Introduction
In this article, we discuss the Syslog feature in Skycloak.
Skycloak is a fully managed Keycloak platform hosted in the cloud. It enables organizations to leverage the powerful capabilities of the open-source Keycloak Identity and Access Management (IAM) solution without the operational overhead of installing, maintaining, and scaling Keycloak for production-grade environments. All of this is delivered in a secure and cost-effective manner.
By using Syslog, customers can improve observability, integrate Skycloak with external SIEM platforms, and optionally configure alerting mechanisms.
SIEM integration options supported by Skycloak
Skycloak currently supports the following SIEM integration mechanisms:
- Syslogs
- HTTP Webhooks
- More suitable when SIEM is SaaS (Splunk HEC, Datadog etc.)
- Useful when firewall rules block Syslog traffic
- AWS S3
In this article, we focus specifically on Syslog-based integration.
Log types supported by Skycloak
Skycloak supports sending the following telemetry types.
For each type, a separate SIEM configuration can be created if required.
Skycloak supports sending the following details and we have to choose one among the following. Multiple SIEM configurations can be setup at Skycloak for each desired type.
- Keycloak Events
- Authentication events, user registration, password resets, and other Keycloak security events
- Application Logs
- Keycloak server logs including errors, warnings, and debug information
- Security Logs
- Security-related events such as:
- WAF events
- Geo-blocking
- Rate limiting
- Other security controls
In this article we focus on Security Logs
Syslog receiver
To receive Syslog messages from Skycloak, we need a Syslog receiver / agent, such as:
- rsyslog
- syslog-ng
- Fluentd
- Fluent Bit
For this proof of concept (POC), we will use rsyslog.
For more details on the Syslog protocol, please refer the link over here.
Supported Syslog transport protocols
Skycloak supports sending Syslog messages using the following transport protocols:
- UDP
- TCP
- TLS
For this article, we use TCP, which means the data is transmitted without encryption.
Note: In production environments, TLS should always be used to ensure encrypted and secure transmission of logs.
Configuration Steps
Configuring rsyslog on Linux – Ubuntu (TCP)
Note: For production setups, TLS is strongly recommended.
Step 1: Install rsyslog
sudo apt update
sudo apt install rsyslog -y
Step 2: Enable TCP Syslog input
Edit the rsyslog configuration file:
sudo nano /etc/rsyslog.conf
Uncomment or add the following lines:
module(load="imtcp")
input(type="imtcp" port="514")
Step 3: Create a Skycloak-specific log file
Create a configuration file:
sudo nano /etc/rsyslog.d/30-skycloak.conf
