Introduction
Earlier, in this article, we discussed how to configure Keycloak as a SAML Service Provider (SP) and Okta as a SAML Identity Provider (IDP). This article extends that configuration and demonstrates how to map user attributes sent from Okta into Keycloak.
Attribute mapping ensures Keycloak correctly identifies and provisions authenticated users by capturing key fields such as email, first name, and last name
Configuration Steps
To map attributes, you must configure:
- Attribute settings in the Okta SAML application
- Attribute mapping in Keycloak
For more details on Keycloak as an Identity Broker, you may refer Keycloak server admin guide.
Step 1: Configure Attributes for Keycloak in Okta
- Navigate to Okta Developer Console.
- Go to Applications -> Your Keycloak SAML App (created in the previous article, named
kc-client). - Open the General tab and click Edit under SAML Setting
- Proceed to the Configure SAML Settings page.
- Add the attribute statements for:
- firstName
- lastName
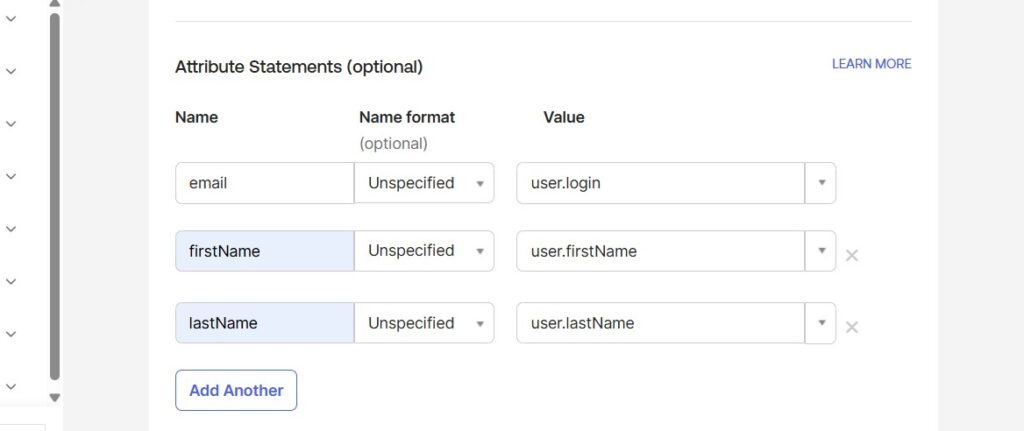
Note on Email Attribute
Here, we map the Okta username as the email value. By default, Okta usernames are email-formatted and unique, while Okta’s primary email field may not always be unique across all user records. Since Keycloak requires emails to be unique across users, mapping the username is safer and consistent.
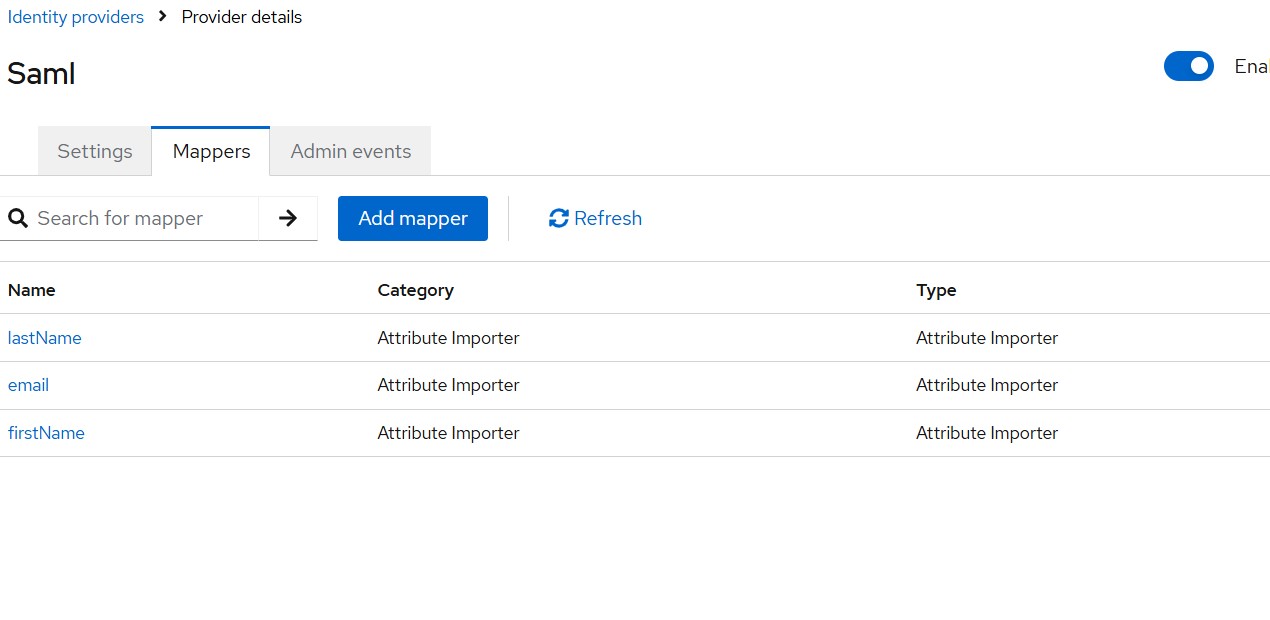
Step 2: Add Attribute Mappings in Keycloak
