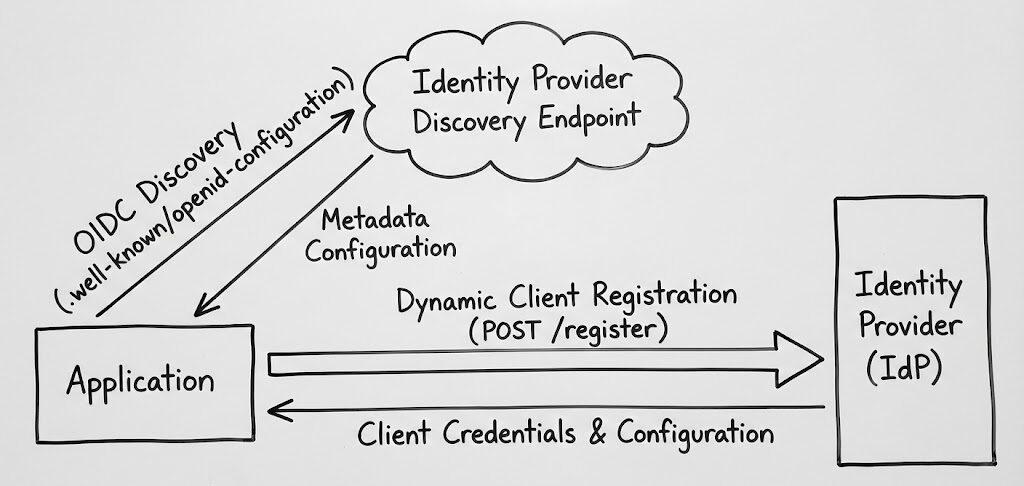
Manual identity provider configuration is time-consuming and error-prone. OpenID Connect (OIDC) Discovery and Dynamic Client Registration automate this process, enabling applications to retrieve configuration details and register programmatically with identity providers. These protocols reduce setup time, improve security, and simplify scaling across environments.
Key Benefits:
- OIDC Discovery: Applications fetch metadata (e.g., endpoints, keys) from a standard URL (
/.well-known/openid-configuration). - Dynamic Client Registration: Applications self-register with identity providers via an HTTP API, receiving client credentials without manual intervention.
- Use Cases: Multi-tenant SaaS platforms, microservices, CI/CD pipelines, and legacy-to-modern integrations.
Challenges:
- Requires robust security controls (e.g., HTTPS, metadata validation, logging).
- Compliance with frameworks like GDPR, SOC 2, and NIST SP 800-63 adds complexity.
- Dynamic registration endpoints must be carefully protected against misuse.
Implementation Tips:
- Start with OIDC Discovery for automated metadata retrieval.
- Test Dynamic Client Registration in controlled environments before production use.
- Enforce strong access controls (e.g., initial access tokens, software statements).
- Use caching for performance but ensure secure storage and periodic refresh.
By automating identity provider configuration, organizations save time, reduce errors, and improve consistency across environments while maintaining security and compliance.
How OIDC Discovery Works: Automated Metadata Retrieval
OIDC Discovery simplifies the process of connecting applications to identity providers by automating the retrieval of configuration details. This standardized mechanism allows applications to gather all necessary information without manual intervention.
The .well-known/openid-configuration Endpoint
Every OpenID Connect (OIDC)-compliant identity provider makes its configuration metadata available at a specific endpoint: https://[identity-provider-domain]/.well-known/openid-configuration. This serves as a centralized resource detailing the provider’s capabilities and endpoints.
The metadata document includes several key configuration parameters:
- Issuer identifier: A unique identifier for the identity provider, used to validate tokens.
- Authorization endpoint: The URL where users are directed to authenticate.
- Token endpoint: The endpoint where authorization codes are exchanged for tokens.
- UserInfo endpoint: The location for retrieving user profile details.
- JWKS URI: The URL for cryptographic keys used to verify token signatures.
- Supported scopes: Lists the permission levels applications can request.
- Supported response types: Options for authentication flows, such as
code,token, orid_token. - Supported grant types: Methods for obtaining tokens, such as authorization code or client credentials.
Applications fetch this information by sending a GET request to the endpoint and receiving a JSON document in response. This process typically happens automatically during application startup or when connecting to a new identity provider. To optimize performance, applications often cache the metadata and refresh it periodically. This automation reduces the effort needed for client-side configuration.
