Introduction
Ever felt the headache of managing user accounts across multiple platforms? 😩 If you’ve been juggling user provisioning manually, it’s time to meet your new best friend: the SCIM protocol. In this blog post, we’ll unravel what SCIM is and why it truly matters in today’s identity and access management landscape.
With the rise of cloud services and the need for seamless user experiences, provisioning and deprovisioning users efficiently has become more critical than ever. Enter SCIM—the System for Cross-domain Identity Management—that promises to simplify these complex processes. Let’s dive in and explore how SCIM can transform your user management strategies!
Understanding the SCIM Protocol
What is SCIM?
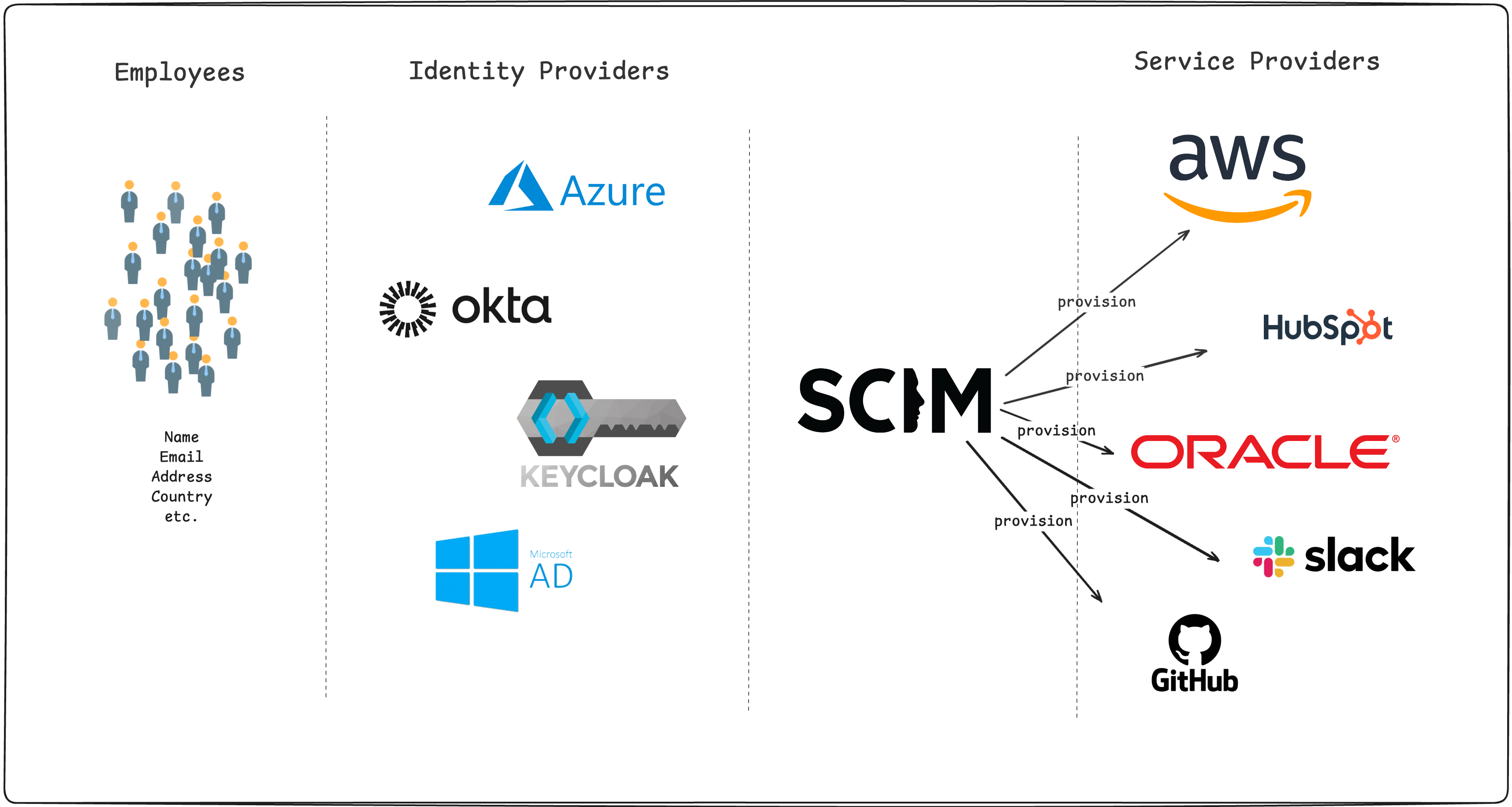
SCIM, short for System for Cross-domain Identity Management, is an open standard designed to manage user identities across different domains and platforms. It provides a standardized RESTful API with data formatted in JSON, making it easier for organizations to automate the exchange of user identity information.
At its core, SCIM aims to simplify user provisioning and deprovisioning, ensuring that user data remains consistent and up-to-date across multiple systems. This not only enhances security but also reduces administrative overhead.
The Evolution of SCIM
The journey of SCIM began to address the complexities associated with managing user identities in cloud-based applications. Initially developed as a response to the limitations of existing protocols like LDAP, SCIM has evolved through community collaboration to become a robust standard widely adopted in the industry.
Its evolution reflects the growing need for interoperability and standardization in identity management, paving the way for seamless integrations between identity providers and service providers.
Why SCIM Matters Today
In today’s fast-paced IT environments, organizations are leveraging an ever-increasing number of applications. Managing user access manually is not only inefficient but also prone to errors. SCIM addresses these challenges by automating user lifecycle management, ensuring that users have the right access at the right time.
