamlessly.
Best Practices and Security Considerations
Security Implications of OAuth and SSO
While OAuth and SSO enhance user experience and security, they also introduce potential risks:
- Token Leakage: Access tokens can be intercepted if not secured properly. Always use HTTPS and implement token expiration.
- Single Point of Failure: In SSO, if the identity provider is compromised, all connected applications are at risk.
- Misconfiguration: Incorrect settings can lead to unauthorized access. Regularly audit configurations.
Common Challenges and Solutions
Here are some challenges you might face:
- Integrating Multiple Protocols: Managing different protocols like OAuth, SAML, and OpenID Connect can be complex. Solution: Use Keycloak’s flexible protocol support to simplify integration.
- User Identity Mapping: Conflicts in user identities across systems. Solution: Implement proper identity brokering and user federation strategies.
- Session Management: Handling user sessions across applications. Solution: Utilize Keycloak’s session management features to maintain consistency.
Real-world Examples and Scenarios
Let’s look at some practical applications:
- Enterprise Application Integration: A company uses Keycloak for SSO across their CRM, ERP, and intranet portal, streamlining employee access.
- Third-party API Access: A mobile app implements OAuth to allow users to share their social media photos within the app without sharing passwords.
- Educational Platforms: An online learning platform uses SSO to let students access courses, forums, and resources with a single login.
Conclusion
Understanding the difference between OAuth and SSO is crucial for implementing secure and user-friendly authentication systems. While OAuth focuses on authorization between applications, SSO streamlines the authentication process for users across multiple applications.
By leveraging tools like Keycloak, you can effectively implement both OAuth and SSO in your applications. Remember to consider security best practices, and don’t hesitate to explore Keycloak’s extensive documentation to get the most out of your identity and access management solutions.
Contact us if you need help to get started!