How Discovery Simplifies Client Configuration
OIDC Discovery eliminates the need for hardcoding identity provider details, making configuration more dynamic and adaptable. Applications can connect seamlessly to any OIDC-compliant provider without manual adjustments.
- Environment flexibility: A single application build can function across development, staging, and production environments. The app queries the discovery endpoint for each environment and configures itself automatically.
- Provider adaptability: Organizations can switch identity providers without modifying application code. The app dynamically adjusts to the new provider’s endpoints and capabilities.
- Automatic updates: When identity providers update their endpoints, rotate keys, or change authentication methods, applications automatically receive these updates during the next discovery request.
- Faster integration: Developers save time by avoiding manual configuration. New applications can quickly integrate with existing identity systems without needing extensive setup or documentation.
Security and Compliance Requirements
While OIDC Discovery streamlines configuration, it introduces security considerations that must be addressed to ensure safe and reliable integration.
- HTTPS enforcement: All discovery requests must use HTTPS to protect metadata during transmission. Applications should validate SSL/TLS certificates and reject connections to endpoints that don’t meet current security standards. This prevents man-in-the-middle attacks that could redirect applications to malicious providers.
- Metadata validation: After retrieving the metadata, applications must verify its authenticity. The issuer identifier should match the expected identity provider, and all endpoint URLs must use HTTPS and belong to the same domain as the discovery endpoint. Applications should also confirm that supported authentication methods align with their security policies.
- Certificate pinning: For high-risk environments, applications can pin the SSL certificate or certificate authority of the identity provider. While this adds complexity to certificate lifecycle management, it significantly reduces the risk of attacks involving compromised certificate authorities.
- Audit logging: Logging is critical for both security and compliance. Applications should record all discovery requests, including timestamps, endpoints queried, and validation outcomes. This creates an audit trail that can help identify unusual activity or troubleshoot issues.
- Compliance adherence: Certain regulatory frameworks impose additional requirements for discovery processes. For example, FIPS 140-2 compliance may mandate specific cryptographic algorithms for metadata validation, while SOC 2 audits often review logging and monitoring practices. Healthcare organizations under HIPAA must ensure sensitive information isn’t logged during discovery.
Caching and Security Best Practices
Caching metadata improves performance but introduces its own set of challenges. Applications should encrypt cached metadata at rest and secure it with the same controls used for other sensitive configuration data. Additionally, refresh intervals must be carefully managed to balance performance with the need for up-to-date information. Proper caching practices ensure that stored metadata remains both secure and reliable.
Dynamic Client Registration: Process and Security
Dynamic Client Registration simplifies the way applications integrate with identity providers by allowing them to register automatically, bypassing the need for manual setup. This approach ensures seamless connections between applications and identity systems while adhering to strict security protocols.
Dynamic Registration Protocol Steps
The process of dynamic registration follows a clear workflow, enabling applications to submit their details and receive credentials programmatically. It all starts with the application sending a POST request to the identity provider’s registration endpoint. This endpoint is typically listed in the .well-known/openid-configuration metadata document.
The application provides its metadata in JSON format, which includes details such as redirect URIs, client names, application type, authentication methods for the token endpoint, grant types, and response types.
Once the identity provider receives the registration request, it validates the metadata against its security policies. This includes ensuring the requested grant types are appropriate for the client type and confirming compliance with security requirements. If the metadata passes these checks, the provider generates unique client credentials and sends them back in the response.
The response includes key information for future authentication: the client ID, which serves as the application’s public identifier, and the client secret, used for authenticating confidential clients. Additionally, the response provides a registration access token, allowing the client to manage its registration details (e.g., updates or removal). The provider may also return an adjusted version of the submitted metadata, reflecting any changes made during validation.
Next, we’ll examine the security measures that protect this dynamic process.
Security Controls for Dynamic Registration
To ensure secure operations, identity providers implement various mechanisms to validate client authenticity and restrict registration access to authorized applications.
- Initial access tokens act as the first line of defense. These tokens must be presented by the client before registration is allowed. Organizations distribute these tokens securely, often limiting their scope to control which applications can register and the types of grant requests they can make.
- Software statements provide cryptographic proof of a client’s authenticity. These are JSON Web Tokens (JWTs) signed by a trusted software publisher, containing verified metadata about the client application. When presented during registration, the identity provider verifies the signature and trusts the metadata without additional checks. This method is especially useful in federated environments where multiple organizations need to establish trust.