Moreover, SCIM’s importance is amplified when integrating with identity management solutions like Keycloak or cloud services. By adopting SCIM, you can streamline your identity management processes and enhance security—a win-win situation!
Key Features of SCIM
Automated User Provisioning
One of the standout features of SCIM is its ability to automate user provisioning and deprovisioning. This means when a new employee joins your organization, SCIM can automatically create user accounts across all necessary systems. Conversely, when someone leaves, their access can be revoked promptly.
This automation reduces the risk of unauthorized access and ensures compliance with internal policies and industry regulations. It also frees up your IT team to focus on more strategic tasks.
Standardization and Interoperability
SCIM provides a standardized schema and protocol, which promotes interoperability between different identity providers and service providers. This standardization eliminates the need for custom connectors or proprietary solutions, simplifying integrations.
For example, SCIM can seamlessly integrate with platforms like Skycloak, which offers Keycloak managed as a service. You can then add an extension that would make SCIM available for your Keycloak cluster. Why an extension? At the moment of writing, Keycloak doesn’t support SCIM by default, but extensions are available.
Real-World Examples
Example 1: A multinational corporation uses SCIM to synchronize user identities between its HR system and cloud applications like Office 365 and Salesforce. This ensures employees have immediate access to the tools they need.
Example 2: An educational institution leverages SCIM to manage student access to various online learning platforms, automatically adjusting permissions as students enroll in or drop courses.
Example 3: A healthcare provider implements SCIM to control access to patient data systems, ensuring compliance with HIPAA regulations by promptly revoking access when staff change roles.
SCIM and Keycloak
Integrating SCIM with Keycloak
Keycloak is an open-source identity and access management solution that supports standard protocols like SAML and OpenID Connect. While Keycloak doesn’t natively support SCIM out of the box, integrating SCIM can enhance its user provisioning capabilities.
By using a SCIM plugin or third-party solutions like Skycloak, you can enable SCIM functionality in Keycloak. This integration allows for automated user management across all your connected applications.
Implementation Tips
When integrating SCIM with Keycloak, consider the following steps:
- Install a SCIM plugin compatible with your Keycloak version.
- Configure the SCIM endpoints and ensure they’re secured appropriately.
- Map the SCIM schema attributes to your Keycloak user attributes.
- Test the integration thoroughly before rolling it out to production.
Remember to consult the official Keycloak documentation and community resources for detailed guidance.
Security Considerations
Security is paramount when dealing with identity data. Ensure that all SCIM endpoints are secured using HTTPS, and implement proper authentication mechanisms.
Regularly audit your SCIM integrations to detect any unauthorized access attempts or anomalies. Keeping your Keycloak and SCIM implementations up-to-date with the latest security patches is also crucial.
Common Challenges and Solutions with SCIM
Synchronization Issues
One common challenge is ensuring data remains synchronized across all systems. Network latency or outages can cause delays in provisioning.
Solution: Implement retry mechanisms and regularly schedule synchronization jobs to mitigate temporary failures.
Data Consistency
Inconsistent data formats or validation rules across systems can lead to provisioning errors.
Solution: Standardize data formats and utilize SCIM’s schema validation features to enforce consistency.
Compatibility with Other Systems
Not all applications support SCIM natively, leading to integration hurdles.
Solution: Use middleware or identity platforms that act as a bridge between SCIM and non-SCIM systems, or consider developing custom connectors if necessary.
Best Practices for Implementing SCIM
Industry Best Practices
Adhering to industry best practices ensures a smooth SCIM implementation:
- Use standardized schemas and avoid custom extensions unless absolutely necessary.
- Keep your SCIM services stateless to improve scalability.
- Implement proper error handling and logging for troubleshooting.
Step-by-Step Implementation Guide
Here’s a simplified guide to implementing SCIM:
- Assess your current identity management landscape and identify systems to integrate.
- Choose an identity provider like Keycloak and ensure SCIM compatibility.
- Set up SCIM endpoints and configure security protocols.
- Map attributes between SCIM schema and your systems.
- Test the provisioning and deprovisioning processes thoroughly.
Security Implications
Always consider the security implications when working with identity data:
- Enforce strong authentication and authorization for SCIM endpoints.
- Encrypt data in transit using TLS.
- Regularly update and patch all systems involved.
Neglecting security can lead to data breaches and compliance violations.
Comparing SCIM with Other Protocols
SCIM vs. LDAP
LDAP has been a staple in directory services for decades. While LDAP is powerful, it lacks the modern, web-friendly approach of SCIM.
SCIM Advantages: Uses RESTful APIs, easier integration with cloud services, and utilizes JSON instead of complex LDAP queries.
SCIM vs. SAML
SAML is primarily used for authentication and authorization, not provisioning.
SCIM Advantages: Focuses on user provisioning and lifecycle management, complementing protocols like SAML and OpenID Connect.
Detailed Comparisons
When choosing between protocols, consider your organization’s specific needs. SCIM excels in provisioning, while others may be better suited for authentication.
For more insights, you can read about open identity standards at openid.net and further explore Keycloak’s capabilities on keycloak.org.
Conclusion
Implementing SCIM can revolutionize how you manage user identities across your organization. By leveraging this powerful protocol, you can automate tedious provisioning tasks, reduce security risks, and ensure compliance with ease.
Ready to get started? Here’s what you can do next:
- Evaluate your current identity management processes and identify areas where SCIM can bring improvements.
- Explore SCIM integration with platforms like Skycloak to simplify your Keycloak deployments.
- Stay informed about best practices and keep security considerations at the forefront during implementation.
Don’t let outdated processes hold you back. Embrace SCIM and take control of your user management today! 🚀