Introduction
Have you ever worked in an enterprise level organization where applications harmoniously share authentication and authorization data, providing a nice and smooth experience for users across platforms? I bet you did. But how do they do that? Keycloak is one way to do so! In today’s rapidly evolving digital landscape, enterprises need robust identity and access management (IAM) solutions that not only secure resources but also offer great flexibility and scalability.
Keycloak, an open-source IAM solution, has emerged as a leader in providing Single Sign-On (SSO) capabilities, Identity Brokering, and more. This blog post delves into how enterprises can leverage Keycloak integrations to enhance security, streamline operations, and provide a superior user experience. Let’s explore the key features, real-world applications, and best practices for implementing Keycloak in an enterprise setting.
Understanding Keycloak and Its Core Concepts
Keycloak is more than just an authentication server; it’s a comprehensive IAM solution that supports OpenID Connect, OAuth 2.0, and SAML 2.0 protocols. It allows enterprises to centrally manage user identities, define security policies, and integrate with various applications and services.
Key Features of Keycloak
Keycloak offers a plethora of features designed to meet enterprise needs:
- Single Sign-On (SSO): Enables users to authenticate once and gain access to multiple applications.
- Identity Brokering: Allows integration with external identity providers like Google, Facebook, or corporate LDAP servers.
- User Federation: Synchronizes user data from existing directories such as LDAP and Active Directory.
- Role-Based Access Control (RBAC): Manages user permissions through roles and groups.
- Two-Factor Authentication (2FA): Adds an extra layer of security with TOTP/HOTP protocols.
- And more through custom extensions!
Core Concepts and Terms
Understanding Keycloak’s terminology is crucial for successful integration:
- Realm: A space where users, credentials, roles, and groups are managed.
- Client: Representation of an application or service that requests authentication from Keycloak.
- Identity Provider: External services that Keycloak can delegate authentication to.
- User Federation: Linking external user databases to Keycloak.
Integrating Keycloak into Enterprise Environments
Integration is at the heart of Keycloak’s value proposition. By connecting Keycloak with existing enterprise systems, organizations can achieve unified authentication and authorization across all applications.
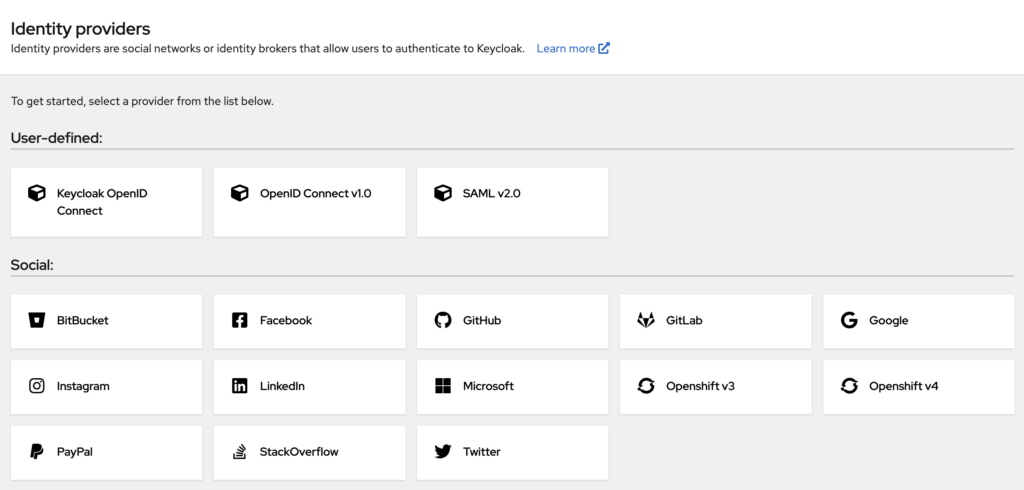
Integrating with LDAP and Active Directory
Many enterprises rely on LDAP or Active Directory (AD) for user management. Keycloak’s User Federation feature allows synchronization with such systems:
- Configuration: Connect Keycloak to LDAP/AD servers to import user data.
- Synchronization: Schedule regular syncs to keep user data up-to-date.
