Introduction
Ever found yourself scratching your head over the terms SSO and SAML? You’re not alone! In identity and access management, these two acronyms play big big roles (no pun intended). Understanding them is not just beneficial—it’s essential for securing your applications and providing a great user experience these days. Let’s demystify SSO and SAML together and discover how tools like Keycloak can help implement them effectively. 🚀
Demystifying SSO: What It Is and How It Works

Single Sign-On (SSO) is a user authentication process that permits a user to access multiple applications with one set of login credentials. That’s it! One to rule them all. This not only enhances security but also significantly improves user convenience. Let’s delve deeper into how SSO works and why it’s a game-changer in the authentication world.
Understanding Single Sign-On (SSO)
SSO is an authentication scheme that allows users to log in with a single ID and password to any of several related, yet independent, software systems. It authenticates the user for all the applications they have rights to and eliminates further prompts when switching applications during a session.
For example, think about how you can access Gmail, Google Drive, and YouTube with a single Google account. That’s SSO in action!
Benefits of Implementing SSO
Implementing SSO brings multiple benefits:
- User Convenience: Reduces password fatigue from different username and password combinations.
- Improved Security: Decreases the chances of phishing by centralizing authentication (assuming the centralized IdP is secured).
- Lower IT Costs: Reduces help desk calls about forgotten passwords.
A real-world example is a corporation where employees need to access various internal applications. With SSO, they authenticate once and gain access to all authorized applications without repeated logins. If you work in a Microsoft enterprise environment, you may be using SSO when logging in to your corporate laptop, then accessing your mail, calendar, drive, SaaS tools, without even providing a single credentials (but you may notice some redirections happening ;)).
Unpacking SAML
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, specifically between an identity provider and a service provider. SAML plays a crucial role in enabling SSO, especially in enterprise environments.
What is SAML?
SAML is an XML-based framework that facilitates the exchange of user authentication and authorization data across secure domains. It allows identity providers to pass authorization credentials to service providers.
Consider a university’s online portal where students access different services like course registration, library resources, and grade reports—all through a single login facilitated by SAML.
How SAML Works in Authentication
SAML works through a process of exchanging XML documents between the identity provider and the service provider. Here’s a simplified flow:
- User attempts to access a service provider (i.e. course registration web application).
- The service provider redirects the user to the identity provider for authentication (the centralized location where the identity resides).
- User authenticates with the identity provider.
- The identity provider sends a SAML assertion (an XML document) to the service provider.
- The service provider validates the assertion and grants access to the user.
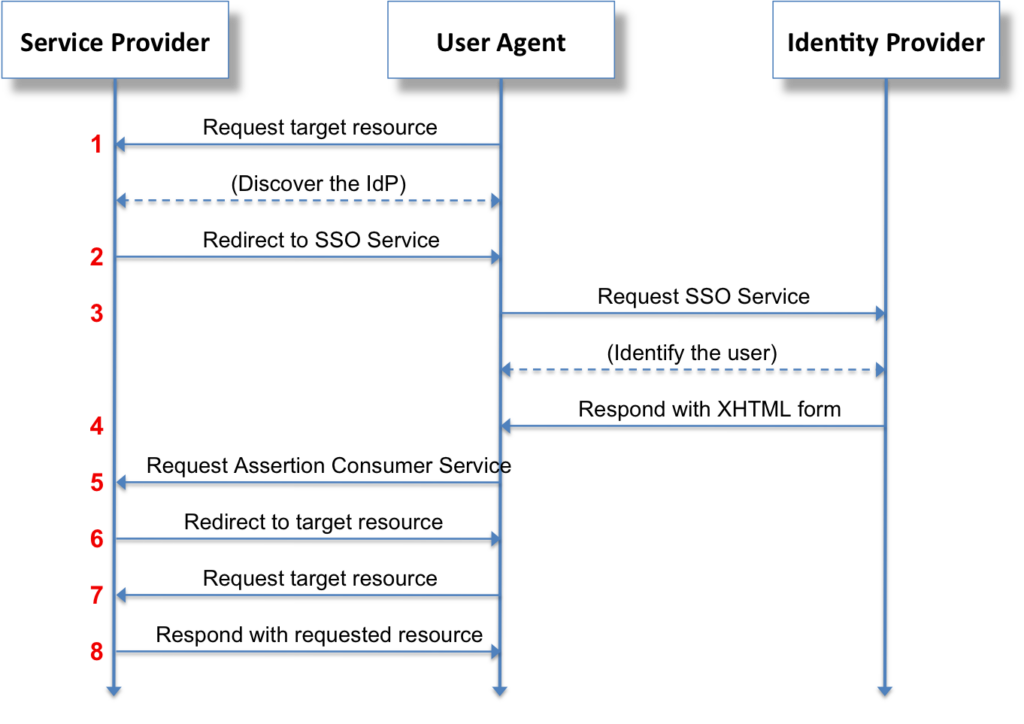
This process ensures that authentication credentials are handled securely and efficiently.