Now configure Keycloak:
- Open Keycloak Admin Console Identity Providers -> Okta
- Locate the SAML dialog
- Open Mappers → Add Mapper
- Create individual mappers for:
- firstName
- lastName
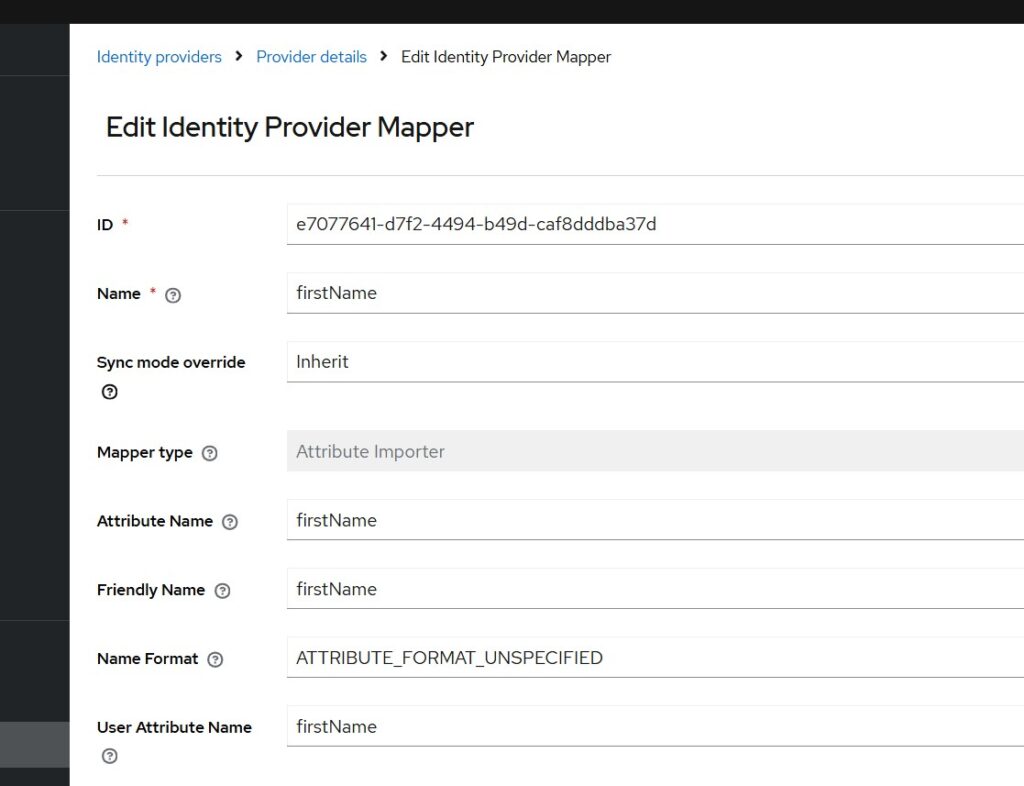
You may refer to the screenshot provided below showing sample configuration for firstName.
Testing the Integration
- Access your Keycloak Account Console: https://skycloak_hostname>/realms/<your_realm_name>/account or launch a protected application.
- Click Sign in with Okta
- Authenticate in Okta
- Keycloak will automatically create (or update) a local user record with mapped attributes
Validating Using SAML Debugger
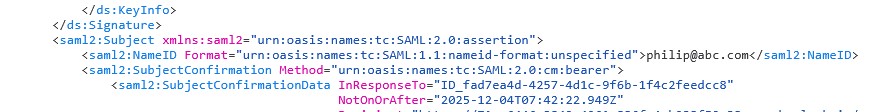
Using Firefox with the SAML Tracer extension:
- Inspect the SAML Response
- You will see attribute statements matching:
- firstName
- LastName
- The SAML NameID field will also be visible for reference
Screenshots referenced earlier will illustrate these payloads.

Summary
In this article, we covered:
- How to configure attribute statements for Keycloak within Okta
- How to map those attributes inside Keycloak
We used Skycloak, a fully managed Keycloak hosting solution, for demonstration.
Skycloak provides production-ready managed Keycloak hosting, helping teams avoid the complexity of maintaining and scaling Keycloak themselves.
If you’re new to Skycloak, visit the Skycloak Getting Started Guide to learn more.