- Authentication methods vary based on the client type. Confidential clients, such as server-side applications, receive client secrets and authenticate using methods like HTTP Basic authentication or JWT-based assertions. Public clients, like mobile or single-page applications, cannot store secrets securely and rely on mechanisms like Proof Key for Code Exchange (PKCE) for added security.
- Registration policies enable identity providers to enforce specific security rules automatically. These policies can restrict redirect URIs to approved domains, limit grant types based on client type, or require additional approval workflows for certain requests. Advanced implementations may integrate external systems to verify client legitimacy or enforce custom rules.
Meeting Compliance and Privacy Requirements
Dynamic registration must also align with compliance and privacy standards, which shape how data is handled and logged during the process. Frameworks like GDPR, SOC 2, and NIST SP 800-63 influence these requirements.
- GDPR compliance emphasizes the careful handling of personal data. While client metadata rarely includes personal information, details like client names or contact information must follow data protection principles. Privacy notices should be provided when collecting identifiable data, and mechanisms must be in place for updating or deleting such information.
- SOC 2 audits focus on the security of the registration process. Auditors assess access controls for initial access tokens, logging of registration activities, and how client credentials are stored securely. Organizations must demonstrate that registration endpoints are protected, failed registration attempts are monitored, and client secrets are encrypted properly.
- NIST SP 800-63 offers guidance on identity verification and authentication. It helps organizations assess risks tied to compromised client registrations and determine appropriate security measures. High-risk environments might require stronger authentication methods or stricter registration policies.
- Audit logging is essential for compliance. Logs should capture registration requests, including metadata, timestamps, source IPs, and validation results. Failed attempts deserve special attention as they could signal malicious activity. Log retention periods should meet regulatory requirements, often ranging from one to seven years.
Regional data residency requirements must also be considered, especially when using managed identity services that may store data across multiple locations. Organizations should ensure compliance with local regulations regarding where registration data is stored.
Lastly, managing the client lifecycle is vital for maintaining compliance. This includes updating registration details as business needs evolve and deactivating registrations for decommissioned applications. Regular audits of registered clients help identify unused or orphaned registrations that could pose security risks.
Implementation Approaches and Architecture Options
Building on the security principles of dynamic registration, this section explores various deployment models and configuration strategies. Organizations face key architectural decisions when implementing OIDC Discovery and Dynamic Registration. These decisions depend on factors such as security needs, operational complexity, and available resources. By understanding the options, teams can choose the best implementation strategy for their environment.
Self-Hosted vs Managed IAM Solutions
Self-hosted identity providers offer organizations complete control over OIDC protocols. In this model, teams manage everything – from server setup to applying security updates. This approach allows for extensive customization of metadata and registration policies. Teams can implement tailored security controls, adjust registration workflows, and integrate seamlessly with existing systems.
However, this level of control requires skilled personnel with expertise in identity protocols and infrastructure management. On the upside, self-hosting ensures that data stays within the organization, which can be crucial for meeting compliance requirements.
Managed IAM services, on the other hand, take care of the infrastructure and protocol implementation. Organizations can focus on configuring their systems without worrying about maintenance. These services often include built-in OIDC Discovery endpoints and standardized Dynamic Registration capabilities. Updates and security patches are handled automatically, reducing the operational burden.
The trade-off with managed services is a loss of flexibility. Organizations must work within the constraints of the service provider’s features, which may limit customization of registration workflows or discovery metadata. Additionally, data residency becomes a key consideration, especially for organizations with strict compliance mandates.
Hybrid approaches combine elements of both models. For example, an organization might use a managed service for general OIDC functionality while maintaining self-hosted components for specialized needs. This approach balances efficiency with customization but adds complexity to the system.
Next, we’ll examine how different integration patterns meet the unique demands of various environments.
Integration Patterns for Different Environments
Multi-tenant environments demand careful handling of tenant isolation in OIDC Discovery and Dynamic Registration. Each tenant typically requires its own discovery endpoints and registration policies. The discovery metadata must reflect tenant-specific configurations, including unique authorization and token endpoints as well as supported features.
In such setups, tenant-aware initial access tokens play a critical role. These tokens ensure that applications register in the correct tenant context and adhere to the appropriate policies. The registration process then returns tenant-specific client identifiers and configuration details, which are essential for subsequent authentication requests.
Federated environments bring their own set of challenges. Here, multiple identity providers must coordinate discovery metadata and registration policies across organizational boundaries. Trust relationships between providers determine how registration requests are validated and what security measures are applied.
