Explore Insights on Identity and Access Management (IAM)
Discover expert tips, best practices, and in-depth guides to simplify and secure your IAM strategy. Search through our blogs to find something you need.
Popular categories
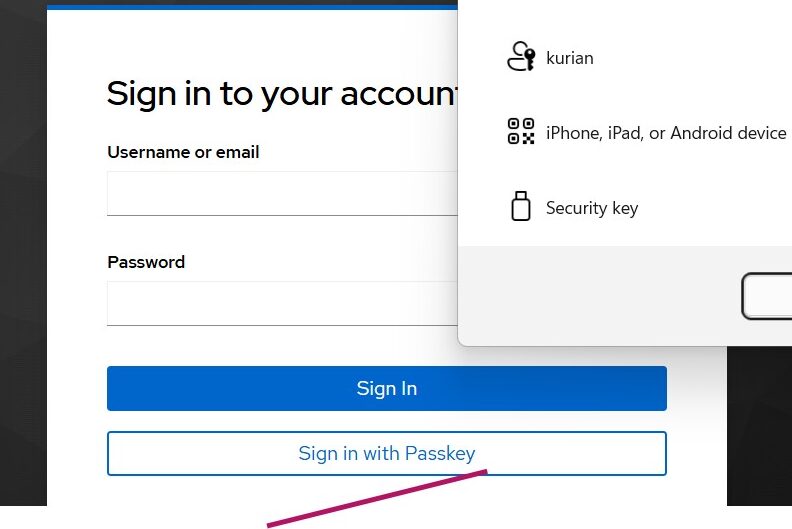
Keycloak WebAuthn Passwordless with Passkeys
Learn how to set up and use passkeys in Keycloak for secure, passwordless authentication using WebAuthn and FIDO2 standards...
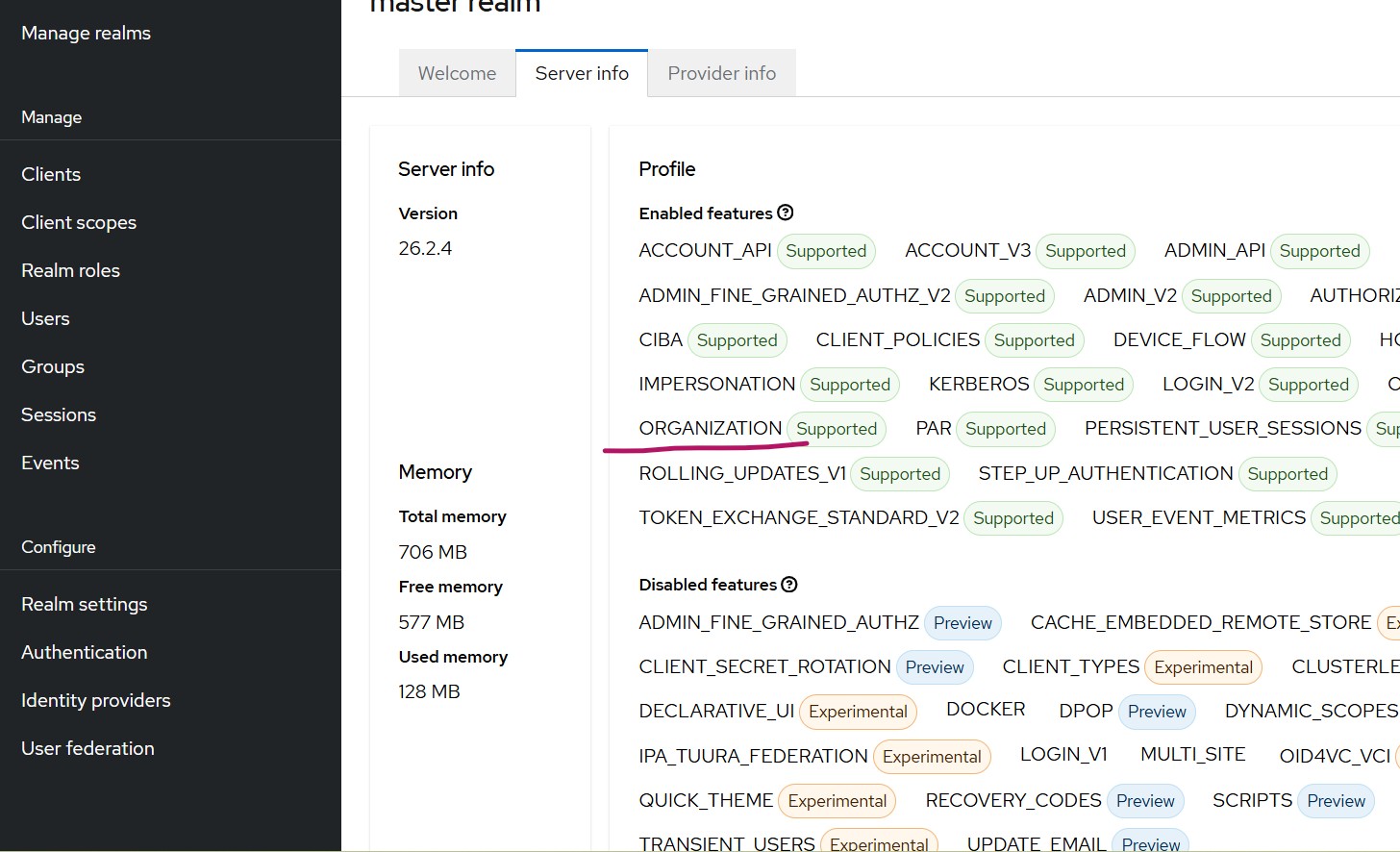
Read More...Multitenancy in Keycloak Using the Organizations Feature
Learn how to implement multitenancy in Keycloak using the Organizations feature, link external identity providers, and streamline B2B authentication securely...
