Introduction
In this article, we discuss how to restrict administrative access to a Skycloak cluster. Skycloak is a fully managed Keycloak platform hosted in the cloud.
Using Skycloak allows organizations to harness the powerful features of the open-source Keycloak IAM product while avoiding the challenges of installing, maintaining, and scaling Keycloak for production-grade environments — all in a cost-effective way.
Skycloak provides enterprise-grade security controls such as Web Application Firewall (WAF), geo-blocking, IP access control, rate limiting, and more.
In this article, we specifically focus on IP or CIDR-based whitelisting to allow only trusted IP addresses to access the Keycloak administration interface.
Overview
Organizations often do not want their Keycloak administrative console (/admin/*) to be publicly accessible. Administrators typically prefer to allow access only from trusted office networks, VPN ranges, or known administrator IP addresses.
Let us see how IP-based whitelisting can be configured for Skycloak.
Steps to Whitelist Access to Keycloak Admin Console
Step 1: Log in to Skycloak Console
Navigate to your cluster dashboard
Step 2: Open Security Configuration
From the left navigation panel, select
Your Cluster -> Security
Here you will find options to enable or configure:
- Web Application Firewall (WAF)
- Geo-blocking
- IP Access Control
- Rate Limiting
Step 3: Enable IP Access Control
Enable IP Access Control for IP access restrictions.
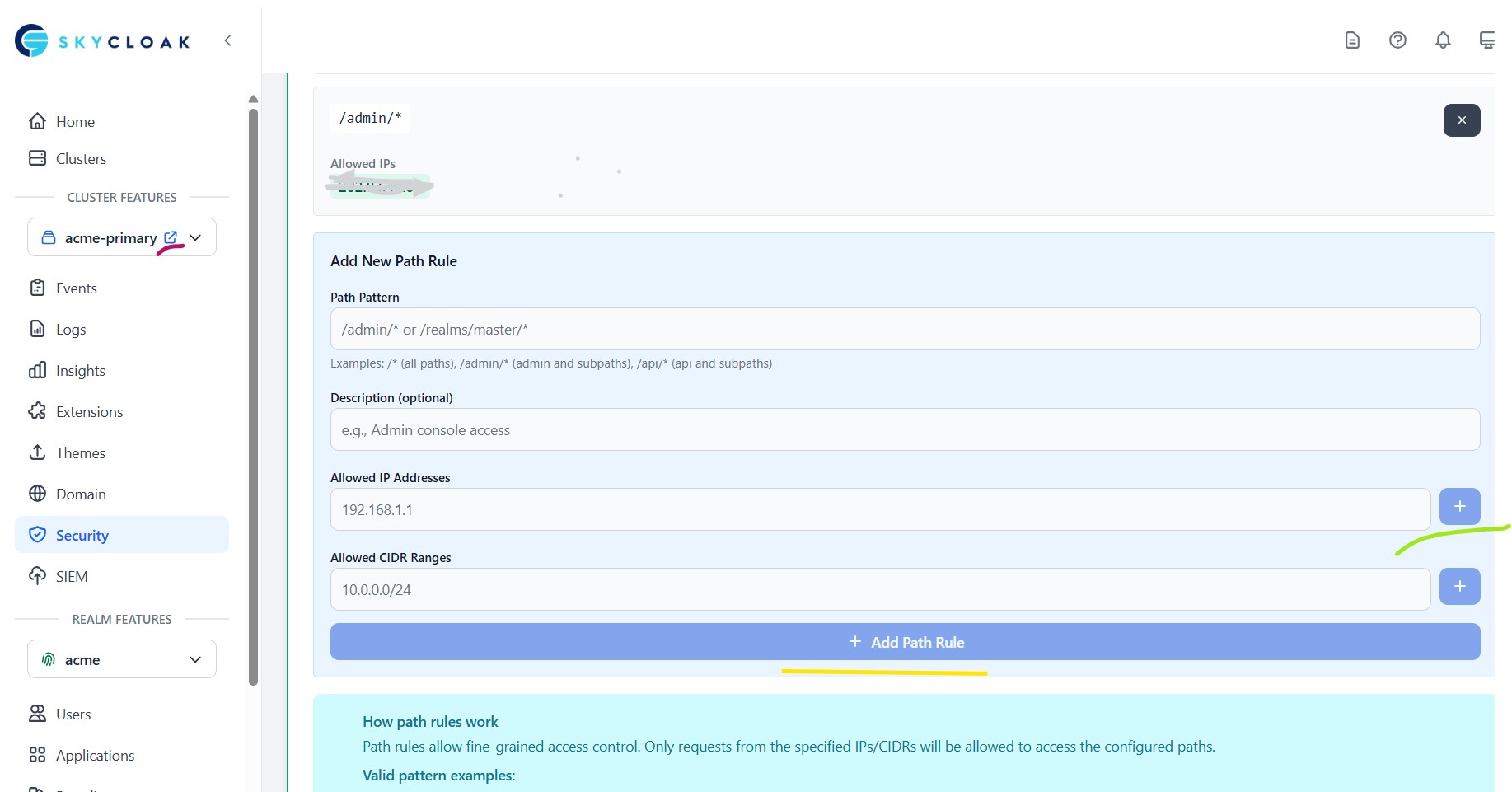
Step 4: Configure Path-Specific Access Rule
Add New Path rule
- Path Pattern /admin/*
- Allowed IP Addresses: For testing, enter
1.2.3.4 - Click the ‘+’ button to the right of Allow IP Address to add this ip address
- Select Add Path Rule
At this point, only IP 1.2.3.4 can access the /admin/* URLs of your Keycloak instance.
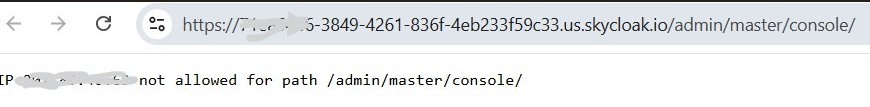
You can now test by accessing the Keycloak admin console from a machine not having this IP — you should see an IP Not Allowed message.
Note: Following screenshot is from a cluster domain where custom domain is not enabled.
Validation
Next, repeat the above steps but enter your actual IP address in the Allowed IP field.
Once saved, your system should now be able to access the admin console.
Summary
In this article, we configured path-based IP whitelisting to restrict access to the /admin/* URLs of a Skycloak cluster. This ensures that only trusted users from approved networks can access the Keycloak admin interface.
You may now delete the first entry (1.2.3.4) and replace it with actual production-grade IPs or CIDR ranges.
Skycloak provides production-ready managed Keycloak hosting, helping teams avoid the complexity of maintaining and scaling Keycloak themselves.
If you’re new to Skycloak, visit the Skycloak Getting Started Guide to learn more.