SSO vs. SAML: Key Differences Explained
While SSO and SAML are closely related, they are not the same. It’s important to understand their differences to implement the right authentication strategy for your needs.
Protocol vs. Methodology
SSO is a methodology or concept that allows users to access multiple applications with one set of credentials. It’s about the user experience of logging in once and accessing multiple services.
SAML, on the other hand, is a protocol used to implement SSO, especially in web applications. It’s the underlying technology that enables single sign-on by facilitating the exchange of authentication and authorization data.
Basically, SAML is one of the ways to achieve SSO.
Use Cases and Scenarios
Different scenarios call for different protocols:
- SAML: Ideal for enterprise and B2B applications requiring advanced security and where users are primarily accessing services via a web browser.
- OAuth2/OpenID Connect (OIDC): Better suited for mobile and single-page applications where tokens are preferred over XML documents.
An e-commerce platform integrating with various third-party services might choose OAuth2/OIDC for its flexibility, whereas a government agency might opt for SAML due to its robust security features.
For a deeper comparison, check out the Cloud Security Alliance resources.
Implementing SSO and SAML with Keycloak
Keycloak is an open-source Identity and Access Management (IAM) solution that makes it easy to secure applications and services with minimal coding. Let’s explore how to implement SSO and SAML using Keycloak.
Setting Up SSO in Keycloak
Here’s how to set up SSO in Keycloak:
- Install Keycloak: Download from the official website and follow the installation guide.
- Create a Realm: Realms manage a set of users, credentials, roles, and groups.
- Register Clients: Clients represent applications and services that Keycloak secures.
- Configure Identity Providers: Set up social logins or integrate external identity providers.
For organizations seeking a hassle-free setup, We at Skycloak, offer Keycloak on Autopilot, providing managed Keycloak services to simplify the implementation process.
Configuring SAML in Keycloak
To configure SAML in Keycloak:
- Create a SAML Client: In your realm, navigate to Clients and create a new client with the
Client Protocolset to SAML. - Configure Client Settings: Set the
Service Provider Entity ID,Single Sign-On Service URL, and other relevant fields. - Set up Mappers: Map user attributes to SAML attributes as needed.
- Adjust Fine-Grained SAML Settings: Configure signatures, encryption, and bindings (POST or Redirect) based on your security requirements.
For detailed configuration options, refer to the Keycloak Server Administration Guide.
Pro Tip: Ensure your server’s clock is synchronized. Time discrepancies can cause SAML assertions to be rejected due to invalid timestamps.
Common Challenges and Solutions
Implementing SSO and SAML isn’t without its hurdles. Here are some common challenges and how to overcome them.
Security Implications and Considerations
Challenge: Ensuring secure token exchange and protecting against attacks such as replay attacks.
Solution:
- Always use HTTPS to encrypt communications.
- Implement token signing and validation to prevent tampering.
- Set proper token lifespans to minimize risk.
Regular security audits and staying updated with the latest security patches is vital. For expert guidance, consider reaching out to professionals via the Contact Page.
Overcoming Integration Hurdles
Challenge: Integrating SSO/SAML with legacy systems or applications that weren’t designed with modern authentication in mind.
Solution:
- Use Keycloak’s adapters and libraries that support various platforms and languages.
- Leverage protocols like OIDC for more flexible integration when SAML isn’t supported.
- Implement custom authentication flows using Keycloak’s extensibility features.
Real-world Example: A particular company needed to integrate modern SSO with their decade-old internal systems (they had multiple systems with different authentication tool). By utilizing Keycloak’s custom authenticators and flexible configuration, they successfully implemented SSO without overhauling their existing infrastructure.
Managing User Data and Privacy
Challenge: Handling sensitive user information securely while complying with data protection regulations.
Solution:
- Configure Keycloak to minimize the amount of user data transmitted in SAML assertions.
- Implement encryption for sensitive attributes.
- Stay informed about regulations like GDPR and ensure your authentication flows are compliant (if it applies to you).
Best Practice: Regularly review your application’s data handling policies and adjust your Keycloak configuration accordingly to protect user privacy.
Conclusion
Understanding the difference between SSO and SAML is crucial for implementing secure and efficient authentication strategies. By leveraging tools like Keycloak, you can streamline your authentication processes, enhance security, and provide a seamless user experience.
Don’t let the complexities of authentication hold you back. Take actionable steps today:
- Assess your organization’s authentication needs.
- Explore Keycloak’s capabilities.
- Consider partnering with experts like us at Skycloak for managed solutions.