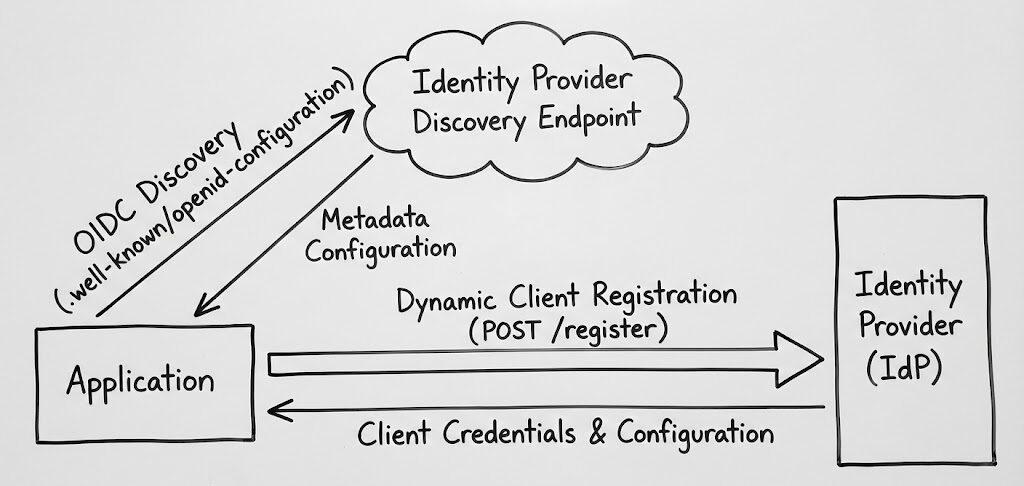
Read More...OIDC Discovery and Dynamic Registration: Automating Identity Provider Configuration
Automate identity provider configuration with OIDC Discovery and Dynamic Registration, enhancing security and efficiency while reducing errors...
Read More...Session Management in Distributed Systems: Cookies vs Tokens vs Server-Side
Explore the pros and cons of cookies, tokens, and server-side sessions in distributed systems to optimize security and performance...
Read More...Multi-Factor Authentication Integration Patterns for Enterprise Applications
Explore effective multi-factor authentication strategies for enterprises, balancing security, usability, and compliance across various industries...
Read More...JWT Token Lifecycle Management: Expiration, Refresh, and Revocation Strategies
Explore effective strategies for managing JWT token lifecycle, focusing on expiration, refresh workflows, and revocation to enhance security and user experience...
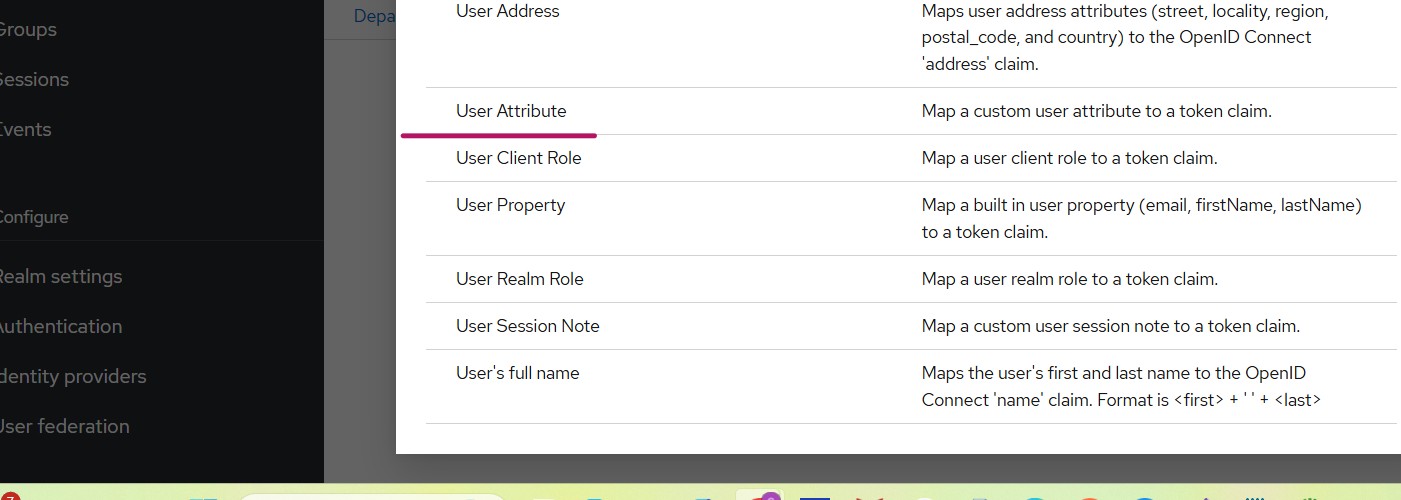
Read More...Using Custom User Attributes in Keycloak OIDC Tokens
Learn how to add custom user attributes to Keycloak tokens and map them to your OIDC client. Includes setup steps, Spring Boot example, and testing...
Read More...Authentication Capacity Planning: Scaling for Peak Usage Periods
Learn how to effectively plan authentication capacity to handle peak usage while maintaining performance, security, and compliance...
Read More...Identity Service Testing: Automated Validation and Quality Assurance
Automated IAM testing enhances security, compliance, and efficiency by validating workflows and reducing risks in identity management systems...
Read More...