- Authentication: Users authenticate using their LDAP/AD credentials.
This integration ensures that existing user management workflows remain uninterrupted while enhancing security.
Leveraging Identity Brokering for Social Logins
Enterprises can enhance user convenience by enabling social logins:
- Supported Providers: Google, Facebook, GitHub, Twitter, and more.
- Configuration: Set up identity providers in the Keycloak Admin Console.
- User Experience: Users can choose to authenticate via their preferred social platforms.
This is particularly useful for customer-facing applications where ease of access can improve engagement.
Securing RESTful Services
For enterprises offering APIs, securing RESTful services is critical:
- Token-Based Authentication: Utilize OAuth 2.0 access tokens for API requests.
- Policy Enforcement: Define fine-grained access policies using Keycloak’s Authorization Services.
- Example: A financial institution securing its transaction APIs to ensure only authorized apps can initiate transfers.
Real-World Example of Keycloak Integrations
Let’s look at how an enterprise can successfully integrate Keycloak into their ecosystems.
Case Study: Global Retailer Enhances SSO
Centralized Authentication Revolution: A Retail Success Story with Keycloak
The Challenge
A global retailer faced a major hurdle: multiple authentication systems across its e-commerce platforms, mobile apps, and in-store systems. This patchwork approach led to slow login processes and a fragmented customer experience. The result? Frustrated users and abandoned shopping carts.
The Solution
The retailer adopted Keycloak, integrating it as the centralized identity and access management system across all platforms. By leveraging Single Sign-On (SSO) and streamlining user authentication, they cut login times by 50%.
Keycloak’s flexibility allowed them to seamlessly connect their web and mobile applications, as well as their in-store point-of-sale systems, providing a unified and secure login experience. Additional features like passwordless authentication and social logins were implemented to enhance usability.
The Outcome
This transformation not only improved login efficiency but also elevated customer satisfaction, with happier users more likely to complete their purchases. The result? Higher conversion rates and stronger brand loyalty.
The Takeaway
Keycloak isn’t just a tool—it’s a game changer for businesses that prioritize seamless customer experiences. By unifying disparate systems, businesses can unlock both operational efficiency and customer satisfaction.
Pro tip: If you’re a retailer or business looking to simplify authentication across your digital and physical platforms, tools like Keycloak paired with expert hosting services (like Skycloak.io) can give you the competitive edge.
Overcoming Common Challenges
While Keycloak offers numerous benefits, enterprises may face challenges during integration.
Challenge 1: Scaling and Performance
Solution: Deploy Keycloak in a clustered environment to ensure high availability. Utilize solutions like Skycloak to automate scaling and management.
Challenge 2: Customizing Login Pages
Solution: Take advantage of Keycloak’s theme support to tailor user interfaces. Ensure branding and user experience remain consistent across applications.
Challenge 3: Managing Legacy Applications
Solution: Use Keycloak’s support for SAML to integrate with older applications that do not support modern protocols like OpenID Connect.
Best Practices for Implementing Keycloak
To maximize the benefits of Keycloak integrations, consider the following best practices:
Security Considerations
Ensure that Keycloak is configured to meet your organization’s security requirements:
- Enable SSL: Protect data in transit by configuring SSL for all Keycloak endpoints.
- Regular Updates: Keep Keycloak up-to-date to benefit from security patches and new features.
- Audit Logging: Monitor authentication events to detect and respond to suspicious activities.
Optimizing Performance
Performance optimization is key for delivering a smooth user experience:
- Use Caching: Implement caching strategies for user sessions and tokens.
- Load Balancing: Distribute traffic across multiple Keycloak instances.
- Database Optimization: Tune the underlying database for better read/write performance.
Utilizing Professional Services
Consider leveraging platforms like Skycloak – Keycloak on Autopilot to manage and scale your Keycloak clusters efficiently.
Conclusion
Keycloak integrations offer a powerful way for enterprises to unify and secure their identity and access management processes. By leveraging Keycloak’s rich features and adhering to best practices, organizations can enhance security, improve user experiences, and streamline operations.
Want to make the switch but not sure where to start? We can help you integrate, optimize, and customize your Keycloak cluster for great results .