In cross-domain registration scenarios, managing redirect URIs and trust boundaries becomes crucial. Software statements, which provide cryptographic proof of application authenticity, are especially valuable in these contexts. The discovery process must help applications navigate multiple providers and identify the correct one for specific authentication scenarios.
Microservices architectures benefit greatly from automated OIDC configuration. As services scale up or down, they can dynamically discover identity provider capabilities and register themselves. This eliminates the need for manual configuration, which can otherwise slow down deployment.
In service mesh environments, automated OIDC Discovery and Dynamic Registration enable ephemeral services to function efficiently. By caching discovery metadata and automating credential issuance, these processes support auto-scaling and short-lived workloads. The registration system must also handle automatic cleanup of unused credentials to maintain security and efficiency.
Edge computing scenarios introduce challenges like latency and intermittent connectivity. To address these issues, discovery metadata can be cached at edge locations, improving response times. Registration processes must account for unreliable connectivity and include fallback mechanisms for when central identity providers are unreachable.
These scenarios highlight the importance of comparing manual and automated configuration approaches.
Manual vs Automated Configuration Comparison
| Aspect | Manual Configuration | Automated Configuration |
|---|---|---|
| Setup Time | Hours to days per application | Minutes with proper automation |
| Error Rate | High due to human errors | Low with validated processes |
| Scalability | Limited by administrative capacity | Scales with infrastructure |
| Consistency | Varies across applications | Standardized through automation |
| Maintenance Overhead | Requires manual updates for endpoint changes | Automatic updates through discovery |
| Security Posture | Risk of outdated configurations | Dynamic credential management |
| Compliance Tracking | Manual audit trails | Automated logging and audits |
| Environment Sync | Prone to configuration drift | Consistent across environments |
| Rollback Capability | Complex manual process | Automated rollback via infrastructure as code |
| Cost Structure | High ongoing maintenance costs | Lower ongoing costs after initial setup |
The table illustrates how automation offers clear advantages, especially in environments with many applications or frequent changes. While manual configuration might work for small-scale, stable deployments, automation becomes crucial as complexity grows.
Deployment models also influence the choice between manual and automated approaches. Containerized environments align naturally with automation, as containers can include discovery and registration logic during startup. Traditional server setups may require more manual steps, though automation tools can help bridge the gap.
Change management processes differ significantly between the two approaches. Manual configuration involves coordination across teams, updating documentation, and thorough testing in multiple environments. Automated configuration, while requiring robust testing of scripts and discovery logic, enables faster iteration cycles and reduces coordination overhead.
Implementation Best Practices
Building on the deployment strategies already discussed, adhering to certain best practices can ensure both secure and efficient implementations. When working with OIDC Discovery and Dynamic Registration, a meticulous approach to security and operational procedures is essential. By following specific technical guidelines and establishing robust monitoring mechanisms, organizations can create a secure and scalable framework for identity automation. Below are key practices to consider for both initial setup and ongoing oversight.
Technical Implementation Guidelines
- Use HTTPS for all endpoints: This ensures metadata is transmitted securely and prevents interception or tampering.
- Validate discovery documents and metadata: Always confirm that configuration details and endpoint URLs are accurate and trustworthy.
- Enforce strong access controls: Require initial access tokens for registration endpoints and use short-lived registration access tokens, ensuring these tokens are stored securely.
- Implement robust error handling: Provide clear, secure feedback for registration failures and maintain detailed logs for troubleshooting and analysis.
Monitoring and Auditing Requirements
Effective monitoring not only strengthens security but also ensures that automated identity configurations remain consistent and compliant over time.
- Comprehensive logging: Track all activities related to dynamic client registration, including successful registrations, failed attempts, and client de-registrations.
- Automated cleanup processes: Regularly identify and revoke inactive or unused dynamically registered clients to maintain a clean and secure environment.
- Centralized client registry: Maintain a single registry to monitor the lifecycle and usage of all registered clients, providing better control and oversight.
Key Takeaways for Automating IdP Configuration
Building on the earlier discussions of technical, security, and integration strategies, these takeaways outline a practical roadmap for automating identity provider (IdP) configuration. By leveraging OIDC Discovery and Dynamic Registration, organizations can transition from manual, error-prone processes to automated, scalable identity setups. This shift not only reduces operational burdens but also strengthens security – a critical need in environments managing dozens or even hundreds of client applications across varied deployment scenarios.