Add the following:
if $fromhost-ip != '127.0.0.1' then /var/log/skycloak.log
& stop
This configuration:
- Captures incoming remote Syslog messages
- Writes them to
/var/log/skycloak.log
Step 4: Restart rsyslog
sudo systemctl restart rsyslog
sudo systemctl status rsyslog
Step 5: Verify the listener
sudo ss -lntp | grep 514
You should see rsyslog listening on TCP 514.
Configuring Skycloak SIEM destination
Navigate to:
Skycloak Console -> SIEM-> Add Destination
Configuration steps
Review the configuration and click Complete Setup.
Destination Name
Specify a meaningful name.
Destination Type
Select Syslog (UDP / TCP / TLS)
Click Continue.
Syslog configuration
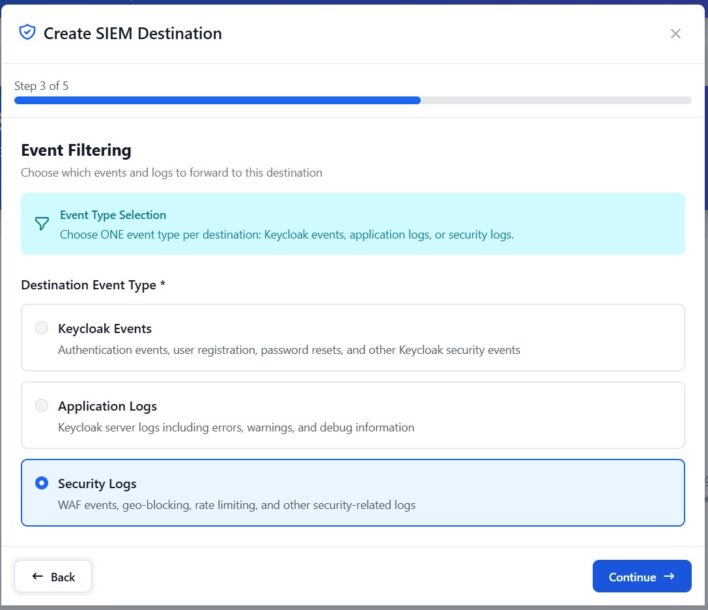
Event Type Selection
Select Security Logs
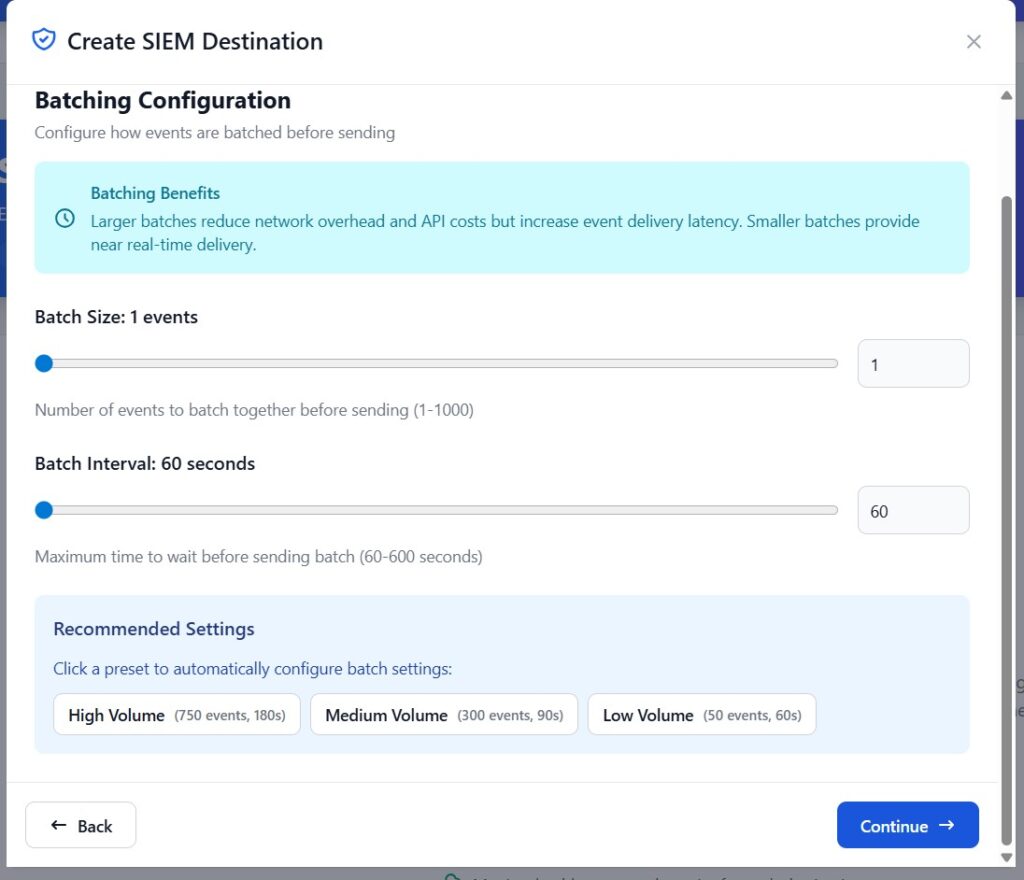
Batching Configuration
Choose an appropriate batch size and interval
(For this POC, the lowest values were selected.)
Testing the Implementation
We validate the setup using the following test scenarios:
- Simulate an XSS attack using curl
- For more details, please refer the blog over here
- Test Geo-blocking
- For more details, please refer the blog over here
IF you simulate these security attacks, in addition to logs on Security-> logs , you will find that your configured SIEM has sent the data to the listener.
When these security events are triggered:
- They appear under Security -> Logs in Skycloak
- Security logs are forwarded to the configured Syslog destination
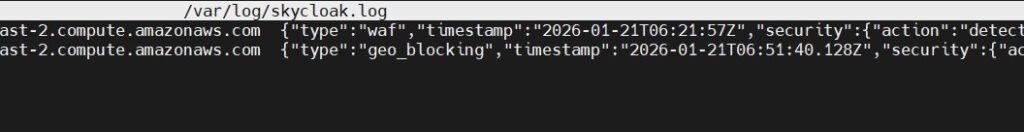
Sample output
Contents of /var/log/skycloak.log after executing the test scenarios: (two test cases)
What we have implemented can be further extended to integrate with Elastic Stack or other SIEM/log analytics platforms, preferably by routing logs through Fluent Bit or Fluentd for parsing, buffering, and reliable delivery.
Note: rsyslog is used here primarily as a PoC and lightweight log relay. In production-grade, cloud-native setups, logs can be sent directly to Fluent Bit or Fluentd. Using rsyslog in this approach provides the additional advantage of maintaining local backup copies of logs on the system, which can be useful for auditing and troubleshooting.
Summary
In this article, we explored how to configure Syslog-based SIEM integration in Skycloak and demonstrated receiving Security Logs using rsyslog over TCP.
In future articles, we will:
- Integrate with Elastic Stack or another SIEM/log analytics platform for visualization and alerting. (POC)
- Explore additional log streams (events and application logs)
- Configure direct ingestion into Fluent Bit / Fluentd
If you’re new to Skycloak, visit the Skycloak Getting Started Guide to learn more and securing your Keycloak deployments.