Explore Insights on Identity and Access Management (IAM)
Discover expert tips, best practices, and in-depth guides to simplify and secure your IAM strategy. Search through our blogs to find something you need.
Popular categories
Top 7 Keycloak Cluster Configuration Best Practices
Optimize your Keycloak cluster with these 7 best practices for security, performance, and scalability, ensuring a robust authentication setup...
Read More...10 Best Practices for Secure SSO Implementation in 2025
Implementing secure Single Sign-On (SSO) in 2025 involves best practices like MFA, secure protocols, and regular audits to protect user identities...
Read More...Social Login Implementation: Step-by-Step Guide
Learn how to implement social login with Keycloak, enhancing user experience and security while simplifying authentication for your app...
Read More...Why Skycloak is a Premier Choice in the Identity and
Skycloak is proud to announce that one of the distinguished review platforms for software solutions and academic institutions, Research.com, has given Skycloak an assessment of its features and capabilities in providing clients with unremarkable and...
Read More...Reducing Insider Risk: Online Cyber Security with IAM Security Measures
IAM reduces insider risk by enforcing RBAC, MFA, and monitoring, ensuring secure access and protecting against data breaches...
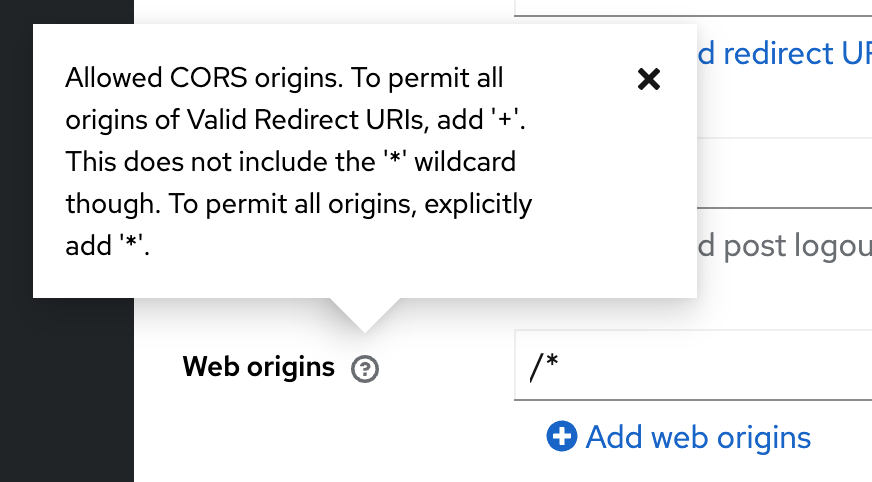
Read More...Configuring CORS with Your Keycloak OIDC Client
Learn how to configure CORS in Keycloak for secure OIDC client communication across domains. Step-by-step guide to avoid CORS-related errors...
Read More...Supabase or Keycloak? A complete Guide
Deep dive into this article to learn more about Supabase and Keycloak. Then figure out when to use one over the other...
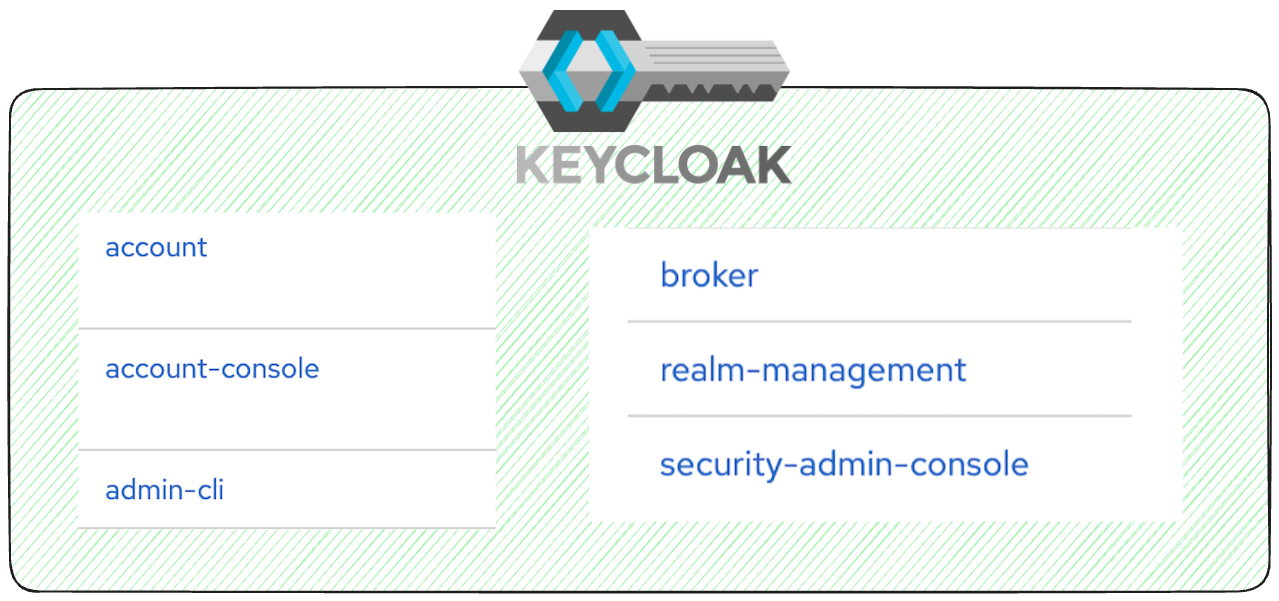
Read More...What to Do With the Default Clients in Your Newly
See what are the default clients generated by Keycloak when creating a new realm and what to do with them...
Read More...What is Keycloak Quarkus and Why You Need it Now
Keycloak evolves, and the shift to Quarkus was a game-changer. Discover why you should be considering this move for your IAM needs...
Read More...