Main Benefits and Challenges
The automation enabled by OIDC Discovery and Dynamic Registration brings notable operational improvements, enhancing both development efficiency and security. Many organizations adopting these protocols report fewer configuration errors, quicker onboarding of applications, and consistent identity management across their infrastructure.
One of the most immediate advantages is a reduction in manual effort. Instead of manually configuring endpoints, scopes, and keys, discovery mechanisms automate these tasks, saving time and reducing human error.
Scalability is another key benefit, especially in microservices and cloud-native architectures where applications need to scale dynamically. Dynamic registration allows applications to register themselves automatically, making it possible to handle elastic scaling patterns that would be cumbersome with manual workflows.
However, automation doesn’t come without challenges. Dynamic registration endpoints can become targets for attacks, making robust access controls and continuous monitoring essential.
Additionally, compliance requirements introduce further complexities. Organizations must implement enhanced logging and monitoring to meet regulatory standards, ensuring they can trace and audit identity-related activities effectively.
Getting Started with Implementation
To maximize the benefits of automation while minimizing risks, it’s best to adopt a phased approach. Start with OIDC Discovery before moving to dynamic registration. Discovery offers immediate advantages with relatively low risk, as it primarily involves consuming publicly available metadata rather than exposing new endpoints.
Begin by identifying applications that currently rely on manual endpoint updates. These are ideal candidates for discovery, as automated metadata retrieval can immediately streamline their configuration process.
Ensure your IAM infrastructure supports the necessary endpoints and protocols. While most modern identity providers include discovery capabilities, older systems may require updates or additional configuration to expose metadata endpoints.
Establish robust logging and governance policies from the outset. This proactive step ensures you can detect anomalies or security issues early on. Setting baselines for normal behavior will make it easier to spot irregularities later.
For dynamic registration, start small by testing in controlled pilot environments. This allows you to validate the registration lifecycle without risking disruptions to production systems. Focus initially on applications with predictable scaling needs, then expand to more complex use cases.
Finally, evaluate the integration patterns that align best with your existing architecture. For example, organizations using service mesh implementations might approach automation differently than those relying on traditional load balancers or API gateways. The goal is to ensure that automated identity configuration integrates seamlessly with your broader infrastructure strategies. By taking these incremental steps, organizations can confidently embrace automation while maintaining security and compliance.
FAQs
How does OIDC Discovery improve security when integrating applications with identity providers?
OIDC Discovery enhances security by automating the process of fetching configuration details directly from an identity provider’s metadata. This approach ensures that applications consistently use current and verified endpoints, public keys, and supported features, significantly lowering the chances of misconfigurations or reliance on outdated settings.
By establishing a standardized method for applications to locate and connect with identity providers, OIDC Discovery reduces the likelihood of manual errors. It also ensures secure and reliable communication between systems. This streamlined mechanism supports seamless interoperability while aligning with established security practices in identity and access management.
What are the risks of using Dynamic Client Registration (DCR), and how can they be addressed?
Dynamic Client Registration (DCR) comes with its own set of challenges, including uncontrolled database growth, client impersonation, denial-of-service (DoS) risks, and poorly managed client lifecycles. On top of that, failing to properly validate client metadata can open the door to security vulnerabilities or operational issues.
To tackle these issues effectively, consider implementing multi-layered verification processes, ensuring thorough validation of all client metadata, and developing workflows specifically designed for different types of clients. Leveraging structured solutions, such as Client ID Metadata Documents (CIMD), can further enhance control and security during client registration. Adopting these strategies will help minimize risks while supporting a scalable and secure approach to DCR.
How can organizations meet compliance requirements like GDPR and SOC 2 when using OIDC Discovery and Dynamic Registration?
Organizations can address compliance requirements like GDPR and SOC 2 by incorporating OIDC Discovery and Dynamic Registration while prioritizing security and privacy best practices. These features streamline the configuration of Identity Providers (IdPs) through automation, reducing the likelihood of human errors and supporting adherence to established security protocols.
For GDPR compliance, it’s critical to minimize the personal data processed during identity federation, ensure encryption is applied to sensitive information, and handle the data transparently. Meanwhile, achieving SOC 2 compliance involves implementing secure logging, continuous monitoring, and strict access controls throughout the OIDC workflow. Your Identity and Access Management (IAM) system should also support detailed audit trails, ensuring alignment with your organization’s overall compliance strategy.
By embracing OIDC’s open standards and implementing strong security practices, organizations can simplify identity federation processes while meeting regulatory requirements effectively.